Koske Malware Hides in Panda JPEGs to Deploy Crypto Miners on Linux

A new Linux malware named Koske is exploiting misconfigured JupyterLab environments and using innocent-looking panda bear images to deploy stealthy rootkits and crypto miners, researchers from AquaSec revealed.
Malicious Images Conceal Sophisticated Payloads
Koske uses a unique technique involving polyglot files—JPEG images that are also valid shell scripts. These files show a normal image to the user but execute malicious code when interpreted by a script processor.
“The attacker downloads two .JPEG images of panda bears hosted on trusted platforms like OVH or FreeImage, each containing an embedded payload,” AquaSec stated.
Unlike traditional steganography, the malware is not hidden inside image pixels. Instead, the JPEG files contain valid image headers followed by appended shell scripts and C code, enabling dual functionality.
Initial Access: Jupyter Misconfigurations
The attack begins by exploiting misconfigured JupyterLab instances exposed on the internet. These configurations allow command execution, giving attackers a remote foothold.
Once inside, the attacker downloads the panda JPEGs and triggers the hidden payloads:
- Payload 1: C code compiled and executed in memory as a
.sorootkit, leveragingLD_PRELOADto override system calls and hide itself. - Payload 2: Shell script executed in-memory, responsible for persistence, system manipulation, and cryptominer deployment.
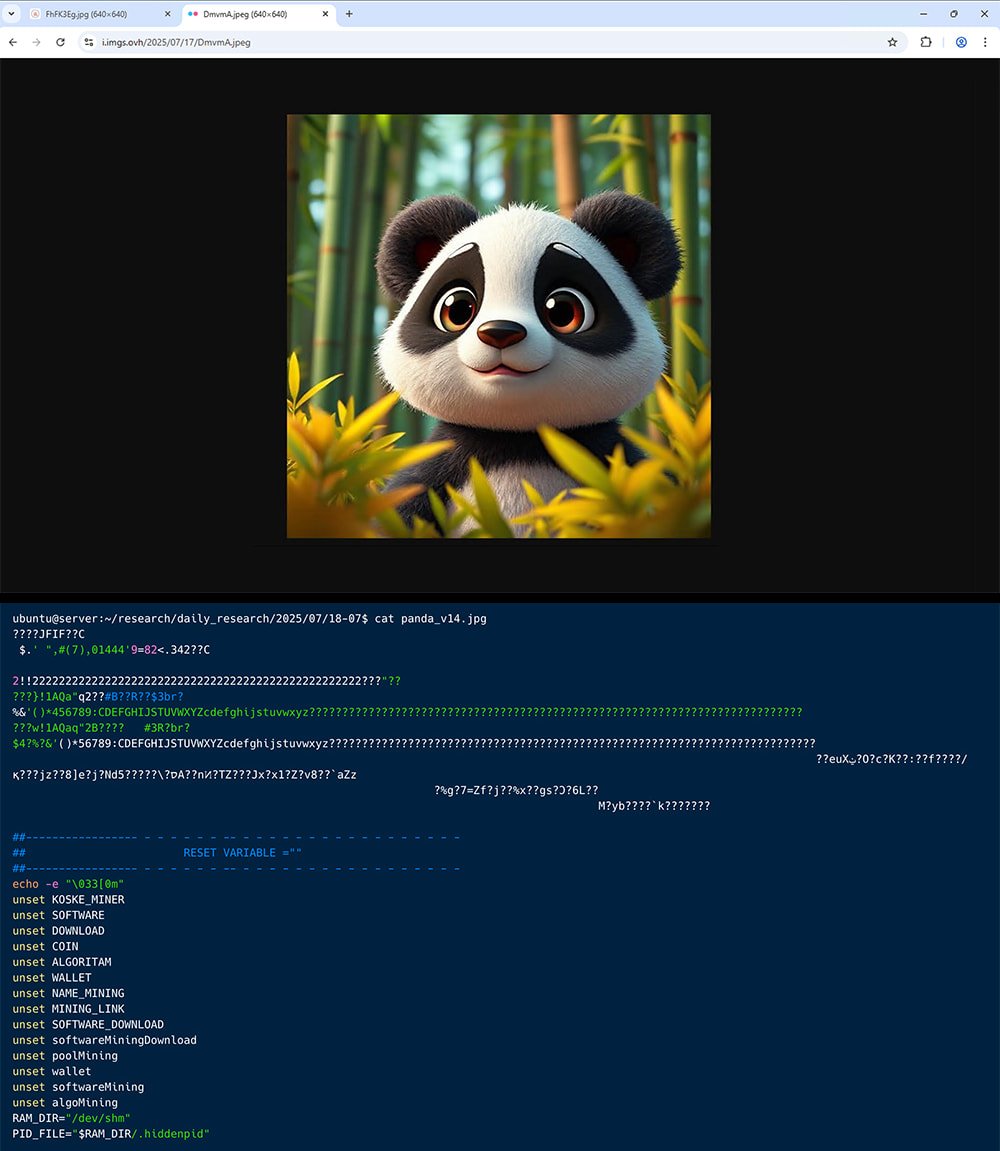 Seemingly innocuous panda image (top), file contents (bottom)
Seemingly innocuous panda image (top), file contents (bottom)
Source: AquaSec
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
In-Memory Execution and Persistence
Koske avoids writing to disk where possible. The shell script uses cron jobs and custom systemd services to maintain persistence. It also performs several hardening and evasion techniques:
