Sh1mmer: A New Exploit Enables Unenrollment of Enterprise-Managed Chromebooks

Reading Time: 3 Minutes
‘Sh1mmer’ exploit
A new exploit called ‘Sh1mmer’ allows users to unenroll enterprise-managed Chromebooks and bypass device restrictions. The exploit was developed by security researchers from the Mercury Workshop Team and requires a publicly leaked RMA shim that the Sh1mmer exploit will modify.
When Chromebooks are enrolled with a school or enterprise, they are managed by policies established by the organization’s administrators.
This allows administrators to force-install browser extensions, apps, and to restrict how a device can be used. However, the Sh1mmer exploit lets users unenroll their Chromebooks from enterprise management.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Exploit specifics
The exploit requires a publicly leaked RMA shim, which is a disk image stored on USB devices containing a combination of the Chrome OS factory bundle components used to reinstall the operating system and manufacturer tools for repair and diagnostics.
The researcher’s online builder is used to inject the RMA shim with the Sh1mmer exploit, and then the Chrome Recovery utility is run. The Sh1mmer menu is then launched, where the user can unenroll and re-enroll the device, enable USB boot, allow root-level access to the operating system, and more.
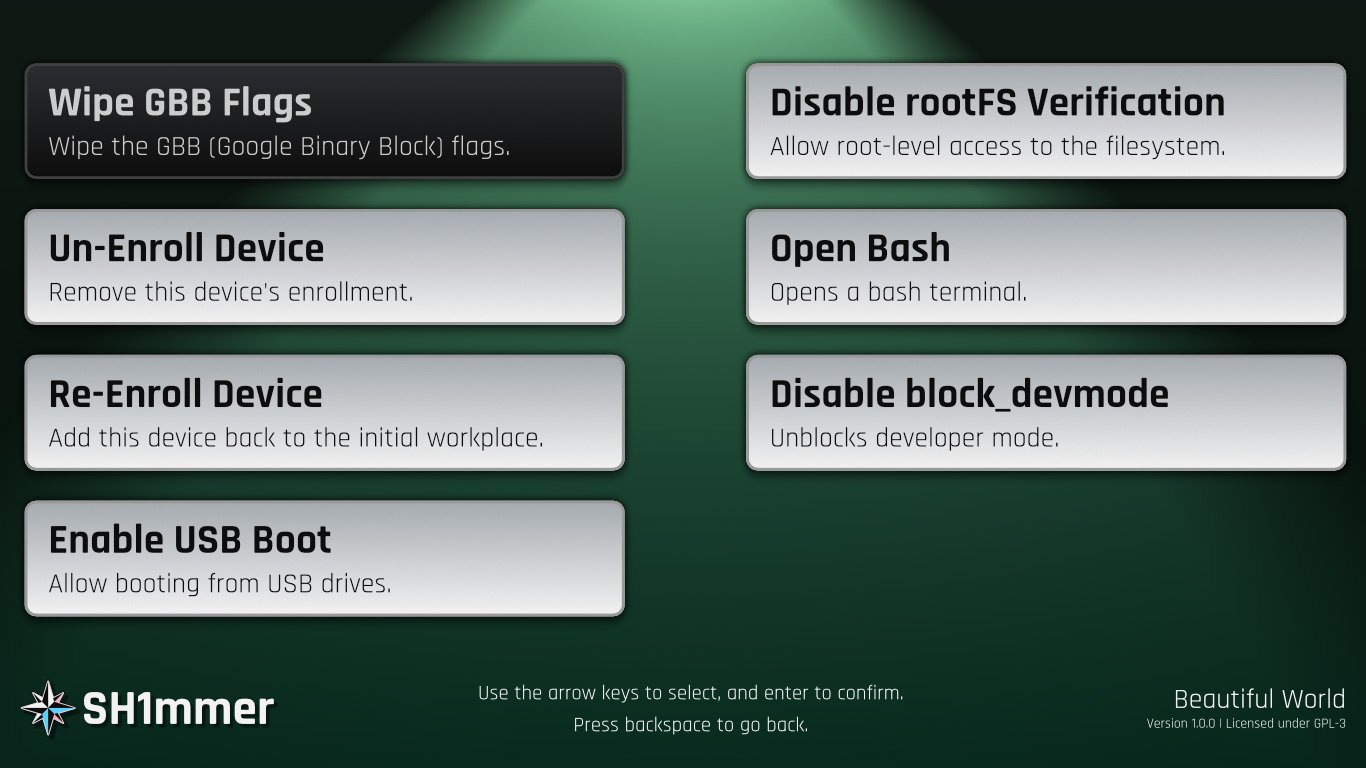 Sh1mmer exploit menu – source bleepingcomputer.com
Sh1mmer exploit menu – source bleepingcomputer.com
Trending: Offensive Security Tool: XSSRocket
Google is aware, but no prevention or detection is provided for the exploit
Google has stated that they are aware of the issue and are working with hardware partners to address it, although they have not provided information on how administrators can prevent the exploit or detect exploited devices.
When the Sh1mmer exploit is used, the device will show up as inactive in the administration console, which administrators can enable inactive device notifications for to receive emails when a device becomes inactive, allowing them to look into it further and determine if the exploit was used. Some members of the k12sysadmin Reddit group have warned that the use of the Sh1mmer exploit likely breaks student code of conduct and could lead to serious consequences, such as having the school confiscate the Chromebook and removing the student’s district use of technology for a year.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com









