Over 100 Popular Brands Impersonated in Massive Phishing Campaign

A far-reaching campaign involving the impersonation of over a hundred renowned apparel, footwear, and clothing brands has been discovered, with cybercriminals tricking individuals into providing their account credentials and financial information on fraudulent websites.
Among the targeted brands are Nike, Puma, Asics, Vans, Adidas, Columbia, Superdry Converse, Casio, Timberland, Salomon, Crocs, Sketchers, The North Face, UGG, Guess, Caterpillar, New Balance, Fila, Doc Martens, Reebok, Tommy Hilfiger, and others.
The campaign, uncovered by Bolster’s threat research team, relies on approximately 3,000 domains and nearly 6,000 websites, including both active and inactive ones.
Bolster reports a significant surge in activity between January and February 2023, with around 300 new fake sites emerging each month.
The domain names follow a consistent pattern, incorporating the brand name alongside a city or country, followed by a generic top-level domain (TLD) such as “.com.”
Researchers found that the campaign involved more than ten fake websites for popular brands like Nike, Puma, and Clarks, closely resembling the design of the official brand websites.
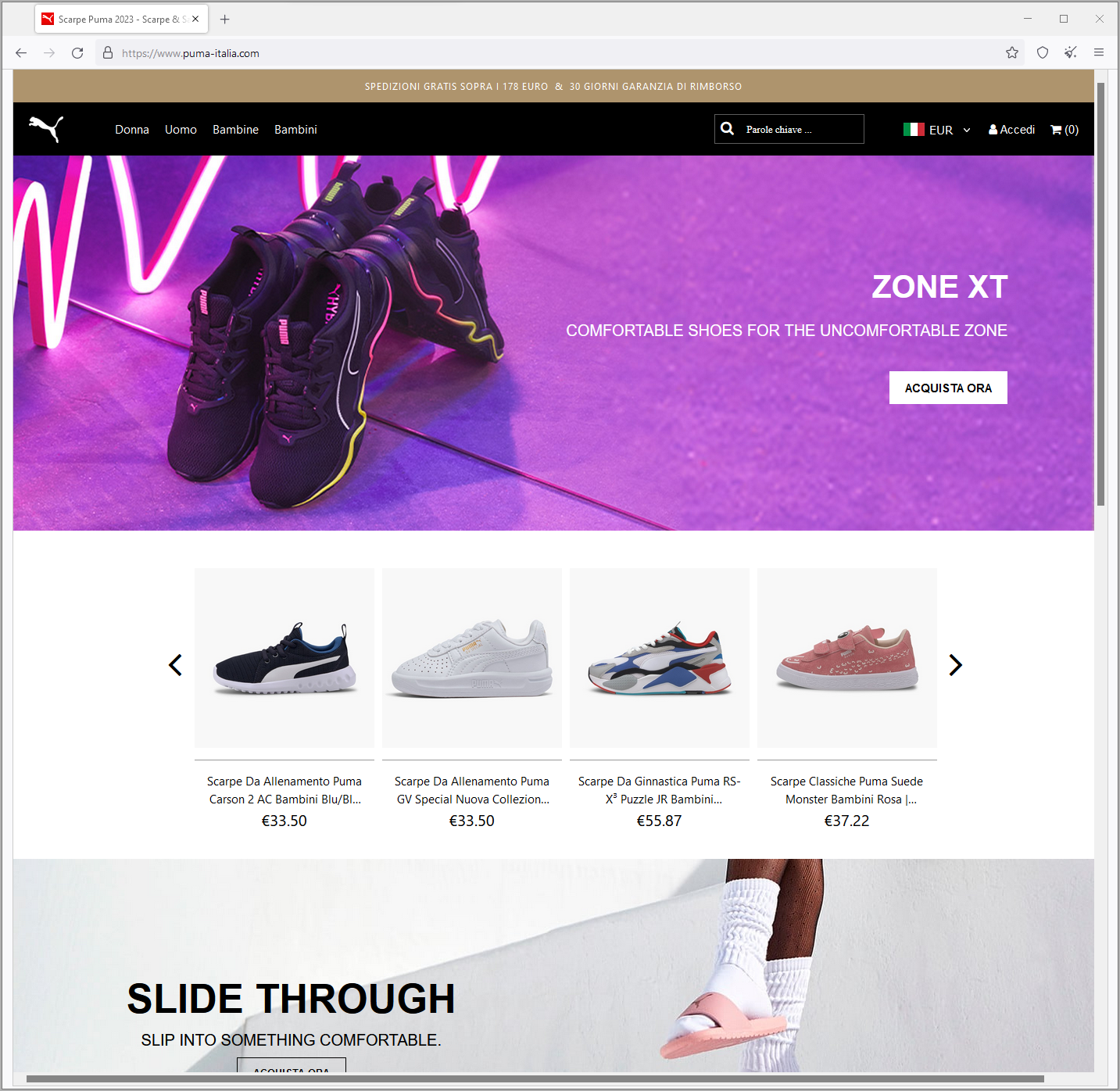 Fake Puma site targeting Italians (BleepingComputer)
Fake Puma site targeting Italians (BleepingComputer)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
These fraudulent domains were traced back to the Autonomous System number AS48950 and were hosted by two internet service providers: Packet Exchange Limited and Global Colocation Limited.
