ChaosBot: Rust Backdoor Uses Discord C2 — Chaos Ransomware Adds Destructive & Clipboard-Hijack Features
Overview
Security firms have disclosed two related developments from the “Chaos” ecosystem: a new Rust-based backdoor called ChaosBot used for reconnaissance and remote command execution, and an evolved Chaos-C++ ransomware family that now includes destructive deletion and clipboard-hijacking capabilities. The backdoor was detailed by eSentire, which first observed activity in a financial-services environment in late September 2025; Fortinet’s FortiGuard Labs described the new ransomware variant and its tactics. Together the findings show a multi-vector campaign combining credential abuse, phishing, DLL sideloading and unconventional command-and-control (C2) channels.
How ChaosBot is deployed
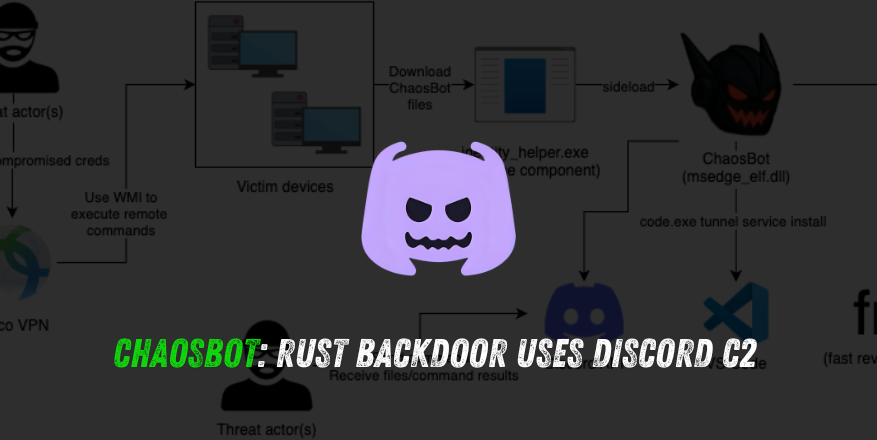
eSentire’s investigation tied initial access to compromised credentials: a VPN credential and an over-privileged Active Directory account named serviceaccount. Using these credentials, the attackers used WMI to run remote commands across the environment and stage the backdoor deployment. Other observed delivery methods include phishing messages carrying a malicious Windows LNK shortcut that launches a PowerShell one-liner to fetch and run the payload, while displaying a decoy PDF (example: spoofed State Bank of Vietnam correspondence) to distract victims.
Technical profile: ChaosBot behavior
Key technical traits of ChaosBot include:
- Language & persistence: The backdoor is written in Rust, with a DLL payload (
msedge_elf.dll) that is DLL-sideloaded via a bundled Edge helper binary (identity_helper.exe). - C2 via Discord: Operators use Discord user accounts (notably
chaos_00019andlovebb0024) and create channels named after victim hostnames to issue commands and exfiltrate data — a lightweight, resilient C2 channel that blends in with benign traffic. - Proxy & lateral movement: The implant downloads a fast reverse proxy (FRP) to open ingress into the compromised network and maintain persistent remote access. Attempts were also made to configure VS Code Tunnel as an alternate backdoor, though those attempts reportedly failed.
- Capabilities: Supported commands observed include
shell(execute PowerShell/commands),scr(screenshot capture),download(pull files), andupload(push files back to the Discord channel). - Evasion: New variants employ ETW evasion by patching
ntdll!EtwEventWrite(first instructions patched to neutralize tracing) and check MAC address prefixes commonly used by VMware/VirtualBox to avoid execution in VMs or sandboxes.
