‘Hazy Hawk’ Hijacks Abandoned Cloud CNAMEs to Exploit Trusted Domains

‘Hazy Hawk’ Hijacks Abandoned Cloud CNAMEs to Exploit Trusted Domains in Global Scam Campaign
A newly identified threat actor dubbed ‘Hazy Hawk’ has been observed hijacking abandoned DNS CNAME records that point to decommissioned cloud infrastructure, allowing them to take over trusted subdomains of some of the world’s most reputable institutions and corporations.
According to a new report from Infoblox, Hazy Hawk exploits these overlooked DNS configurations to distribute scams, malicious ads, and fake applications, using the credibility of compromised parent domains to boost legitimacy and evade detection.
How the Attack Works
The campaign begins with scanning for forgotten DNS CNAME records that still point to expired or deleted cloud resources. By referencing passive DNS telemetry, the threat actor identifies cloud services that have been unlinked from their owning domain but still referenced in DNS.
Hazy Hawk then re-registers cloud infrastructure—such as an Azure, AWS, or GCP resource—using the same name as the abandoned one. As a result, any subdomain with a dangling CNAME record will now resolve to the attacker’s new infrastructure, effectively hijacking it without needing access to the domain itself.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
High-Profile Victims
The impact of this campaign is global. Infoblox reports that Hazy Hawk successfully hijacked subdomains of major organizations, including:
- cdc.gov – U.S. Centers for Disease Control and Prevention
- honeywell.com – Honeywell International
- berkeley.edu – University of California, Berkeley
- michelin.co.uk – Michelin Tires UK
- ey.com, pwc.com, deloitte.com – Big Four consulting firms
- ted.com – TED Talks
- health.gov.au – Australian Department of Health
- unicef.org – United Nations Children’s Fund
- nyu.edu – New York University
- unilever.com – Global consumer goods company
- ca.gov – California State Government
A complete list is available in the Infoblox report, highlighting the widespread nature of the campaign.
Malicious Infrastructure and Tactics
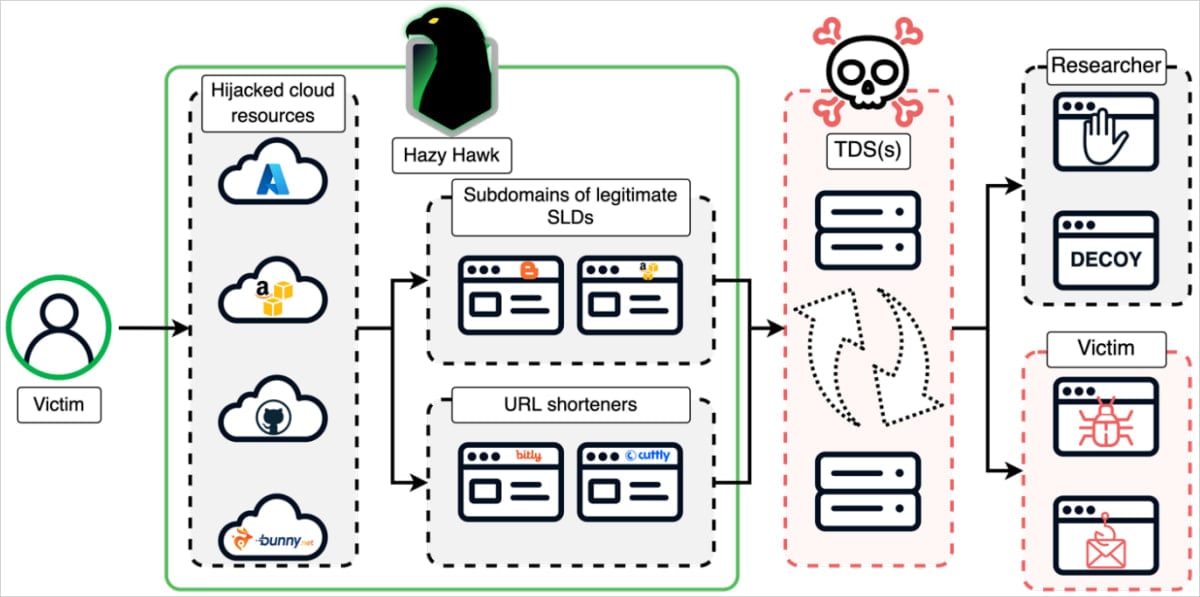 Overview of the Hazy Hawk attack
Overview of the Hazy Hawk attack
Source: Infoblox
Once control over a subdomain is achieved, Hazy Hawk generates hundreds of scam URLs that inherit the trust and SEO rankings of the legitimate domain. These malicious links are indexed by search engines, giving them high visibility and further credibility to unsuspecting users.
