New macOS ‘Sploitlight’ Flaw Bypasses Privacy Controls to Exfiltrate Sensitive Data

Apple has patched a critical macOS vulnerability that allowed attackers to bypass Transparency, Consent, and Control (TCC) protections and access highly sensitive user data, including information cached by Apple Intelligence.
The flaw, tracked as CVE-2025-31199 and dubbed “Sploitlight” by Microsoft researchers, exploited Spotlight plugin behavior to evade privacy controls and harvest detailed user information. It was addressed in March 2025 with macOS Sequoia 15.4 through “improved data redaction.”
Exploiting Spotlight for Privileged Access
TCC is a macOS security framework that restricts how apps access sensitive user data such as location, photos, calendar, and contacts. It requires explicit user consent before apps can access protected resources.
Microsoft’s researchers — Jonathan Bar Or, Alexia Wilson, and Christine Fossaceca — discovered that Spotlight plugins could be leveraged to execute code with elevated privileges, bypassing TCC’s protections and accessing files normally restricted to apps with Full Disk Access.
“While similar to prior TCC bypasses like HM-Surf and powerdir, the implications of Sploitlight are more severe,” Microsoft stated. “It enables exfiltration of Apple Intelligence cache and remote information from iCloud-linked devices.”
What Attackers Could Steal
The potential impact of the vulnerability is extensive. Attackers could steal:
- Precise geolocation data
- Photo and video metadata
- Face and person recognition data
- Photo albums and shared libraries
- Search history and user preferences
- Deleted photos and videos
- Remote data from iCloud-linked devices
The vulnerability exploited a “logging issue,” as described by Apple, but Microsoft showed that the underlying mechanism allowed the unauthorized execution of code that interacted directly with sensitive system components.
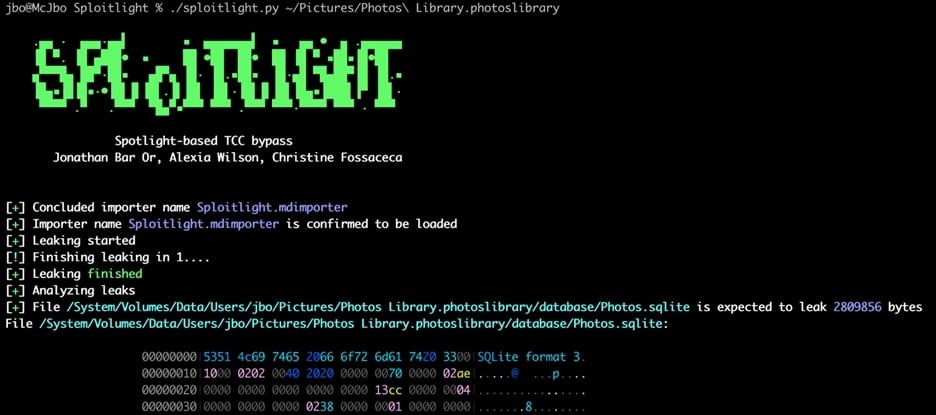 Spoitlight exploit (Microsoft)
Spoitlight exploit (Microsoft)
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
No User Interaction Needed
Because Spotlight is a core macOS service, attackers could exploit Sploitlight without requiring user interaction, using weaponized plugins to abuse the privileged context.
Even worse, the TCC framework was unaware of the access, making the intrusion stealthy and difficult to detect or log.
Previous TCC and macOS Bypasses
This is not the first time Microsoft has uncovered flaws in Apple’s security layers. Past notable macOS vulnerabilities include:
- CVE-2020-9771 – Time Machine mount-based TCC bypass
- CVE-2021-30713 – Bundle conclusion issue
- CVE-2021-30970 (powerdir) – Custom TCC database injection
- CVE-2023-32369 (Migraine) – SIP bypass for rootkit installation
- CVE-2024-44243 – Kernel driver injection via third-party extensions
Microsoft’s Warning
Microsoft emphasized the growing risks associated with these kinds of vulnerabilities:
“These risks are further complicated and heightened by the remote linking capability between iCloud accounts, meaning an attacker could also determine remote information of other devices linked to the same iCloud account.”
In other words, compromising one macOS system may allow attackers to gain partial insight into all devices connected to the same Apple ID.
Trending: Offensive Security Tool: APKScope
Apple’s Fix and Recommendations
Apple quietly addressed the issue in macOS Sequoia 15.4 in March 2025 by improving redaction mechanisms and restricting Spotlight plugin behavior.
Organizations and users are advised to:
- Update to macOS 15.4 or later immediately
- Audit third-party software using Spotlight integrations
- Monitor for unusual plugin behavior
- Use Apple’s system integrity and privacy logs to detect anomalous access
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













