Matrix Push C2 Emerges as Browser-Based C2 Platform Using Fake Notifications for Cross-Platform Attacks
Overview
Cybercriminals have begun exploiting browser push notifications as a new infectionless attack vector, powered by a malware-as-a-service (MaaS) command-and-control framework called Matrix Push C2.
This browser-native C2 platform enables attackers to distribute deceptive system-like alerts through Chrome, Edge, Firefox, and mobile browsers to deliver malicious links, phish credentials, and escalate access — all without installing malware first.
BlackFog researchers warn that Matrix Push C2 represents a major shift in social engineering, leveraging browser features themselves as a persistent foothold across Windows, macOS, Linux, Android, and iOS.

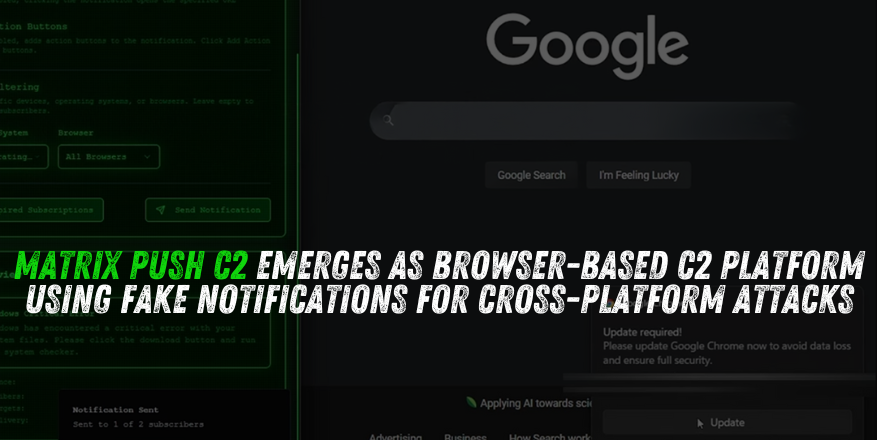
Matrix Push C2’s notifications panel
How the Attack Works
Matrix Push C2 exploits one key step:
Tricking users into enabling browser notifications
Attackers use malicious or compromised sites that pressure victims into clicking “Allow notifications”, sometimes disguised as:
- CAPTCHA checks
- Browser update prompts
- Video playback requirements
- Fake security warnings
Once the user accepts push notifications:
The browser becomes the C2 client
Attackers can now send persistent, OS-themed alerts directly to the user’s device, even when the malicious site is closed.
These fake alerts mimic trusted brands and operating-system dialogs, displaying messages like:
- “Suspicious activity detected — verify now”
- “Browser update required — click to install patch”
- “Your account is locked — sign in to restore access”
Each notification contains a malicious “Verify/Update” button redirecting to phishing or malware-delivery sites.
Because everything happens natively inside the browser, no initial malware download is required — similar in spirit to ClickFix, where victims unintentionally compromise themselves.
Offensive Security, Bug Bounty Courses
Why Matrix Push C2 Is Dangerous
1. Cross-platform persistence
Any device with a browser becomes a controllable endpoint, including:
- Windows & macOS desktops
- Linux workstations
- Android and iOS devices
- Chromebooks
- Enterprise-managed browsers
2. Completely fileless
No executable or script needs to be downloaded to establish communication.
3. Hard to detect
Security tools rarely monitor browser push notifications or C2 traffic that originates from them.
4. Attack escalation possible
Once notifications begin, attackers can:
- Steal credentials
- Phish for MFA codes
- Push malicious extensions
- Deploy malware via social engineering
- Drain crypto wallets
- Run browser exploit chains
Matrix Push C2 Business Model
The toolkit is fully commercialized as a subscription-based PhaaS platform, sold via Telegram and cybercrime forums.
Pricing:
- $150 / 1 month
- $405 / 3 months
- $765 / 6 months
- $1,500 / 12 months
Payments accepted in cryptocurrency.
Key Features:
- Web dashboard for sending notifications
- Real-time victim tracking
- Telemetry on which alerts are clicked
- Built-in URL shortener for cloaking links
- Extension inventory (including crypto-wallet extensions)
- Theming to mimic popular brands
Supported phishing templates include:
- MetaMask
- PayPal
- Netflix
- Cloudflare
- TikTok
These templates are designed to maximize credibility and drive user interactions.

Figure 6: Cloudflare-style phishing notification example
Trending: Offensive Security Tool: APKScope
Social Engineering at the Core
Attackers craft notifications that appear indistinguishable from legitimate operating system pop-ups.
Push Security notes the pages are heavily obfuscated:
- Invisible characters in UI text
- Images replacing textual UI elements
- Fragmented JavaScript to evade scanners
- Conditional delivery to hide malicious content from bots and researchers
This provides unusually strong evasion and makes detection by automated systems unlikely.
What Happens After Initial Access
Once a user is conditioned into interacting with Matrix Push notifications, attackers can escalate:
- Deploy phishing pages for credential theft
- Trick victims into installing secondary malware
- Execute browser-based exploit chains
- Perform reconnaissance on installed extensions
- Steal stored session tokens
- Push wallet-draining links to crypto users
BlackFog warns that this staged escalation mirrors modern “infectionless” attack models.
Growing Abuse of Legitimate Tools: Velociraptor Misuse
In parallel, Huntress reports a surge in threat actors misusing the legitimate Velociraptor DFIR tool as part of post-exploitation operations.
Recent intrusions involved:
- Initial access via WSUS vulnerability (CVE-2025-59287, CVSS 9.8)
- Deployment of Velociraptor for:
- User enumeration
- Service discovery
- System configuration mapping
The incident was contained before full compromise but highlights the trend:
attackers increasingly blend legitimate forensic tools with novel C2 frameworks to evade detection.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com, huntress.com, blackfog.com













