ClickFix Attack: Expired Discord Invites Now Deliver Remote Access Trojans

Hackers Exploit Discord Invite Flaw to Deliver Malware via Hijacked Links
A new cyberattack campaign is weaponizing expired and deleted Discord invite links to redirect unsuspecting users to malicious servers that distribute remote access trojans (RATs) and info-stealing malware. Security firm Check Point reports that over 1,300 users across the US, UK, France, the Netherlands, and Germany have already been affected.
Discord’s Vanity Link Loophole Exposed
At the center of the attack is a flaw in Discord’s invitation system—specifically, how the platform handles custom (vanity) invite codes for Level 3 servers. When these servers lose their boost status, their custom invite codes become available again, allowing other users to reclaim and reuse them for malicious purposes.
Incredibly, the same flaw applies to expired temporary invites and deleted permanent links, which hackers can now “revive” and use for new servers, exploiting users’ trust in familiar links.
“Surprisingly, the mechanism for creating custom invite links lets you reuse expired temporary codes and, in some cases, deleted permanent ones,” said Check Point.
Additionally, Discord’s case-insensitive handling of vanity links allows attackers to register duplicate invite codes using lowercase variations of uppercase invites—even if the original is still valid.
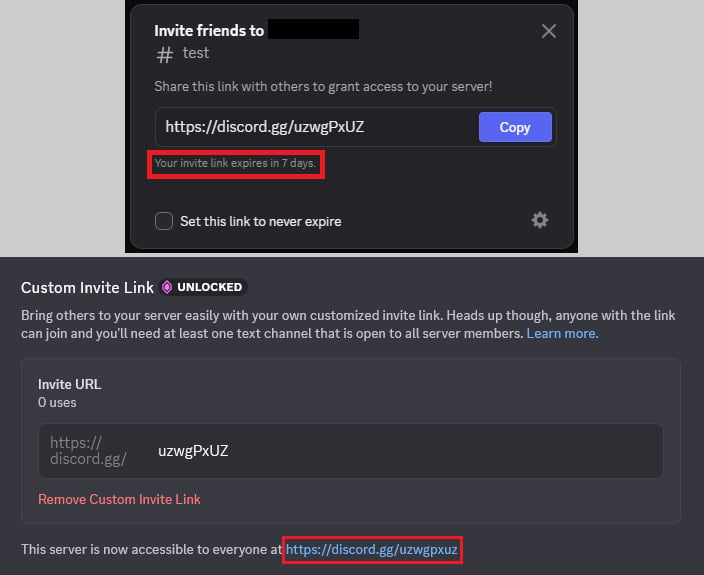 Hijacking a temporary invite code (top) and reusing it in a vanity link (bottom)
Hijacking a temporary invite code (top) and reusing it in a vanity link (bottom)
Source: Check Point
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Weaponized Invites Lead to Fake Verification Traps
Once hijacked, the invite links redirect victims to fake servers that appear legitimate. These servers typically contain only one visible channel: #verify. Here, an automated bot prompts users to complete a “verification” process.
