Nearly 76,000 WatchGuard Firebox Appliances Exposed — Critical IKEv2 RCE (CVE-2025-9242)

What happened
A critical vulnerability in WatchGuard’s Firebox appliances — CVE-2025-9242 — affects the IKEv2 handling process in Fireware OS and can be triggered without authentication by specially crafted IKEv2 packets, potentially enabling remote code execution. Internet-wide scans by The Shadowserver Foundation currently show roughly 75,800–76,000 exposed Firebox devices still vulnerable. Most are located in North America and Europe.
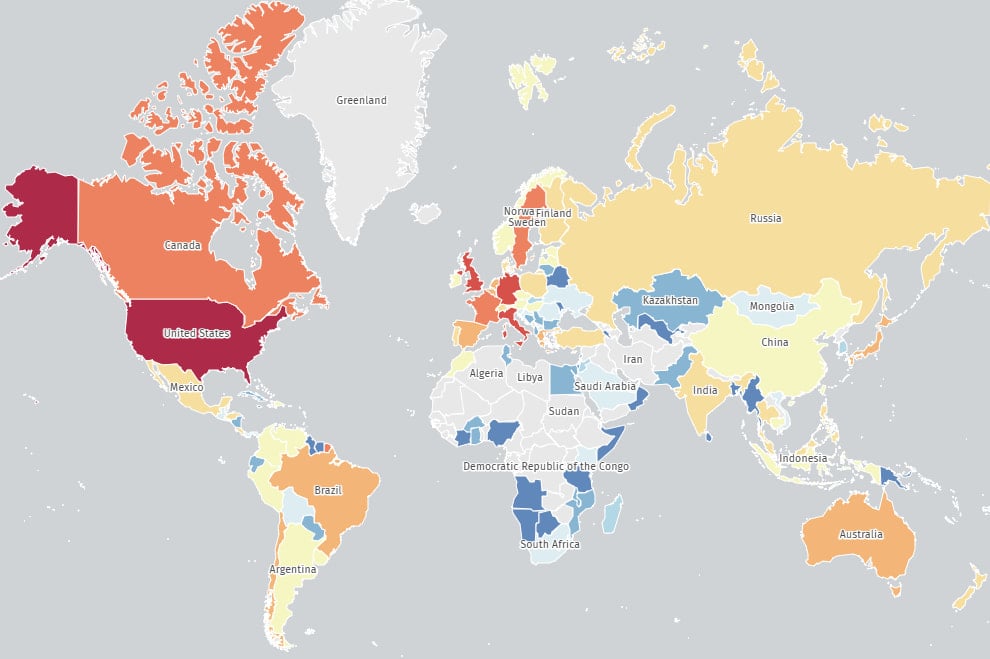 Heatmap of vulnerable Firebox devices
Heatmap of vulnerable Firebox devices
Source: The Shadowserver Foundation
The technical issue
CVE-2025-9242 is an out-of-bounds write in the iked process (the component responsible for IKEv2 VPN negotiations). An attacker can send crafted IKEv2 traffic to a vulnerable Firebox that accepts dynamic IKEv2 gateway peers, causing memory corruption and opening the door to arbitrary code execution on the device. The flaw carries a critical severity rating (WatchGuard scored it 9.3).
Affected Fireware releases include (non-exhaustive):
- 11.10.2 through 11.12.4_Update1 (note: 11.x is end-of-support)
- 12.0 through 12.11.3
- 2025.1
Offensive Security, Bug Bounty Courses
Scope & exposure
Shadowserver’s scans detected ~75,800–75,955 vulnerable Firebox appliances worldwide. Geographical distribution (approximate, per Shadowserver):
- United States: ~24,500 devices
- Germany: ~7,300
- Italy: ~6,800
- United Kingdom: ~5,400
- Canada: ~4,100
- France: ~2,000
These are production devices that frequently act as perimeter firewalls and VPN gateways, meaning successful exploitation could give attackers a powerful foothold into victim networks.
Vendor guidance & patched versions
WatchGuard published a security bulletin on September 17 and recommends upgrading to a fixed release. Suggested target versions include (pick the branch that matches your environment):
- 2025.1.1
- 12.11.4
- 12.5.13
- 12.3.1_Update3 (B722811)
Important: Version 11.x is end-of-support and will not receive further security updates — admins still on 11.x should migrate to a supported branch as soon as possible.
Temporary mitigations
If immediate patching is not possible, WatchGuard suggests workarounds depending on deployment:
- If the appliance is configured only with Branch Office (static gateway) VPNs, consider switching to the static-gateway configuration or follow vendor guidance for securing IPSec/IKEv2 to reduce exposure.
- Restrict inbound IKE/UDP 500 and NAT-T/UDP 4500 to trusted peers only — block or rate-limit IKE traffic from the public Internet where feasible.
- Use network-layer protections (NAT, firewall rules, IP allowlists) to ensure only expected endpoints can initiate IKE negotiations with your Firebox.
- Monitor device logs and WatchGuard Cloud for anomalous IKE negotiation patterns or unexpected peer connections.
These are stopgaps — patching to a fixed Fireware release is the only reliable remediation.
Trending: Obfuscation Tool: Flareprox
Immediate action checklist (recommended)
- Patch now — schedule and apply WatchGuard’s fixed Fireware builds (2025.1.1 / 12.11.4 / 12.5.13 / 12.3.1_Update3) as soon as possible.
- Isolate internet-exposed devices — if patching must wait, restrict IKE/UDP 500 and UDP 4500 ingress to trusted IPs only.
- Inventory — identify all Firebox appliances in your estate and confirm Fireware versions; treat any internet-facing, unpatched unit as high priority.
- Hunt for signs of compromise — review firewall logs, VPN sessions, configuration changes, and WatchGuard Cloud telemetry for unexpected reboots, new administrative users, modified rules, or unusual tunnels.
- Rotate credentials & keys — if you suspect compromise, rotate administrative credentials and any VPN shared secrets used by dynamic peers.
- Monitor Shadowserver/Threat intel — track public scanning reports and vendor advisories for evolving IoCs or exploit telemetry.
- Plan migration — move off end-of-life 11.x branches to supported Fireware versions to receive future security updates.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com,













