Sneaky2FA Phishing Kit Adds Browser-in-the-Browser (BitB) to Steal Microsoft 365 Sessions
Overview
The Sneaky2FA phishing-as-a-service (PhaaS) platform has added a significant new capability to its Microsoft 365 credential-theft toolkit: browser-in-the-browser (BitB) fake login windows. This enhancement dramatically increases the realism of phishing attacks and enables attackers to steal both passwords and active authenticated sessions, even when multi-factor authentication (MFA) is enabled.
Push Security’s new analysis shows Sneaky2FA joining Tycoon2FA and Mamba2FA as the latest PhaaS service to adopt more advanced, MFA-bypassing social-engineering tactics.
What BitB Brings to Sneaky2FA
Sneaky2FA was already a sophisticated kit, known for:
- SVG-based phishing pages
- Attacker-in-the-middle (AitM) reverse proxying
- Session-token theft, not just password capture
But the addition of BitB fake pop-ups brings a new level of visual deception to its attacks.
How BitB Works
Originally created as a concept by researcher mr.d0x in 2022, BitB creates a fake login window rendered inside the original browser page. It:
- Mimics a standalone browser pop-up
- Displays a fake URL bar showing the legitimate domain (e.g., login.microsoftonline.com)
- Is styled to perfectly match the victim’s OS and browser (Edge on Windows, Safari on macOS)
- Uses an iframe to host the malicious login form
