LinkPro Rootkit: New eBPF-Backed GNU/Linux Backdoor Found in Compromised AWS Environments

Summary — what was found
Security researchers at Synacktiv investigated a compromise of AWS-hosted infrastructure and uncovered a sophisticated GNU/Linux rootkit dubbed LinkPro. The intruders gained initial access by exploiting an exposed Jenkins server vulnerable to CVE-2024-23897 and deployed a malicious Docker image (kvlnt/vv, since removed) to multiple Kubernetes clusters. LinkPro is a Golang backdoor that achieves kernel-level stealth and flexible command-and-control (C2) by installing two eBPF modules (Hide and Knock) and — when those fail — falling back to ld.so.preload tricks via a bundled libld.so. The backdoor supports both active (forward) and passive (reverse/knock-activated) modes and implements multiple transport protocols for C2.
Initial access and delivery chain
Synacktiv’s analysis shows the incident unfolded as follows:
- Attackers abused an exposed Jenkins server vulnerable to CVE-2024-23897 to get a foothold.
- They pushed a malicious Docker Hub image (
kvlnt/vv, Kali-based) onto Kubernetes nodes; the image contained:start.sh— startup script that launches SSH and the payloadslink— an open-source VPN/proxy (vnt) used to provide remote proxy access viavnt.wherewego[.]top:29872app— a Rust downloader (“vGet”) that fetches an encrypted vShell payload from an S3 bucket and connects back to C2 (56.155.98[.]37) over WebSocket
- Additional payloads dropped to nodes included a second vShell backdoor and LinkPro, the Golang rootkit.
LinkPro architecture & modes
LinkPro operates in two complementary modes:
- Forward (active) mode: the implant directly initiates connections to the operator’s C2 using one of five supported protocols — HTTP, WebSocket, UDP, TCP, or DNS.
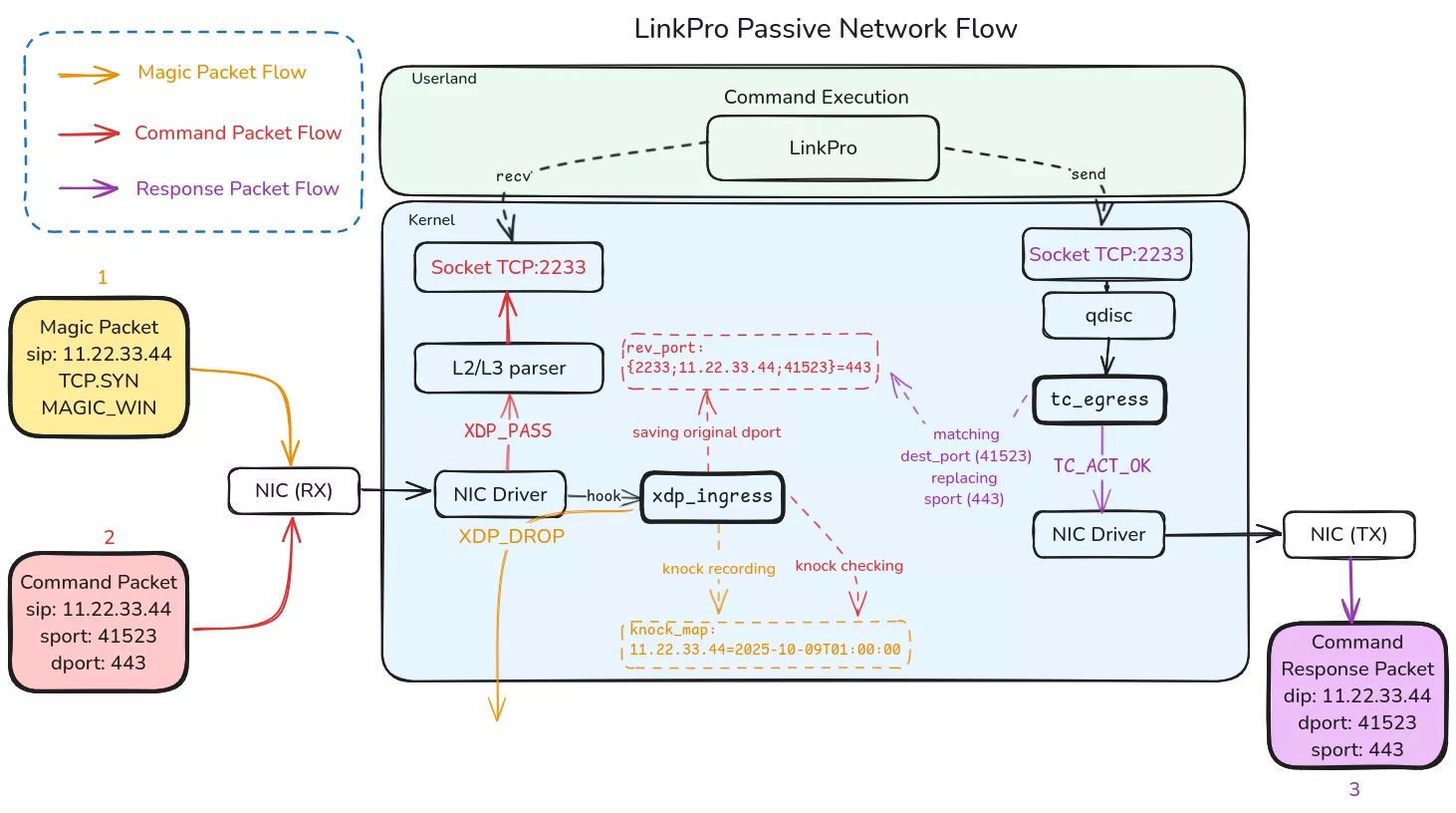
- Reverse (passive / knock) mode: LinkPro installs a Knock eBPF module that monitors incoming TCP traffic for a “magic packet” (TCP packet with window size = 54321). When detected, the Knock module saves the source IP and opens a one-hour window during which the operator can reach back to the host on an arbitrarily chosen port. The Knock module also rewrites packet headers (destination/source ports) to route operator packets to LinkPro’s internal listener (port 2333) while masking the original front-end firewall port — complicating log correlation.
