iCloud Calendar Invites Abused to Send Callback Phishing Emails via Apple Servers

Abuse of iCloud Calendar Invites
Threat actors are leveraging Apple’s iCloud Calendar invite system to deliver phishing emails disguised as PayPal purchase notifications, making the messages appear more legitimate and allowing them to bypass traditional spam filters.
Earlier this month, a reader shared an example with BleepingComputer. The phishing email claimed the recipient had been billed $599 through PayPal, urging them to call a “support” number to dispute or cancel the charge.
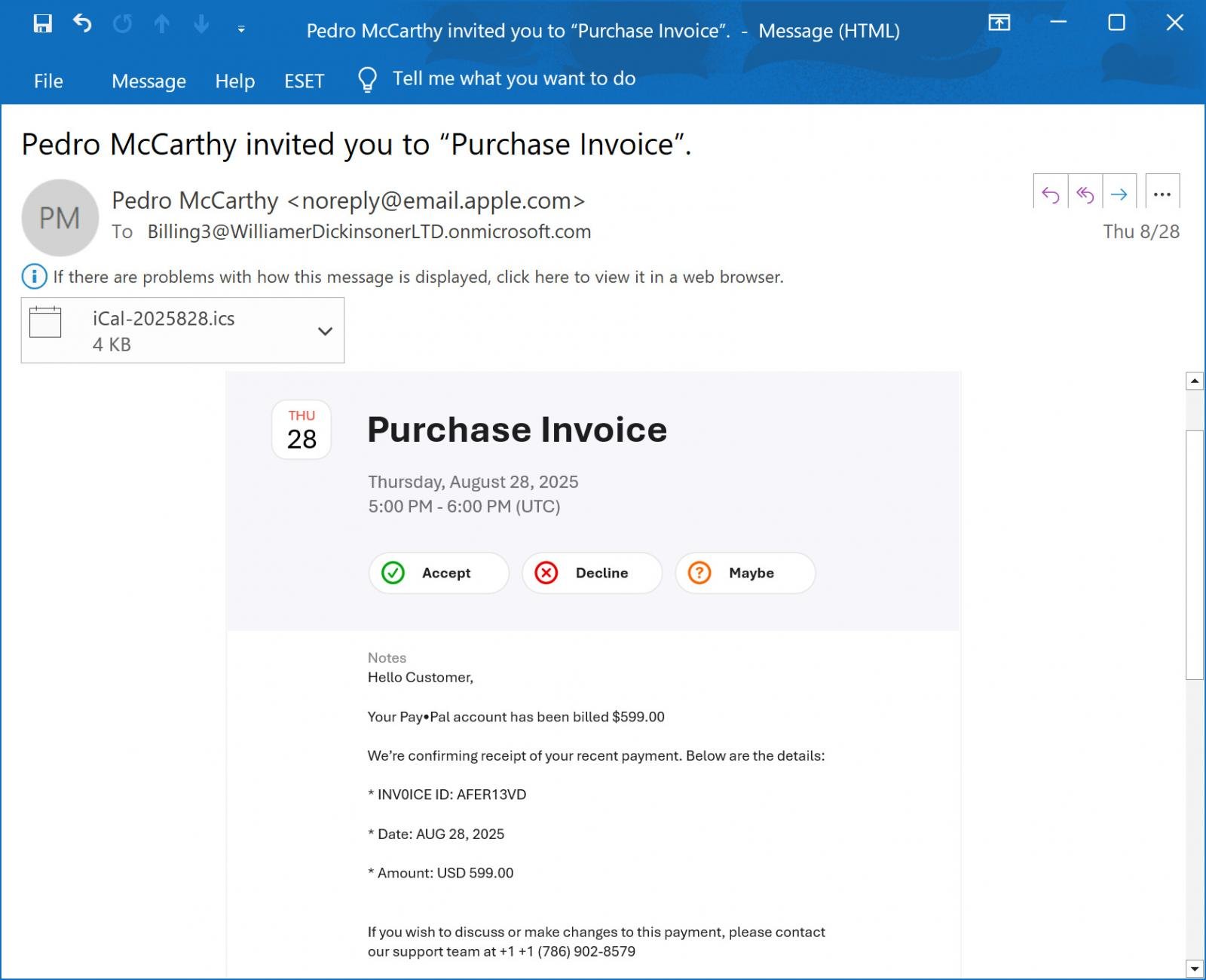 iCloud Calendar invites used for phishing emails
iCloud Calendar invites used for phishing emails
Source: BleepingComputer
Classic Callback Phishing Tactics
This campaign follows the typical callback phishing playbook:
- Victims are scared into believing an unauthorized payment was processed.
- They are urged to call a fake support line.
- Once on the phone, scammers attempt to persuade targets to install remote access tools.
Historically, such scams have been used not to issue refunds but to steal bank funds, deploy malware, or exfiltrate sensitive data.
Offensive Security, Bug Bounty Courses
Why Apple Servers Are Involved
What makes this campaign unusual is that the phishing messages were sent from [email protected], fully authenticated by Apple’s infrastructure.
Email headers showed:
Authentication-Results: spf=pass (sender IP is 17.23.6.69)
smtp.mailfrom=email.apple.com; dkim=pass (signature was verified)
header.d=email.apple.com; dmarc=pass action=none header.from=email.apple.com;
This was achieved by embedding the phishing lure in the Notes field of an iCloud Calendar invite. When external recipients are added to an iCloud Calendar event, Apple’s servers automatically send an email invitation on behalf of the calendar owner — in this case, carrying the scam text.
The targeted address, a Microsoft 365 email account, acted as a forwarding mailing list, distributing the phishing email to multiple recipients.
Role of Microsoft’s SRS
Normally, forwarded emails break SPF checks. However, Microsoft 365’s Sender Rewriting Scheme (SRS) rewrites the return path so that forwarded emails can still pass authentication.
This allowed the phishing message to retain its legitimacy, appearing to come directly from Apple’s trusted infrastructure even after being distributed through Microsoft’s system.
Trending: Recon Tool: ZoomeyeSearch
Impact and Risks
While the lure itself — a fake PayPal receipt — is common, the use of Apple’s servers and branding significantly increases the chance of victims falling for the scam.
Because these emails pass all authentication checks, they are more likely to evade spam filters and reach inboxes.
Security experts caution that unexpected calendar invites containing unusual text should always be treated as suspicious.
BleepingComputer reached out to Apple for comment regarding the abuse of its iCloud Calendar infrastructure. At the time of publication, no response had been received.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













