New Phishing Kits Automate MFA Bypass, AI Email Lures, and Bank Credential Theft at Scale

A Growing Ecosystem of Modular Phishing Kits
BlackForce, GhostFrame, InboxPrime AI, and Spiderman join a rapidly expanding ecosystem of phishing frameworks such as Tycoon 2FA, Salty 2FA, Sneaky 2FA, Cephas, Whisper 2FA, and others.
Researchers from ANY.RUN recently observed a hybrid Salty–Tycoon phishing chain, where one kit seamlessly falls back to another when infrastructure fails. This blending of frameworks complicates detection, weakens kit-specific signatures, and gives attackers greater resilience.
“This overlap marks a meaningful shift that complicates attribution and enables attackers to slip past early detection,” ANY.RUN noted.
BlackForce: MFA Bypass via Man-in-the-Browser
First observed in August 2025, BlackForce is a phishing kit designed to steal credentials and bypass multi-factor authentication using Man-in-the-Browser (MitB) techniques. Sold on Telegram for €200–€300, the kit is actively maintained and frequently updated.
Researchers from Zscaler ThreatLabz report that BlackForce has been used to impersonate more than 11 major brands, including Disney, Netflix, DHL, and UPS.
Key capabilities include:
- Real-time credential capture via Telegram bots and a web-based C2 panel
- Fake MFA prompts injected through MitB techniques to harvest one-time passwords (OTPs)
- JavaScript “cache-busting” filenames (e.g.,
index-[hash].js) to evade detection - Blocklists to filter out security scanners, crawlers, and analysis tools
After credentials and MFA codes are captured, victims are quietly redirected to the legitimate website, reducing suspicion and hiding evidence of compromise.

GhostFrame: Stealth Phishing at Massive Scale
Discovered in September 2025, GhostFrame is a lightweight yet highly effective phishing kit that has already been linked to over one million stealth phishing attempts.
At its core, GhostFrame uses a benign-looking HTML page that hides malicious behavior inside an embedded iframe, which loads the actual phishing content.
Notable features:
- Targets Microsoft 365 and Google accounts
- Randomized subdomains on each visit to evade blocking
- Anti-debugging and anti-analysis to block browser inspection
- Dynamic modification of page titles, favicons, and redirects
- Fallback iframes if the primary loader fails
The separation between the visible outer page and the malicious iframe allows attackers to rapidly swap phishing payloads without changing the main delivery page, complicating detection.
Offensive Security, Bug Bounty Courses
InboxPrime AI: Phishing as a Fully Automated Service
InboxPrime AI represents a shift toward AI-driven phishing automation. Marketed via a Telegram channel with roughly 1,300 members, the kit is sold for $1,000 under a malware-as-a-service model that includes a perpetual license and full source code.
According to Abnormal Security, InboxPrime AI is built to mimic legitimate email marketing platforms while automating nearly every stage of phishing campaigns.
Core functionality includes:
- AI-generated phishing emails, including subject lines and tone selection
- Gmail web interface abuse to improve inbox placement
- Spintax support to generate unique message variations
- Sender identity spoofing and display-name randomization
- Real-time spam diagnostics with suggested fixes
By removing the need for manual email writing, InboxPrime AI dramatically lowers the barrier to entry and enables high-volume, professional-looking phishing operations.

A closer look at the tool’s tone adjustment options, which enable attackers to tailor phishing emails to specific communication styles. – abnormal.ai
Spiderman: Banking-Focused Phishing Across Europe
The Spiderman phishing kit targets customers of European banks and financial platforms, including Deutsche Bank, ING, Commerzbank, CaixaBank, Klarna, PayPal, and others.
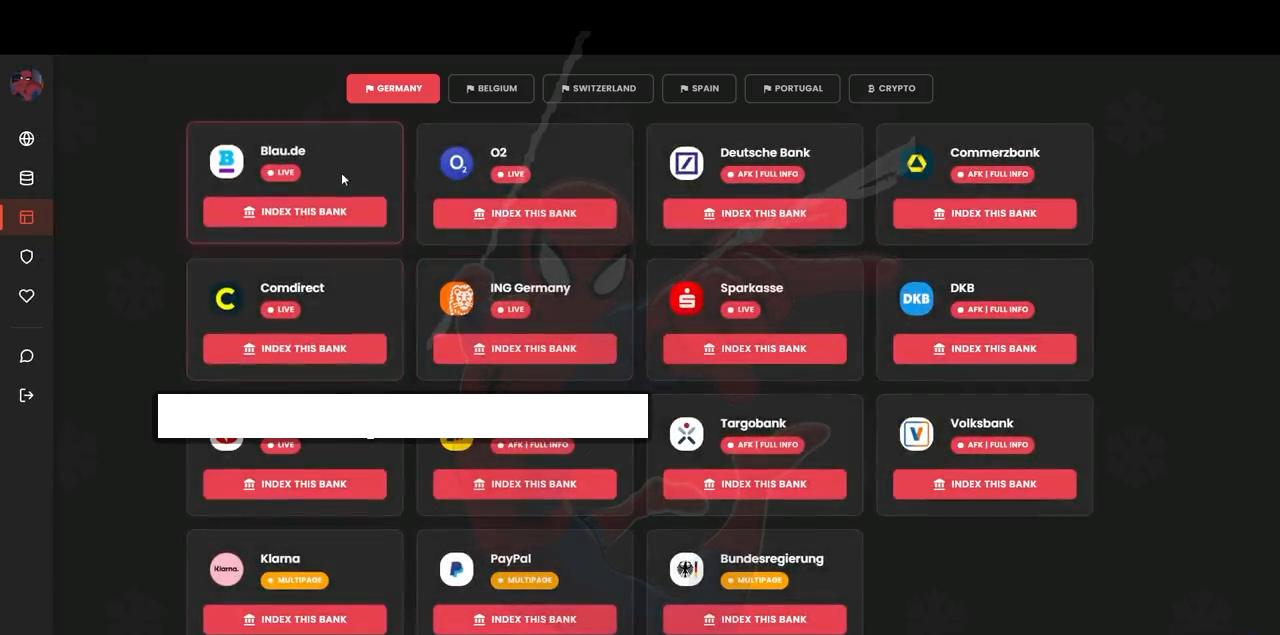
Unlike many kits sold via Telegram, Spiderman is marketed through a Signal group with approximately 750 members, with a focus on Germany, Austria, Switzerland, and Belgium.
Capabilities include:
- Pixel-perfect replicas of banking and government portals
- OTP and PhotoTAN interception
- Credit card data harvesting
- Cryptocurrency wallet seed phrase theft
- ISP allowlisting, geofencing, and device filtering
Each victim session is tracked with a unique identifier, allowing attackers to maintain continuity through multi-step fraud workflows common in European banking environments.
Trending: Using Favicon for OSINT
The Bigger Picture
Together, these kits highlight the industrialization of phishing:
- MFA bypass is now standard
- AI removes the need for human-crafted lures
- Regional and brand-specific targeting is turnkey
- Detection evasion is built-in by default
For defenders, this means higher attack volume, faster campaign turnover, and more realistic phishing content, all without a corresponding increase in attacker effort.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Sources: thehackernews.com













