Maximizing IDOR Detection with Burp Suite’s Autorize

Reading Time: 7 Minutes
Introduction
Despite being in the Top 10 OWASP for several years, Insecure Direct Object Reference (IDOR) vulnerabilities continue to be prevalent in web applications, particularly in APIs.
This raises the question:
What tools can we use to efficiently detect IDOR vulnerabilities and take our discovery process to the next level?
One such tool is the Autorize extension for Burp Suite. However, to truly understand the significance of Autorize and its role in detecting IDOR vulnerabilities, it’s crucial to first have a comprehensive understanding of IDORs themselves.
IDOR
Insecure Direct Object Reference (IDOR) is a type of security vulnerability that can occur in web applications. This vulnerability arises when an application’s access control mechanisms are improperly implemented or bypassed, allowing an attacker to access or manipulate resources or data that should be restricted.
For a more comprehensive examination of access control vulnerabilities, please refer to this write-up.
The vulnerability is known as “direct object reference” because it refers to a direct reference to an internal object or resource, such as a database record, file, or URL. In a web application, these objects are typically referenced using an identifier or parameter in the URL.
For example, suppose a web application uses an ID parameter in the URL to retrieve information about a specific user profile, like “https://example.com/user?id=123“. If the application fails to properly authenticate and authorize the user requesting the information, the attacker could modify the ID parameter in the URL to access another user’s profile or unauthorized resources.
IDOR vulnerabilities can be challenging to detect, as they often require manual testing and manipulation of requests to identify instances where access controls are improperly implemented. Attackers can exploit these vulnerabilities to gain access to sensitive data, resources, or functionality that should be restricted, potentially leading to data breaches or other security incidents.
Leveraging Burp Suite extension for finding IDORs
Autorize is a powerful extension for Burp Suite that streamlines the testing process for access control in web applications.
Autorize is an extension for Burp Suite that facilitates automatic authorization enforcement detection. Developed by Barak Tawily, a recognized expert in application security, the extension is implemented in Python.
With minimal setup required, the extension facilitates the testing of proper access control and authorization by forwarding session cookies for a low-privileged user and omitting session cookies in requests.
By automating the testing process, Autorize can save security testers a significant amount of time and effort while also ensuring thorough and accurate testing of access controls. This extension makes it easier to identify vulnerabilities such as IDOR and can help to enhance the overall security of web applications.
Through the use of Autorize, security testers can gain deeper insights into the access control mechanisms of web applications and identify potential vulnerabilities in a more efficient and effective manner. As web application security becomes increasingly important in today’s digital landscape, tools like Autorize can be invaluable in helping organizations to maintain a strong security posture and protect sensitive data and resources.
See Also: So you want to be a hacker?
Offensive Security Courses
How Autorize works
It is sufficient to give the extension the cookies of a low-privileged user, and navigate the website with a high-privileged user. The extension automatically repeats every request with the session of the low privileged user and detects authorization vulnerabilities.
It is also possible to repeat every request without any cookies in order to detect authentication vulnerabilities in addition to authorization ones.
The plugin works without any configuration, but is also highly customizable, allowing configuration of the granularity of the authorization enforcement conditions and also which requests the plugin must test and which not.
It is possible to save the state of the plugin and to export a report of the authorization tests in HTML or in CSV.
Authorization Enforcement Status
Autorize has 3 enforcement statuses.
- Authorization bypass! – Red color – endpoint could be vulnerable to IDOR,
- Authorization enforced! – Green color – endpoint is clearly protected against IDOR
- Authorization enforced??? (please configure enforcement detector) – Yellow color

When Autorize encounters the third status(Authorization enforced??? ), it indicates that the extension is unable to determine whether authorization is enforced or not. In such cases, the user is prompted to configure a filter in the enforcement detector tab.
These enforcement detector filters enable Autorize to detect authorization enforcement by fingerprint (string in the message body) or content length in the server’s response. For example, if a request enforcement status is detected as “Authorization enforced??? (please configure enforcement detector),” it is possible to examine the modified/original response and observe that the modified response body includes the string “You are not authorized to perform action.” By adding a filter with the fingerprint value “You are not authorized to perform action,” Autorize will search for this fingerprint and automatically detect that authorization is enforced. It is also possible to define a content length filter in a similar manner.
In summary, the enforcement detector filters of Autorize provide a mechanism to detect authorization enforcement in cases where the extension cannot automatically determine the status. By configuring these filters, users can significantly enhance the efficiency and effectiveness of their access control testing efforts.
Installation
*Jython is needed for using Python based addons in Burp like Autorize.
- Download Jython standalone https://www.jython.org/download
- Open Burp and navigate to the Extensions tab (older versions, Extender tab), click on Extension settings (or options for older versions), then in the Python environment section, choose the Jython standalone JAR

- Then, navigate to the BApp Store subtab in the Extensions tab
- Click on BApp Store, search for Autorize, and scroll down on the right-side panel to click install.

- Upon installation, you should see the new tab (Autorize) at the top.

Trending: Offensive Security Tool: Go365
How to use it to find IDORs easily
- The tests will be performed using OWAP’s vulnerable app Juice shop. Website Link:
- https://juice-shop.herokuapp.com/
- A low privilege user is already created
- Admin account creds: [email protected]/admin123
- Input the header details (the Authorization bearer token header and the JWT token used in the cookie header) of the low-privileged/different user into the Autorize extension.