Persistence is achieved by installing a systemd service, and if eBPF module installation fails or is disabled, LinkPro will install a shared library libld.so and add /etc/libld.so to /etc/ld.so.preload as a fallback stealth mechanism.
Stealth mechanisms — eBPF + ld.so.preload
LinkPro’s concealment is notable and multi-layered:
- Hide eBPF module: installs Tracepoint and Kretprobe eBPF programs that intercept system calls (e.g.,
getdents) to hide files/processes and interceptsys_bpfcalls to hide BPF programs themselves. This enables kernel-level hiding without modifying kernel modules. (This technique requires kernel configCONFIG_BPF_KPROBE_OVERRIDE; if absent, LinkPro uses the ld.so technique.) - Knock eBPF module: uses XDP and TC eBPF programs to detect and manipulate packets for the magic-packet activation and to rewrite ports transparently.
- /etc/ld.so.preload + libld.so: the fallback injects
libld.soviald.so.preloadso the library is loaded into all dynamically linked processes (e.g.,/usr/bin/ls).libld.sohooks libc functions to modify outputs (file lists, process listings, network sockets) so user-mode tools do not reveal the rootkit. On signal-based shutdowns (SIGHUP, SIGINT, SIGTERM) LinkPro removes eBPF modules and restoresld.so.preload.
Capabilities and operator features
LinkPro provides a compact but powerful command set to operators:
- Spawn interactive shells (
/bin/bashin a pseudo-TTY) - Execute arbitrary shell commands
- Enumerate files and directories, perform file I/O operations
- Download files to the host from attacker-controlled sources
- Establish SOCKS5 proxy tunnels for pivoting and proxying traffic through the compromised host
The initial deployment chain also included a vnt VPN/proxy component and a Rust downloader that fetched vShell payloads from cloud storage and established WebSocket C2 connections.
Offensive Security, Bug Bounty Courses
Network & operational evasion
Synacktiv highlights two operational evasion points worth noting:
- Magic-packet activation + port rewriting — allows operator access via allowed firewall ports and obfuscates correlation across perimeter logs and host activity.
