Atomic macOS Stealer Evolves – New Variant Enables Remote Control and Reboot Persistence

A Stealth Upgrade: AMOS Now Comes with Full Remote Access
Security researchers have discovered a dangerous new version of the Atomic macOS Stealer (AMOS) that includes a built-in backdoor, allowing attackers to maintain persistent access to infected Apple devices.
The malware, which already targeted sensitive user data like browser credentials and crypto wallets, now enables attackers to execute remote commands, survive system reboots, and retain control indefinitely.
Global Spread Confirmed by Analysts
The discovery was made by Moonlock, the cybersecurity division of MacPaw, following a tip from independent malware analyst g0njxa, who specializes in monitoring infostealers. Moonlock’s findings reveal that AMOS campaigns have already spread to over 120 countries, with the U.S., U.K., France, Italy, and Canada being among the most impacted.
“The backdoored version of Atomic macOS Stealer now has the potential to gain full access to thousands of Mac devices worldwide,” warned Moonlock researchers.
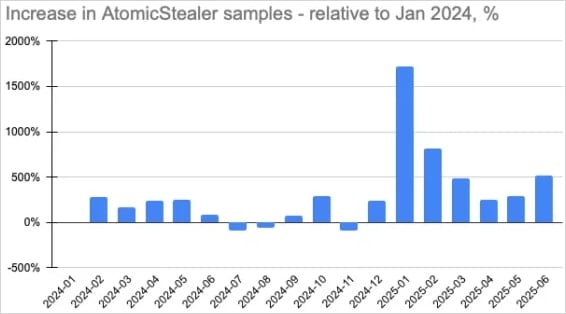 Circulation of unique Atomic stealer samples
Circulation of unique Atomic stealer samples
Source: Moonlock
A Timeline of Evolving Threats
From Info-Stealer to Persistent Threat
Atomic Stealer first appeared in April 2023 as a malware-as-a-service (MaaS) tool marketed on Telegram for $1,000/month. Its original purpose was to harvest macOS files, credentials, and crypto extensions.
By November 2023, AMOS was used to expand the ClearFake campaign to macOS, and in September 2024, it was deployed by the Marko Polo cybercrime group in large-scale attacks. Most recently, attackers shifted from broad cracked software campaigns to more targeted phishing, luring cryptocurrency users and freelancers with job interviews.
Moonlock reports that the latest version includes:
- A stealthy backdoor component
- LaunchDaemon-based persistence
- Victim ID tracking
- A revamped command-and-control (C2) infrastructure
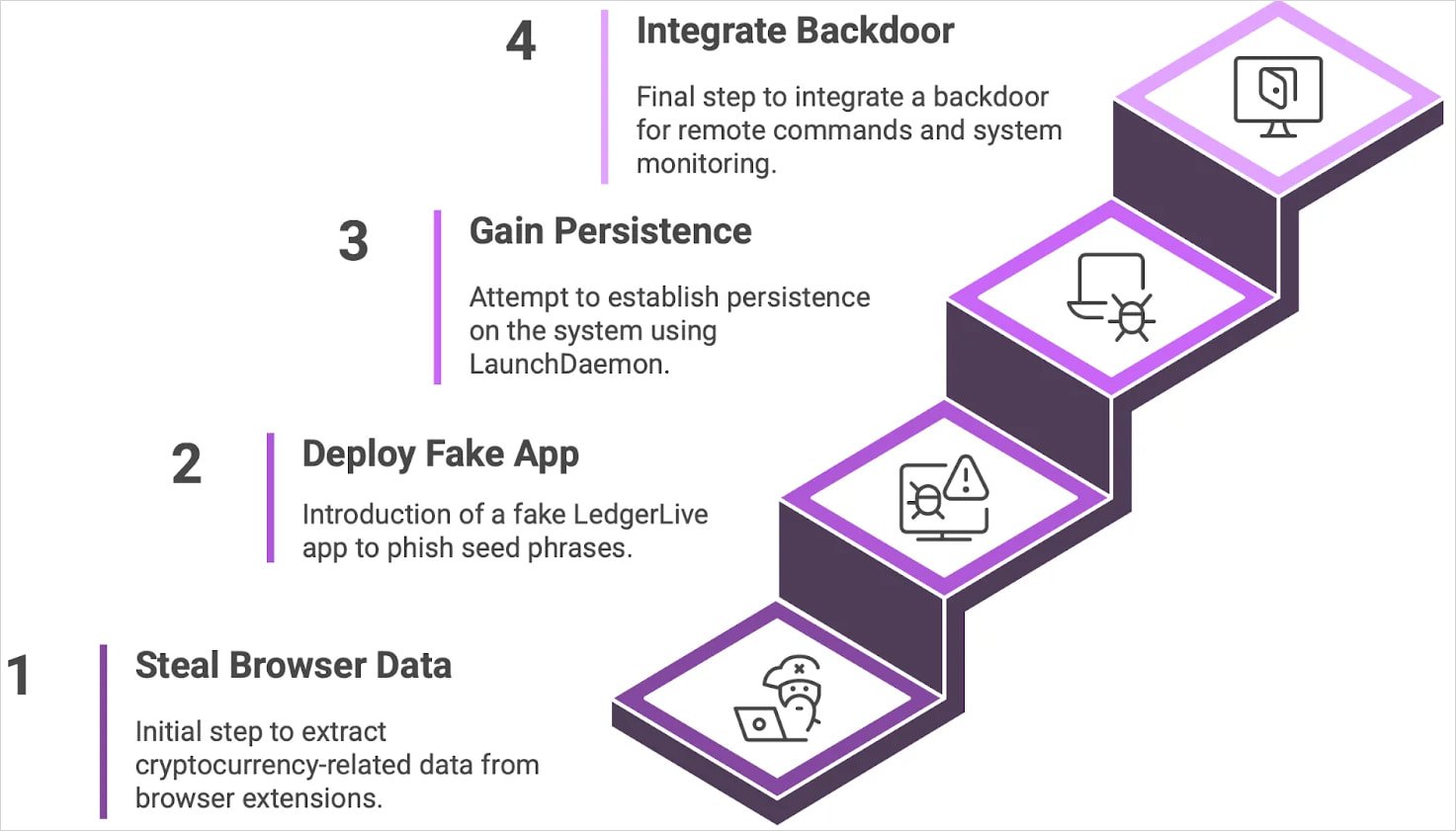 Evolution of the Atomic stealer
Evolution of the Atomic stealer
Source: Moonlock
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Detection & Mitigation
There is no workaround. The only remediation is to upgrade to a fixed version or apply the available patch.
Admins can check for signs of compromise by reviewing logs:
Look for unauthorized login entries from the root user—Cisco confirms these events are logged by default under /var/log/active/syslog/secure.
