New ‘Defendnot’ Tool Silently Disables Microsoft Defender Using Fake AV Registration

New ‘Defendnot’ Tool Disables Microsoft Defender by Masquerading as a Valid Antivirus
Security researcher es3n1n has released a new tool dubbed Defendnot, which can silently disable Microsoft Defender by spoofing the presence of a legitimate antivirus product—even on systems where no actual third-party AV is installed.
The technique leverages an undocumented Windows Security Center (WSC) API, which is typically used by antivirus vendors to register their security software with Windows. When such a product is detected, Windows automatically disables Microsoft Defender to prevent conflicts between multiple AV engines.
How It Works
Defendnot exploits this logic by registering a fake antivirus product that passes all of Windows’ validation checks. This effectively tricks Windows into deactivating Defender under the assumption that another security solution is in place.
The tool builds upon a previous project called no-defender, which spoofed antivirus registration by reusing code from a third-party security vendor. That earlier tool was removed from GitHub after a DMCA takedown.
“After the release, the project blew up… the developers of the antivirus I was using filed a DMCA takedown… so I erased everything and called it a day,” the developer explained in a blog post.
To avoid copyright issues, Defendnot was rebuilt from scratch, using a custom dummy antivirus DLL.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Trusted Process Injection and PPL Bypass
Ordinarily, WSC API registration requires Protected Process Light (PPL) status and valid digital signatures, ensuring only legitimate AV products can interact with Windows Security Center.
Defendnot bypasses these safeguards by injecting its DLL into Taskmgr.exe, a signed and trusted system process. From inside this process, it registers itself as an AV product under a spoofed name.
Once registration is complete, Microsoft Defender shuts itself down—effectively leaving the system with no active security protection.
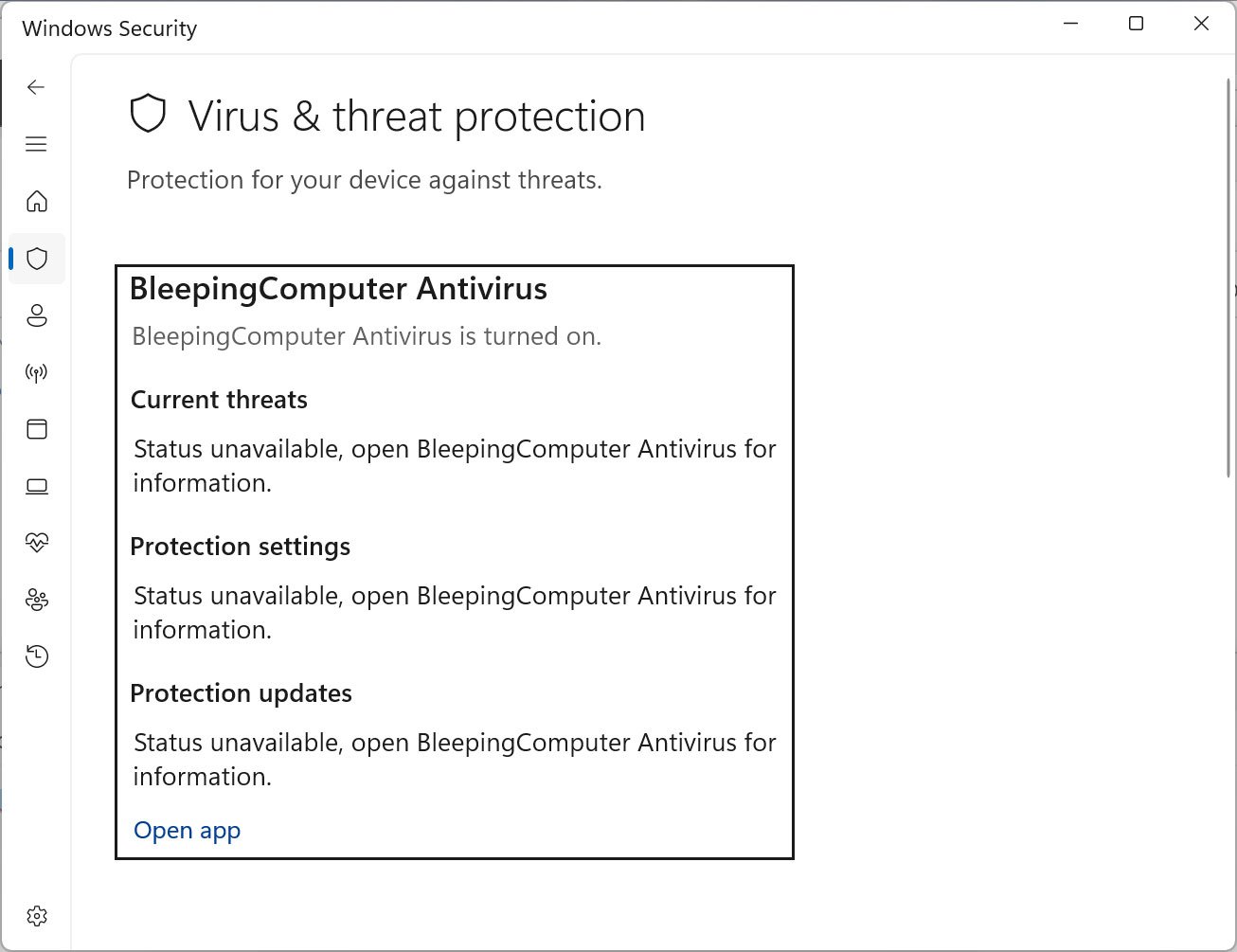 Defendnot registered on a device
Defendnot registered on a device
Source: BleepingComputer
Additional Capabilities
- Custom configuration: The tool uses a ctx.bin file to pass options like AV display name, logging verbosity, and whether to disable registration.
- Persistence: It sets up an autorun task via Task Scheduler, ensuring it launches automatically at each login.
Trending: Major Cyber Attacks that shaped 2024
Detection and Response
While Defendnot is presented as a research project, it highlights a dangerous weakness in how Windows trusts AV registration. It demonstrates how trusted system processes and undocumented APIs can be abused to neutralize built-in protections.
Microsoft Defender has begun detecting the tool under the name Win32/Sabsik.FL.!ml, and will quarantine it if found.
Trending: ClickFix Malware Campaign Now Hits Linux
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com