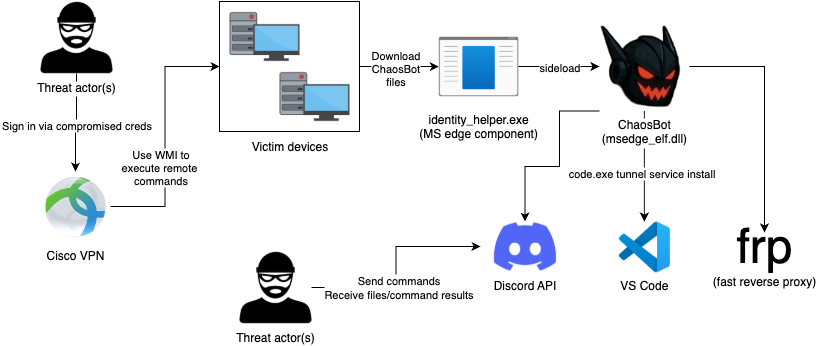 Figure 2 – Attack Chain diagram – esentire.com
Figure 2 – Attack Chain diagram – esentire.com
Offensive Security, Bug Bounty Courses
Chaos-C++ ransomware: destructive tactics and clipboard hijack
Fortinet reports the Chaos-C++ ransomware family has adopted more aggressive monetization techniques:
- Destructive deletion: The ransomware can irreversibly delete files larger than ~1.3 GB instead of encrypting them, escalating the destructive impact on victims.
- Clipboard hijacking: The malware monitors the system clipboard and replaces cryptocurrency addresses (e.g., Bitcoin) with attacker-controlled wallet addresses to intercept transfers.
- Execution flow & persistence: The downloader masquerades as utilities like System Optimizer v2.1. On execution it checks for
%APPDATA%\READ_IT.txtto decide behavior: if present, it goes into monitoring mode (clipboard watch); otherwise, it checks for admin rights and then disables recovery options before encrypting files under ~50 MB and skipping those between 50 MB and 1.3 GB. - Robust crypto + fallback: Encrypts with symmetric/asymmetric methods and includes an XOR fallback, reportedly to ensure file corruption even if cryptographic routines fail.
Operational picture & observed targets
- eSentire’s detection was tied to a financial-services customer, but the tactics are broadly applicable to enterprise environments that expose services to VPN/remote access or run legacy/high-privilege accounts.
- The weaponization of Discord — a legitimate collaboration platform — complicates egress filtering and detection, while LNK delivery and DLL sideloading remain effective at bypassing naive defences.
- The combination of credential abuse, remote command execution via WMI, FRP tunnels, and file exfiltration points to a capable, opportunistic attacker motivated by access, persistence and potential extortion.
Trending: Offensive Security Tool: FormPoison
Detection and mitigation guidance
Practical steps to detect and mitigate ChaosBot / Chaos-C++ activity:
Credentials & accounts
- Immediately rotate VPN and service account credentials and enforce unique, least-privilege service accounts.
- Require multi-factor authentication (MFA) for VPN and any remote access.
- Audit
serviceaccountand other privileged AD accounts — remove unnecessary privileges and enable Just-In-Time (JIT) or Just-Enough-Admin (JEA) controls.
Endpoint & telemetry
- Detect suspicious DLL sideloading (e.g.,
identity_helper.exelaunching nonstandard DLLs) and monitor processes that spawn network proxies or FRP binaries. - Alert on PowerShell one-liners launched from LNK files, Office/Explorer contexts, or from temporary folders.
- Monitor for patched ETW calls (unexpected modifications to
ntdll!EtwEventWrite) and for MAC addresses or environment checks that indicate VM-evasion logic. - Flag unexpected VS Code Tunnel / remote-access service registrations and anomalous outbound connections to Discord endpoints.
Network & egress
- Restrict outbound access to Discord or require proxying/inspection for allowed collaboration platforms.
- Block or inspect connections to FRP endpoints and other dynamic reverse proxy services.
- Implement strict egress filtering and TLS inspection where feasible to detect C2 traffic hiding inside legitimate protocols.
Email & user resilience
- Block LNK attachments at email gateway or convert attachments to safe previews; disallow execution from user download folders.
- Educate users to treat unsolicited archives/shortcuts and unexpected PDFs cautiously — particularly those that ask to “open” or contain attachments.
Backups & recovery
- Maintain air-gapped, immutable backups and test restore processes. Given the ransomware’s destructive options, backups are a critical mitigation.
- Restrict filesystem and backup service permissions so ransomware processes cannot delete backups.
Hunt & response
- Hunt for indicators: unusual Discord API usage, FRP binaries,
msedge_elf.dlloridentity_helper.exeanomalies, PowerShell downloaders, new persistent services, and CREATE/WRITE operations for%APPDATA%\READ_IT.txt. - Isolate affected hosts, collect memory and disk images for forensic analysis, and look for lateral movement via WMI or scheduled tasks.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com













