Ghost Calls: New C2 Technique Abuses Zoom and Teams to Evade Detection

A newly disclosed command-and-control (C2) evasion technique dubbed Ghost Calls allows attackers to tunnel malicious traffic through trusted conferencing infrastructure, including Zoom and Microsoft Teams TURN servers.
Presented at Black Hat USA by Praetorian security researcher Adam Crosser, this technique allows red teams—and potentially threat actors—to establish covert, real-time C2 channels that mimic legitimate enterprise activity.
How Ghost Calls Works
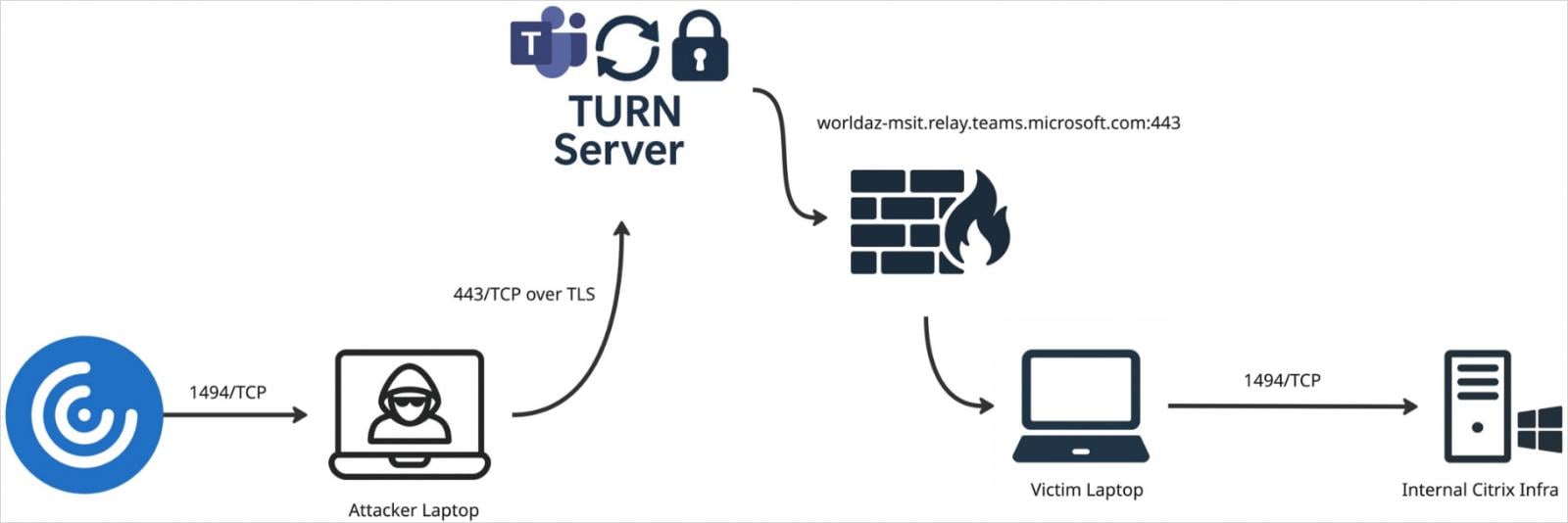
Ghost Calls abuses TURN (Traversal Using Relays around NAT) servers used by conferencing and VoIP platforms. These TURN servers facilitate NAT traversal by relaying traffic between endpoints that can’t connect directly.
When a conferencing app like Zoom or Teams initiates a call, it generates temporary TURN credentials for the session. Ghost Calls can hijack these credentials to establish a TURN-based WebRTC tunnel between an attacker and a compromised host.
This tunnel can then carry arbitrary traffic, enabling attackers to proxy C2 commands, exfiltrate data, and control compromised systems.
 Local port forwarding via Ghost Calls
Local port forwarding via Ghost Calls
Source: Praetorian
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
C2 Traffic Disguised as Web Conferencing
Ghost Calls effectively blends attacker traffic into normal video conferencing patterns, taking advantage of the following properties:
- Encrypted WebRTC channels make packet inspection ineffective
- Use of trusted infrastructure (Zoom, Teams) bypasses firewalls and proxies
- Traffic over port 443 makes the communication indistinguishable from HTTPS
Unlike traditional C2 protocols—which are often high-latency, limited in scope, and easy to flag—Ghost Calls provides low-latency, interactive sessions suitable for VNC tunneling, data exfiltration, and real-time control.
Introducing TURNt: The Ghost Calls Utility
To demonstrate the technique, Crosser developed an open-source tool called TURNt, available on GitHub.
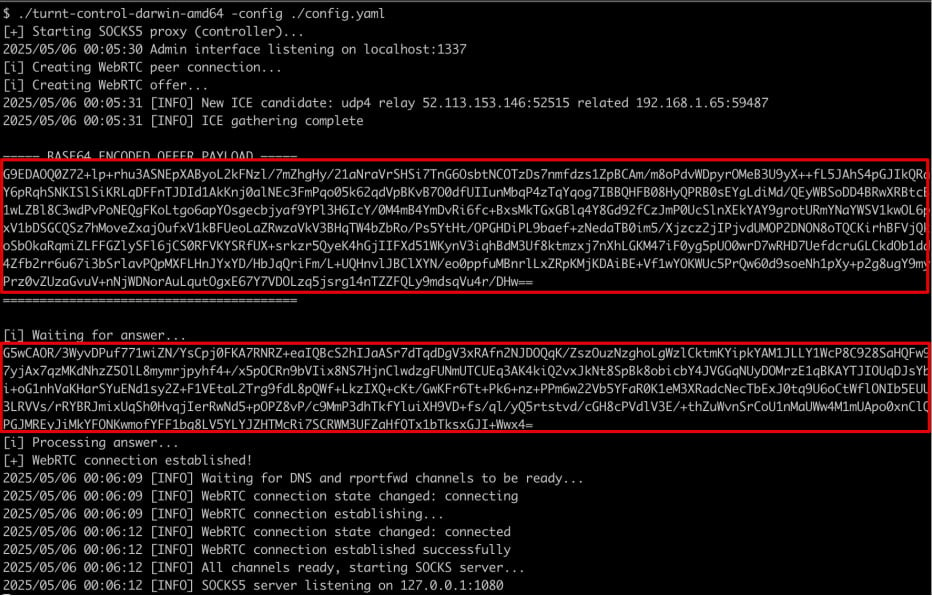
TURNt has two components:
- Controller: Runs on the attacker’s system and functions as a SOCKS proxy
- Relay: Deployed on the victim’s machine, connects back via TURN
Using TURNt, red teams (or attackers) can:
- Perform SOCKS proxying
- Conduct local and remote port forwarding
- Exfiltrate sensitive data
- Tunnel hidden VNC traffic through TURN infrastructure
The tool effectively relays traffic through conferencing providers’ TURN servers, hiding malicious activity behind enterprise-trusted IP ranges.
 SOCKS proxying on TURNt
SOCKS proxying on TURNt
Source: Praetorian
Trending: Offensive Security Tool: RingReaper
No Exploit, Just Abuse of Legitimate Functionality
Ghost Calls does not exploit any vulnerabilities in Zoom, Teams, or WebRTC. It abuses legitimate TURN behavior, making it difficult to mitigate without disrupting core conferencing functionality.
Nonetheless, the research raises concerns for defenders, especially those relying on network traffic analysis or TLS inspection to detect C2 channels.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