Users who land on the URLs are routed through multiple redirection layers and Traffic Distribution Systems (TDS). These systems profile the victim based on:
- Geographic location
- IP reputation and VPN detection
- Browser fingerprinting
- Device and OS type
Qualified users are redirected to tech support scams, fake antivirus warnings, phishing pages, streaming scams, and adult content traps.
Victims who accept browser push notification requests from these pages are continually bombarded with persistent scam alerts—even after closing the site—enabling a high-revenue ad fraud model.
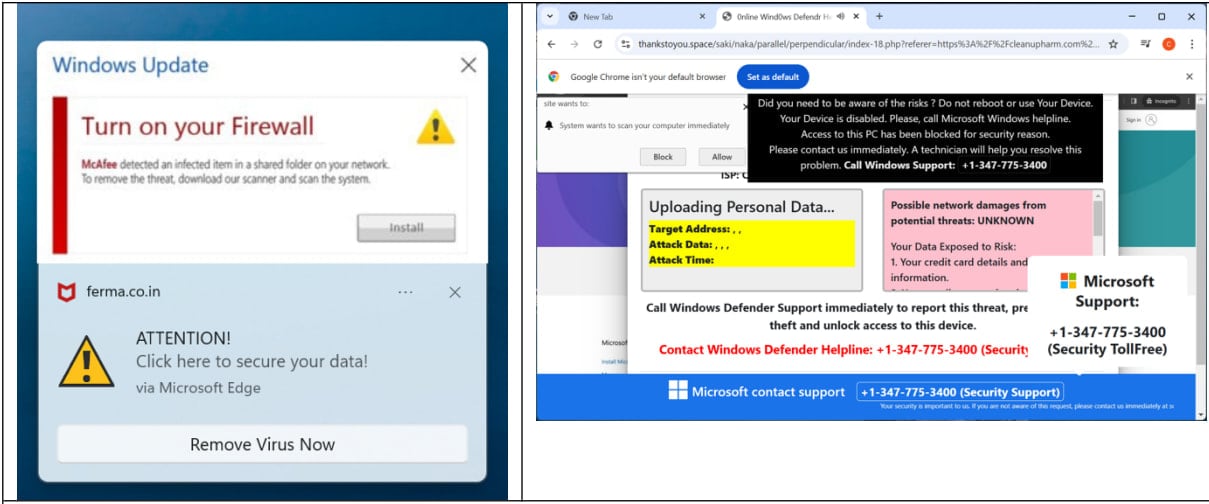 Push notification examples from the campaign
Push notification examples from the campaign
Source: Infoblox
Trending: Major Cyber Attacks that shaped 2024
A Growing Trend: DNS Neglect
Hazy Hawk is not alone. Infoblox previously tracked another group, Savvy Seahorse, employing a similar CNAME hijacking tactic for investment scam campaigns. These incidents reflect a growing trend: cybercriminals increasingly abuse dangling DNS records as part of low-effort, high-impact operations.
DNS CNAME records, especially those tied to cloud-hosted infrastructure, are often neglected during service decommissioning, making them an ideal target for attackers who understand the nuances of cloud-based resource naming.
Recommendations for Organizations
- Audit DNS configurations regularly, especially CNAME records pointing to external or cloud-hosted services.
- Decommission cloud services securely and delete associated DNS entries immediately.
- Use DNS monitoring tools to detect and alert on resolution failures or unexpected changes.
- Implement DNS security extensions (DNSSEC) to authenticate DNS responses.
- Restrict wildcard DNS entries where possible to minimize accidental exposures.
Trending: ClickFix Malware Campaign Now Hits Linux
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













