Critical RCE Flaw in WordPress ‘Alone’ Theme Under Mass Exploitation

Threat actors are actively exploiting a critical vulnerability in the WordPress theme “Alone”, enabling unauthenticated remote code execution and full site takeovers. The flaw, tracked as CVE-2025-5394, affects all theme versions up to 7.8.3.
Over 120,000 Exploitation Attempts Blocked
WordPress security firm Wordfence reports that it has already blocked over 120,000 exploitation attempts on customer sites, with attack activity starting before public disclosure of the flaw.
This indicates that attackers are actively monitoring changelogs and patch releases to identify newly introduced vulnerabilities before official security advisories are published.
Technical Details of the Vulnerability
The flaw lies in the theme’s alone_import_pack_install_plugin() function, which:
- Is exposed via the
wp_ajax_nopriv_hook, allowing unauthenticated access - Lacks nonce validation, leaving it vulnerable to abuse
- Accepts a remote plugin source via POST data, allowing attackers to install any ZIP file
The vulnerable function can be exploited by sending crafted AJAX requests to admin-ajax.php, triggering the installation of malicious plugins from remote servers.
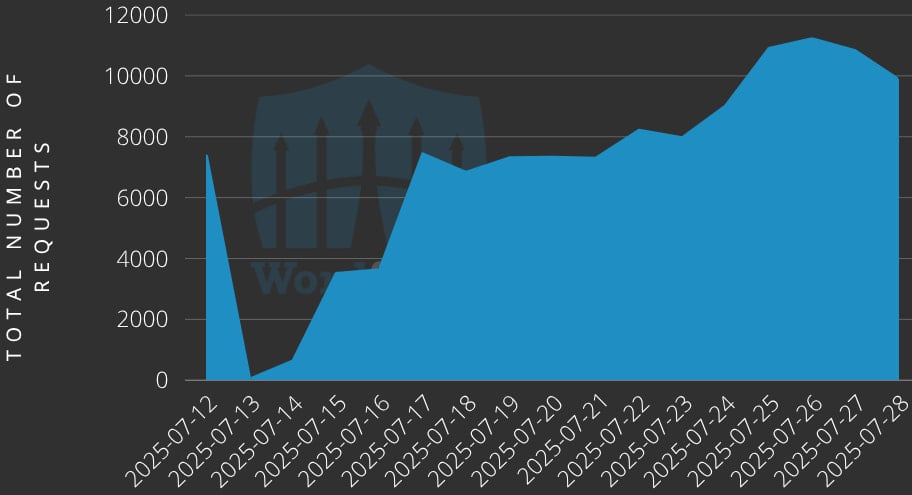 Volume of exploitation attempts against Alone-powered sites
Volume of exploitation attempts against Alone-powered sites
Source: Wordfence
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Full Site Takeovers via Webshells and Backdoors
Attackers are using this exploit to:
- Upload PHP webshells and password-protected backdoors
- Maintain persistence via hidden administrator accounts
- Deploy full-featured file managers for complete control
- Modify or access the site database and backend
These attacks can result in total compromise of affected websites.
Indicators of Compromise
Site owners should immediately check for:
- New unknown administrator users
- Suspicious plugin folders or uploaded ZIP archives
- Requests to:
admin-ajax.php?action=alone_import_pack_install_plugin
Known malicious IP addresses involved in the attacks include:
193.84.71.24487.120.92.24146.19.213.182a0b:4141:820:752::2
Wordfence recommends blocking these IPs at the firewall or server level.
Trending: Offensive Security Tool: APKScope
Patch Released After Delayed Vendor Response
Although Wordfence reported the issue to the theme developer Bearsthemes on May 30, 2025, no response was received. The security firm escalated the matter to Envato on June 12.
The issue was patched on June 16, with the release of Alone version 7.8.5, which is now the recommended update for all users.
Alone Theme Primarily Used by Non-Profits
The Alone theme is a premium WordPress product with nearly 10,000 sales on the Envato Market. It is popular among charities, NGOs, fundraising organizations, and other non-profits—many of whom may lack the resources for robust security monitoring.
This increases the risk of undetected compromise in vulnerable deployments.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













