Chameleon Android Banking Trojan Strikes Again: New Version Disables Biometrics to Steal PINs
Reading Time: 3 Minutes
The Chameleon Android banking trojan has resurfaced with a new iteration that employs a cunning method to compromise devices by disabling fingerprint and face unlock features in order to pilfer device PINs.
This latest version of Chameleon, as reported by researchers at ThreatFabric, has been observed to utilize an HTML page trick to gain access to the Accessibility service and disrupt biometric operations, thereby enabling the theft of PINs and unrestricted access to the device.
Previous iterations of Chameleon, identified earlier this year, masqueraded as Australian government agencies, banks, and the CoinSpot cryptocurrency exchange, carrying out a range of malicious activities such as keylogging, overlay injection, cookie theft, and SMS theft on compromised devices.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
According to ThreatFabric, the current distribution of this malware is facilitated through the Zombinder service, where it poses as Google Chrome. Zombinder is known for attaching malware to legitimate Android apps, allowing the malicious code to operate surreptitiously in the background while the victim uses the intended app.
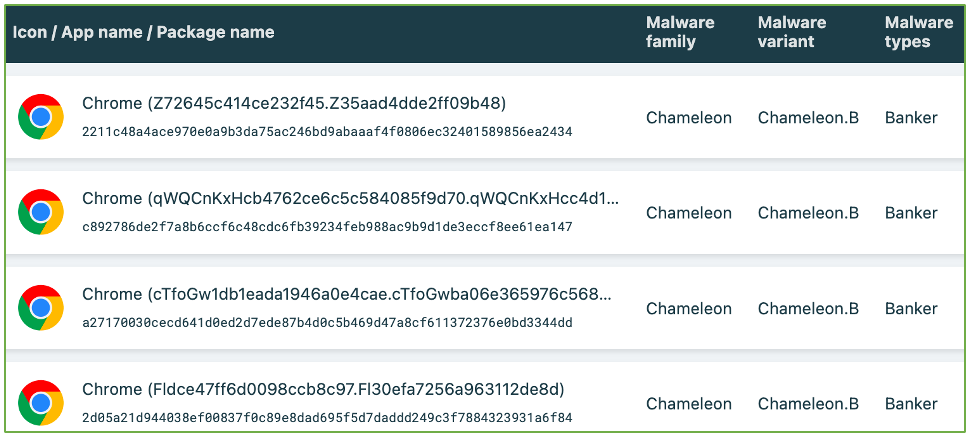 Chameleon-carrying APKs posing as Google Chrome (ThreatFabric)
Chameleon-carrying APKs posing as Google Chrome (ThreatFabric)New variant features
One of the new features of this latest Chameleon variant is its ability to display an HTML page on devices running Android 13 and later, coercing users to grant the app permission to use the Accessibility service. This is particularly concerning as Android 13 and later versions are equipped with a security feature called “Restricted setting,” designed to block the approval of potentially hazardous permissions like Accessibility.
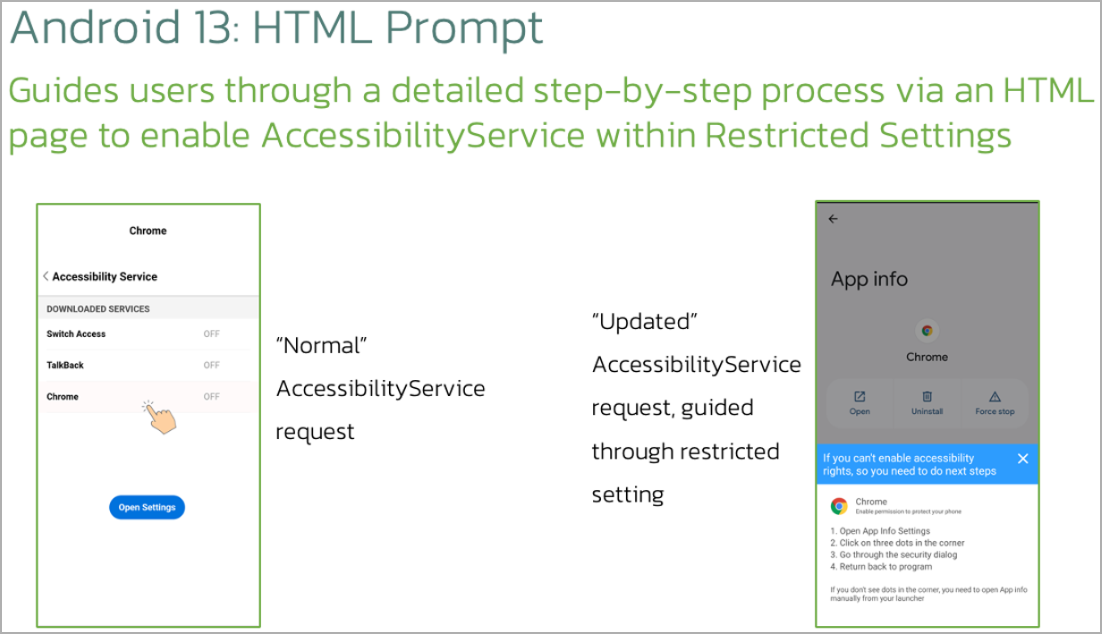 Chameleon’s HTML page prompt (ThreatFabric)
Chameleon’s HTML page prompt (ThreatFabric)Furthermore, the new Chameleon variant can interrupt biometric operations on the device, such as fingerprint and face unlock, by leveraging the Accessibility service to compel a fallback to PIN or password authentication. This enables the malware to capture PINs and passwords entered by the victim, granting it unrestricted access to the device for clandestine malicious activities.
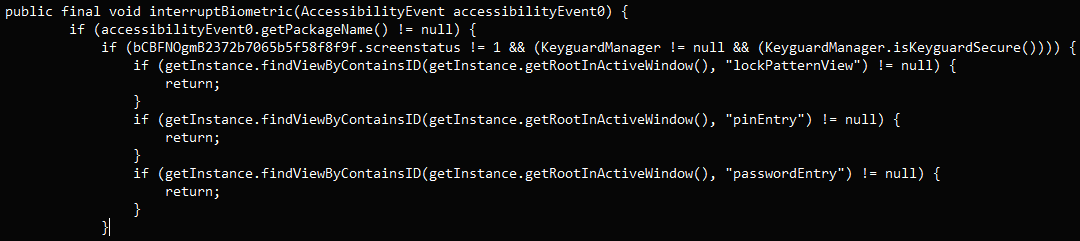 Java code snippet disrupting the biometric service on Android (ThreatFabric)
Java code snippet disrupting the biometric service on Android (ThreatFabric)Trending: Recon Tool: PassDetective
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com