Add “scope items only” interception header:
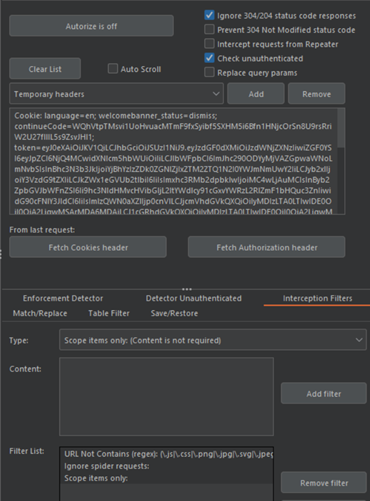
2. Log in to the vulnerable website using a high-privileged account and access different resources while Burp is connected to your browser.
3. Each time you make a request to the website using the high-privileged account, the Autorize extension will automatically repeat the same request using the low-privileged cookie.
4. Check the Autorize extension to see if any privileged resources were accessed using the low-privileged cookie requests. If so, an IDOR vulnerability is present.
Results:

As seen by the screenshot above we did get all the enforcement statuses.
The first column (Authz. Status), shows the request that’s been made as a modified user, and the second column (Unauth. Status) shows the request that’s been made as an authenticated user.
Clicking on any request in the Autorize tab will show on the right side of the panel:
- Modified Request
- Original Request
- Unauthenticated Request

Examining the results
- “Is enforced???” status could be a result of the original’s request size being not the same as the modified one (you can check each of the responses in the tabs to see why is that). This is maybe caused by the fact that this function could be called by any type of user.
- Authorization bypass status on the …/basket/1 endpoint indicates that it may be vulnerable to IDOR since the responses are exactly the same. Meaning that an attacker can see the basket of another user.
- You can validate the finding by sending the modified request to the repeater and manipulating the endpoint to something else than 1.
You can see below that we can access the basket of another user.

Trending: Offensive Security Tool: dontgo403
Some useful tips for Autorize
Utilization of Interception filters:
- Just like we showed in the example, you can limit the results to Scope items only from the Interception filters tab because most of the web applications do have out-of-scope APIs and services that may run when performing actions on the website (especially useful for Bug bounty targets as the scope is limited)
- Another useful filter is the “URL Not Contains(regex)”, and “URL Not Contains (simple string)” to filter out URLs that contain certain strings or we can utilize regex if you want to also with the same results.
g., we could filter the responses in our example above by filtering out socket.io with “URL Not Contains (simple string)”, adding socket.io in the content field, and clicking add s filter. - You can also do the opposite of what we did above with “URL Contains(regex)”, and “URL Contains (simple string)” if you want to only check examples with specific regex or strings.
e.g. we could filter the responses on our example to only check the API of the web application by filtering only results with “.+/api/.+” with “URL Contains(regex)”, adding “.+/api/.+” in the content field and clicking add a filter.
- You can also apply the same logic by filtering Response bodies and HTTP methods.
Utilization of extra extensions/plugins
- Using Autorize with the PwnFox, a Firefox extension, and a Burp plugin. The PwnFox extension can help you proxy your web browser with Burp allowing you to create up to 8 different containers. The Burp plugin adds an option to highlight your requests beautifully in Burp Suite. It can also provide colors to match your different container sessions, which helps you keep track of different testing segments efficiently.
Not a silver bullet
While Burp Suite’s Autorize tool can be a useful starting point for identifying IDOR vulnerabilities, it is important to note that it is not a silver bullet solution. There are a number of other techniques and tools that can be used to efficiently detect IDOR vulnerabilities and take the discovery process to the next level.
Here are some tips for efficient IDOR discovery:
Manual testing
While Autorize can be helpful, it is important to also manually test the application for IDOR vulnerabilities. This can involve manipulating URLs and parameters to try to access unauthorized data or functionality.
Fuzzer
A fuzzer is a tool that can automatically generate and test a large number of requests with different input values. This can help to identify hidden IDOR vulnerabilities that may not be immediately obvious.
Analyze the source code
Analyzing the application’s source code can help to identify potential IDOR vulnerabilities that may not be immediately visible in the web interface. This can involve reviewing the code for direct object references and looking for places where user input is used to access sensitive data.
Use a proxy
A proxy tool like Burp Suite can be used to intercept and modify requests and responses, which can be helpful for identifying IDOR vulnerabilities. In addition to Autorize, Burp Suite’s other tools like Repeater, Intruder, and Scanner can also be used to identify and test IDOR vulnerabilities.
Understand the application’s logic
Understanding how the application works and the relationships between different objects and data can help to identify potential IDOR vulnerabilities. This can involve mapping out the application’s data flow and identifying areas where user input is used to access sensitive data.
Test different user roles
Different user roles may have different levels of access to data and functionality within the application. Testing the application from the perspective of different user roles can help to identify IDOR vulnerabilities that may only be visible to certain users.
By using a combination of these techniques and tools, it is possible to efficiently detect IDOR vulnerabilities and take the discovery process to the next level. However, it is important to remember that IDOR vulnerabilities can be complex and difficult to identify, so it is important to use a thorough and systematic approach to testing and discovery.
Final Thoughts
Ultimately, IDOR vulnerabilities can be extremely damaging to the security of web applications, as they allow attackers to access sensitive data or perform unauthorized actions. The use of a tool like Burp Suite can be highly effective in detecting and exploiting IDOR vulnerabilities, making it an essential part of any security testing toolkit. Developers should take steps to prevent IDOR vulnerabilities in the first place, such as implementing strict access controls and using unique identifiers for each resource. We can work towards a safer and more secure online world by staying vigilant and proactive in our security practices.
See Also: Write up: Exploiting LFI Vulnerabilities
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to Information Security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]