Most of the domains were registered through Alibaba.com Singapore, with domain ages ranging from two years to 90 days.
The age of a domain is a critical factor in phishing operations, as the longer a domain remains innocuous, the less likely it is to be flagged by security tools as suspicious.
This campaign’s effectiveness lies in its ability to exploit domain age, with several malicious domains avoiding detection long enough to be indexed by Google Search, potentially ranking high for specific search terms.
High rankings in Google Search add an air of credibility and trustworthiness, making it more likely for unsuspecting users to visit these phishing sites.
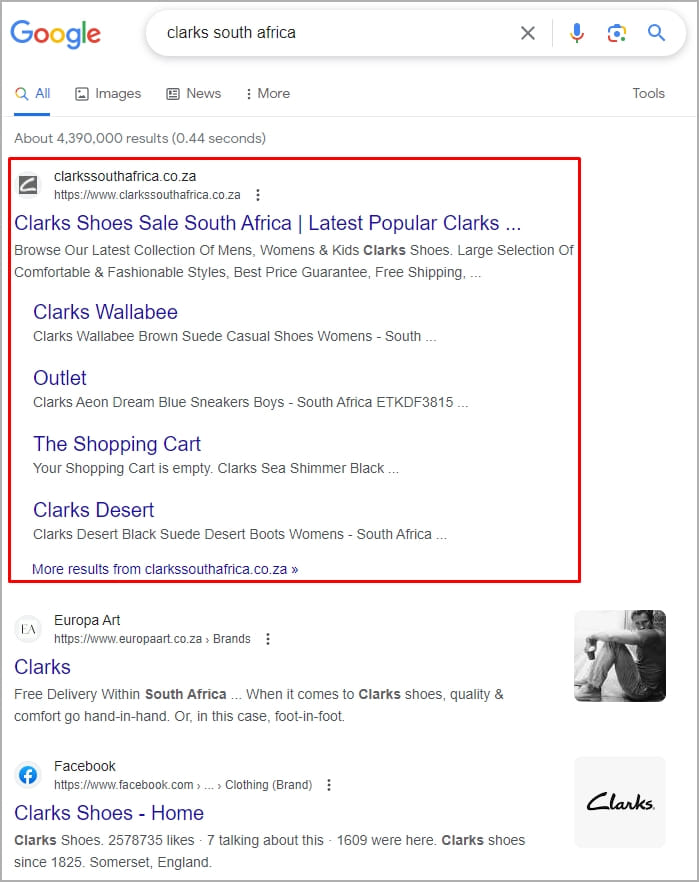 Bogus Clarks site ranking first in Google Search
Bogus Clarks site ranking first in Google Search
(BleepingComputer)
BleepingComputer conducted a thorough investigation of these sites and discovered that they were not hastily constructed clones. They featured realistic “About Us” pages, provided contact details, and their order pages appeared genuine, making them challenging to identify as suspicious.
Trending: Offensive Security Tool: Pypykatz
The precise scam tactics employed in this campaign remain undisclosed, but Bolster suggests that the sites either fail to deliver the products customers purchase or ship counterfeit goods from China.
Furthermore, any information entered on the checkout pages, notably credit card details, may be stored by the website operators and later sold to cybercriminals.
To protect yourself, it is advisable to avoid clicking on promoted results in Google Search when searching for official brand websites. If in doubt, verify the legitimate URL by consulting the brand’s Wikipedia page or official social media channels.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com