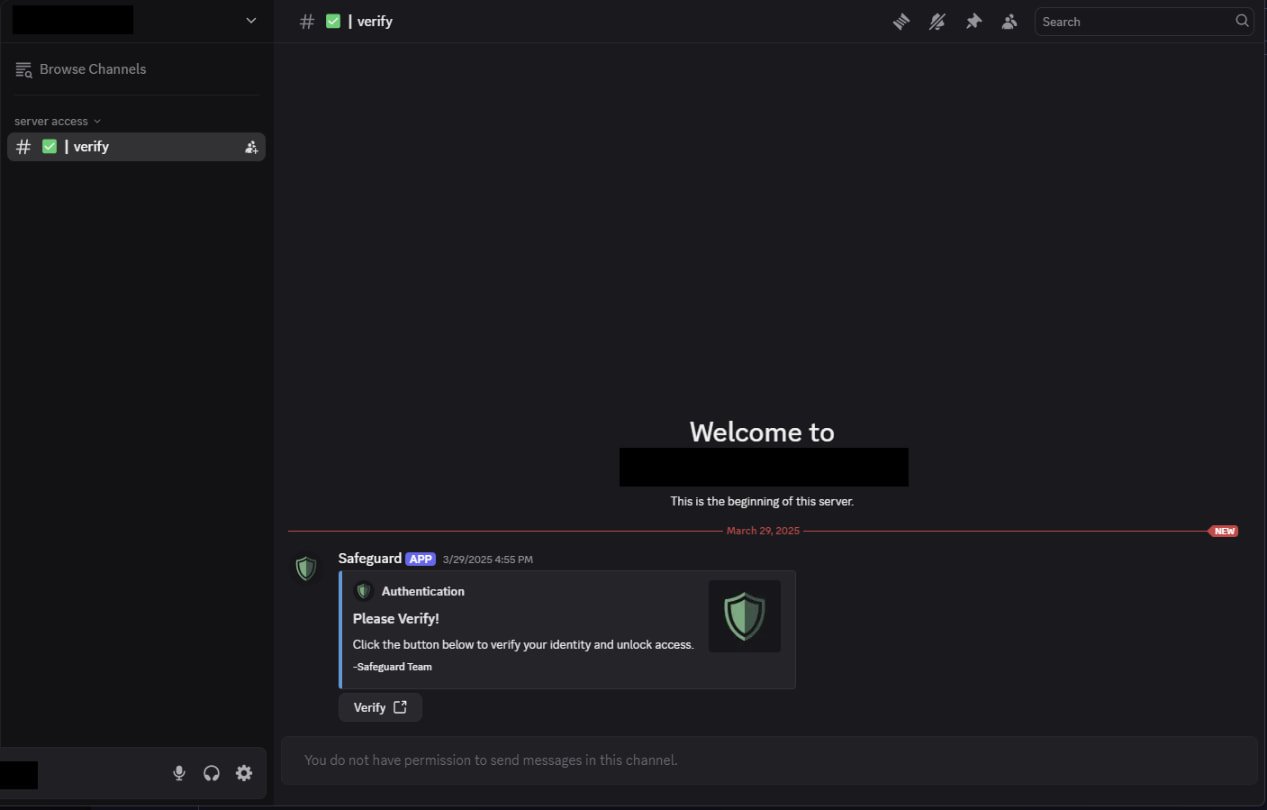 Attacker’s Discord channel
Attacker’s Discord channel
Source: Check Point
Victims are tricked into copying and executing a malicious PowerShell command via the Windows Run dialog. The attack—dubbed ClickFix—mimics Discord’s interface and falsely claims that a CAPTCHA failed to load.
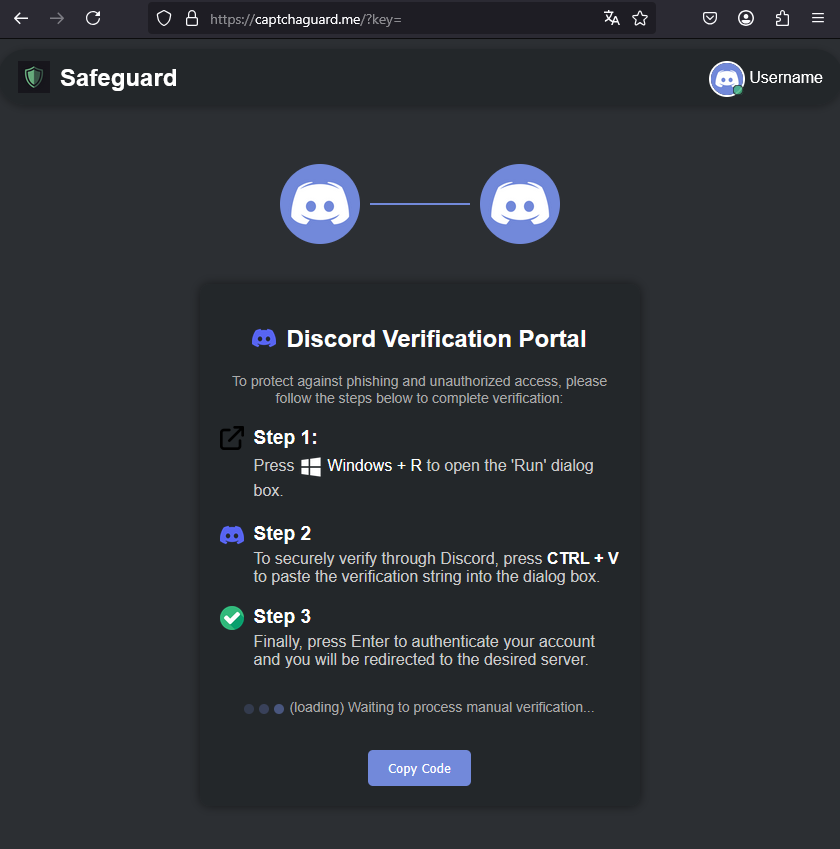 The ClickFix page
The ClickFix page
Source: Check Point
The end goal: tricking users into launching a multi-stage malware infection chain without realizing it.