Because the fake URL bar appears authentic, victims believe they’re entering credentials directly into the official Microsoft pop-up.
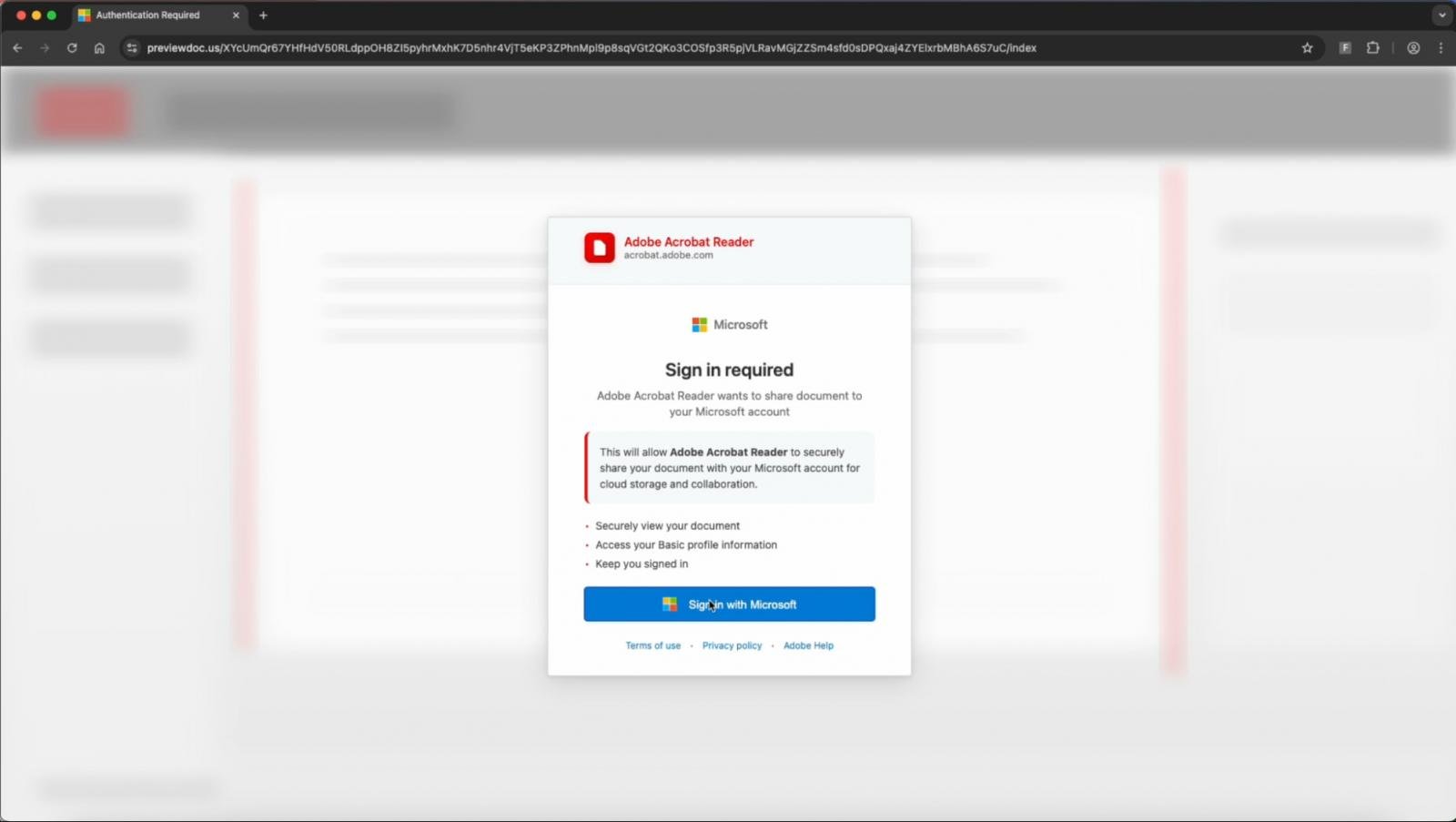 Deceptive prompt leading to phishing
Deceptive prompt leading to phishing
Source: Push Security
Offensive Security, Bug Bounty Courses
Inside a Sneaky2FA Attack
The current attack chain involves:
- Victim receives a phishing link hosted on previewdoc[.]com.
- They pass a Cloudflare Turnstile bot check, increasing trust and evading automated scanners.
- They are prompted to “Sign in with Microsoft” to view a document.
- Clicking the sign-in button triggers the BitB fake login pop-up.
- Sneaky2FA loads its reverse-proxy Microsoft login flow inside the pop-up, stealing:
- Microsoft 365 credentials
- Active session tokens (bypassing MFA)
- Attackers authenticate immediately into the victim’s account.
BitB here is mainly a cosmetic layer that drastically improves the believability of Sneaky2FA’s AitM infrastructure.
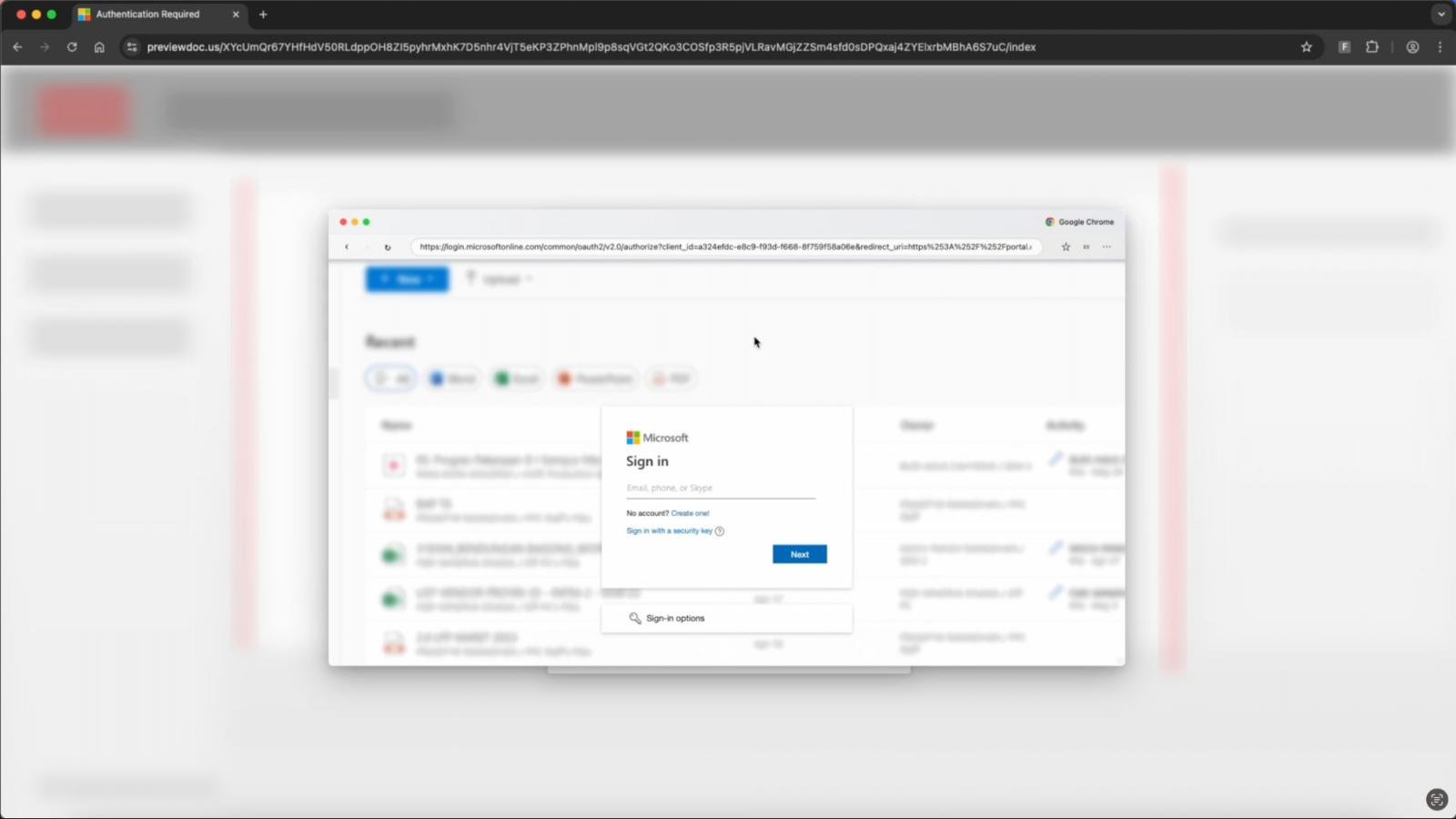 The fake window
The fake window
Source: Push Security
Stealth and Evasion Capabilities
Sneaky2FA’s phishing infrastructure is heavily optimized for evading browser protections, scanners, and security crawlers.
Push Security highlights several evasion techniques:
- Conditional loading (bots and researchers get benign pages)