Cisco’s Product Security Incident Response Team (PSIRT) says there’s no evidence of in-the-wild exploitation or public proof-of-concept code at this time. However, indicators of compromise have been provided for organizations to proactively check their environments.
Background & Context
Cisco Unified CM (formerly CallManager) is the core call routing and control platform for Cisco’s enterprise IP telephony solutions. It’s widely deployed in corporate, government, and critical infrastructure environments.
This marks yet another high-profile hardcoded credential issue for Cisco. Similar flaws have been found in:
- Cisco IOS XE
- Cisco WAAS
- DNA Center
- Emergency Responder
- Smart Licensing Utility (CSLU) – patched in April 2025
- JWT backdoor in IOS XE – removed in May 2025
These repeated discoveries underscore the ongoing risk of embedded development credentials making their way into production firmware.
Trending: Offensive Security Tool: APKScope
Behind the Backdoor: How It Works
Hidden Files and Startup Scripts Ensure Persistence
The core payload is a hidden binary called .helper, downloaded and saved in the victim’s home directory. It’s kept alive by another hidden script named .agent, which runs .helper in a loop.
Persistence is achieved through a LaunchDaemon (com.finder.helper), installed using AppleScript. This component launches the .agent script at every system startup. The malware gains elevated privileges by tricking the user into entering their password—a credential it steals during initial infection.
Once installed, the backdoor enables:
- Arbitrary remote command execution
- Keystroke logging
- Additional payload injection
- Potential lateral movement
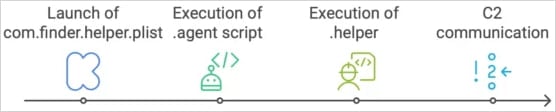 The backdoor execution chain
The backdoor execution chain
Source: Moonlock
Evading Detection: Advanced Anti-Analysis Features
To avoid discovery, the backdoor uses environment checks via system_profiler to detect if it’s running in sandboxed or virtual machine environments. It also employs string obfuscation to hide critical payloads from reverse engineers and automated detection tools.
macOS Users in the Crosshairs
The rise of advanced malware like AMOS marks a shift in cybercriminal focus toward macOS platforms, long considered less targeted than Windows. This new variant underscores how sophisticated, persistent, and tailored threats are becoming for Apple ecosystems.
Moonlock’s findings are a call to action for both consumers and businesses using macOS to prioritize endpoint security, keep systems updated, and be wary of unsolicited downloads or phishing messages.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