Multi-Stage Malware Payloads Delivered via Bitbucket
The malicious script initiates a complex infection chain:
- PowerShell downloaders fetch further stages
- Obfuscated C++ loaders and VBScript files execute malicious payloads
- Final payloads are hosted on Bitbucket, a legitimate code hosting platform
The deployed malware includes:
- AsyncRAT (
AClient.exe)- Remote access trojan with keylogging, webcam/microphone access, and dynamic C2 retrieval via Pastebin
- Skuld Stealer (
skul.exe)- Info-stealer targeting browser credentials, cookies, Discord tokens, and crypto wallets via injected JavaScript
- ChromeKatz (
cks.exe)- Custom data-stealer built from the open-source ChromeKatz project, focused on browser data theft
The attack also creates a scheduled task to re-execute the malware every five minutes, ensuring persistence.
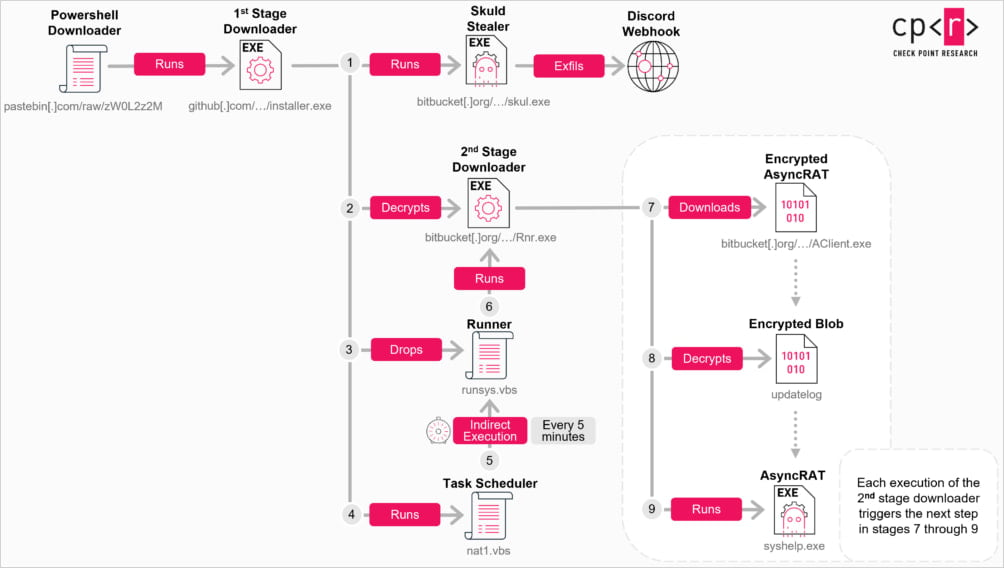 Infection chain from ClickFix to malware
Infection chain from ClickFix to malware
Source: Check Point
Trending: Recon Tool: WaybackLister
Countries Targeted and Protective Measures
The campaign has impacted users primarily in the US, UK, France, the Netherlands, and Germany, according to download telemetry data from Check Point.
Recommended defenses include:
- Avoid clicking old Discord invite links, especially from outdated posts.
- Never run PowerShell or other command-line code from unverified sources.
- Treat any verification process—particularly those that redirect you outside Discord—with high suspicion.
- For server admins, use permanent invite links to reduce the risk of link hijacking.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