- HTML/JS obfuscation, such as invisible characters inserted into UI text
- Microsoft interface elements stored as encoded images, not text
- Dynamic adaptation to OS, browser, and screen size
- Session-based logic to avoid automated detection and fingerprinting
The pages are designed to be nearly undetectable by standard anti-phishing solutions.
How to Identify a Fake BitB Pop-Up
Because BitB pop-ups look extremely convincing, Push Security recommends two key detection methods:
Try dragging the window outside the parent browser
A real browser pop-up is a separate OS-level window.
A fake BitB pop-up cannot leave the bounds of the original page.
Check the taskbar
Real pop-up windows create a separate browser instance icon.
Fake BitB pop-ups do not.
Trending: Recon Tool: ZoomeyeSearch
Rising Trend: BitB in PhaaS Platforms
Sneaky2FA is not the first kit to adopt BitB.
Push Security notes widespread adoption across:
- Raccoon0365 / Storm-2246 (recently dismantled by Microsoft & Cloudflare)
- Tycoon2FA
- Mamba2FA
All three target Microsoft 365 due to the high-value access it grants attackers.
The integration of BitB signals a broader shift in PhaaS services toward MFA-resistant phishing, leveraging reverse-proxying and realistic UI deception to compromise enterprise cloud accounts.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com, pushsecurity.com/blog