- Overwrites
/etc/resolv.confwith hardcoded DNS entries (Cloudflare, Google) and locks the file usingchattr +i - Flushes
iptables - Bypasses proxies and brute-forces working ones using
curl,wget, and raw TCP - Cleans traces while downloading miners from GitHub
Rootkit Capabilities
The in-memory compiled C-based rootkit is designed to remain invisible to system monitoring tools. It:
- Hooks
readdir()to filter entries with strings likekoske,hideproc - Uses
/dev/shm/.hiddenpidto track and hide active process IDs - Operates entirely in user space with minimal footprint
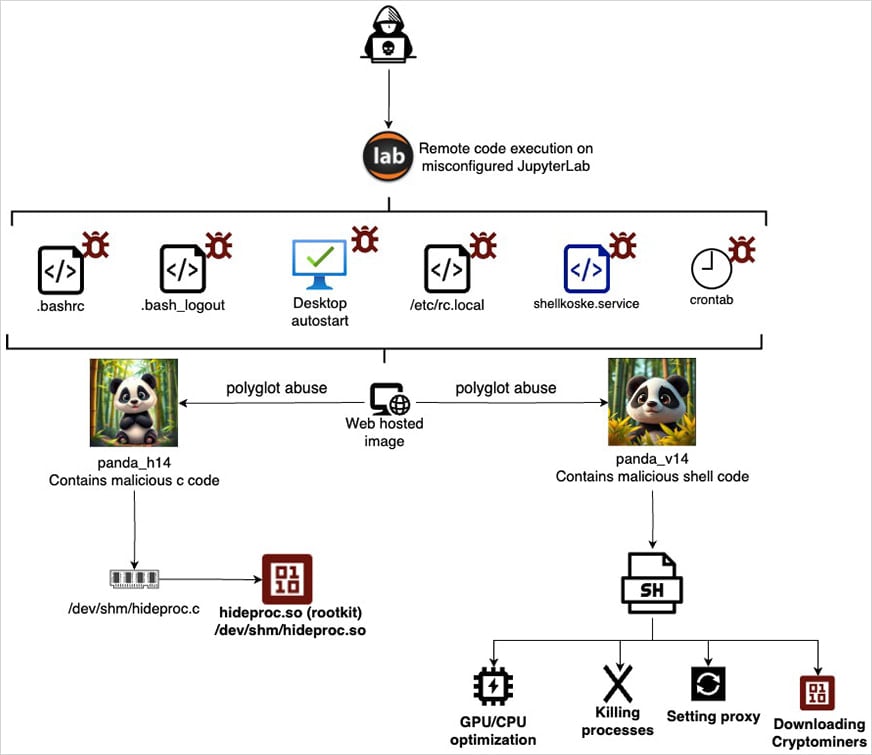 Complete attack chain
Complete attack chain
Source: AquaSec
Cryptomining at Scale
Koske’s primary monetization method is cryptojacking. It evaluates the host system’s CPU and GPU, then chooses the most efficient miner from 18 supported cryptocurrencies, including:
- Monero (XMR)
- Ravencoin (RVN)
- Zano (ZANO)
- Nexa (NEXA)
- Tari (TARI)
If a coin or pool is unreachable, Koske automatically switches to backups, maximizing uptime and resource usage.
Trending: Using Favicon for OSINT
Trending: Recon Tool: ZoomeyeSearch
AI Involvement Suspected
AquaSec researchers believe Koske may have been partially generated using large language models (LLMs) or automation frameworks, due to its highly modular design, advanced evasion techniques, and adaptive behavior.
The GitHub repositories used for miner delivery contain Serbian and Slovak-language traces, with IPs linked to Serbia. However, attribution remains inconclusive.
“The sophistication, automation, and adaptability suggest this malware may mark a turning point in the development of AI-assisted threats,” AquaSec noted.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