- BPF-based hiding — conceals file and process artifacts at the kernel level and can intercept logging or tracing attempts; when kernel features aren’t available, the ld.so technique hides artifacts at userland via libc hooks.
Indicators (from the report)
Examples extracted from Synacktiv’s findings — treat these as starting points for triage.
- Malicious Docker image:
kvlnt/vv(removed from Docker Hub) - VPN/proxy domain:
vnt.wherewego[.]top:29872 - C2 WebSocket IP:
56.155.98[.]37 - Files observed in image:
start.sh,link,app(vGet downloader) - LinkPro artifacts:
libld.so(path installed via/etc/ld.so.preload), systemd service entries for persistence - LinkPro listening port: 2333 (internal) and proxied port experiments with 2233 used in header translations
- Kernel config of interest:
CONFIG_BPF_KPROBE_OVERRIDE(required for certain BPF hiding features)
Note: organizations should treat these IoCs as sensitive and combine them with their own telemetry. IPs/domains in attacker infrastructure can change quickly.
Trending: Offensive Security Tool: FormPoison
Detection and incident response guidance
Because LinkPro strives for kernel- and userland-level stealth, defenders should use diverse telemetry sources and assume user-space tools alone may be unreliable:
Immediate triage steps
- Isolate affected hosts and snapshot memory + disks for forensic analysis.
- Look for unexpected systemd services; check
/etc/ld.so.preloadfor unexpected entries and validate integrity of/lib/ld-linux*and related libraries. - Search for
libld.soand other unexpected shared libraries in system paths. - Inspect container images running on clusters for
kvlnt/vvor unknown images; review recent image pulls and Kubernetes deployment events. - Correlate front-end firewall logs for inbound traffic showing unusual port mappings around the magic packet heuristics (unusual TCP window size 54321 may be an indicator).
Hunting for BPF-based stealth
- Query kernel BPF program lists (
bpftool prog) on hosts (requires privileged access) and compare to a known-good baseline — note that LinkPro attempts to hide BPF programs, so this check should be performed from a trusted, forensic environment or offline snapshot where the attacker’s hooks cannot interfere. - Check kernel audit logs and dmesg for BPF program loads or XDP/TC changes.
- Use out-of-band monitoring (hypervisor/container runtime, host logs forwarded to remote SIEM) to detect discrepancies between process lists and observed sockets/connections.
Containment & remediation
- Revoke credentials that gave initial access (Jenkins service accounts, compromised VPN credentials, over-privileged AD service accounts). Rotate keys and tokens discovered in compromised repositories or configs.
- Rebuild compromised hosts from known-good images after wiping; do not rely on in-place cleanup if persistent kernel or loader hooks were active.
- Remove any malicious container images from registries and audit CI/CD pipelines and image build/deploy workflows for supply-chain abuse.
- If BPF programs were used and kernel integrity is suspect, update/reboot kernels and ensure kernel modules and configuration are restored from trusted sources.
- Rotate all credentials (SSH keys, API keys, cloud roles) that may have been exposed.
Mitigations & hardening recommendations
- Patch and harden CI/CD endpoints: close or patch exposed Jenkins instances (CVE-2024-23897) and limit unauthenticated access to build systems.
- Harden container registries and image pipelines: enforce image signing, scanning, and least-privilege deployment; restrict ability to pull arbitrary images.
- Harden Kubernetes clusters: use network segmentation, Pod Security Policies / OPA/Gatekeeper, restrict node access, and audit RBAC roles.
- Egress and firewall policies: enforce strict egress rules and log all NATed connections; consider TLS inspection where feasible to detect covert C2.
- BPF visibility: enable centralized kernel telemetry where possible and integrate BPF program load events into SIEM/wider monitoring.
- Immutable infrastructure: prefer rebuild-over-fix for systems suspected of kernel-level compromise.
- Credential hygiene: remove over-privileged service accounts, apply JIT/JEA, and rotate keys after compromise.
- Backup & recovery: ensure backups are offline/immutable and tested.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]













