Sni5Gect Attack Framework Can Downgrade 5G Connections Without Rogue Base Stations

Researchers Develop Novel 5G Attack
A team of academics from the ASSET Research Group at Singapore University of Technology and Design (SUTD) has introduced a new attack method that can downgrade a 5G connection to older generations—without relying on a rogue base station.
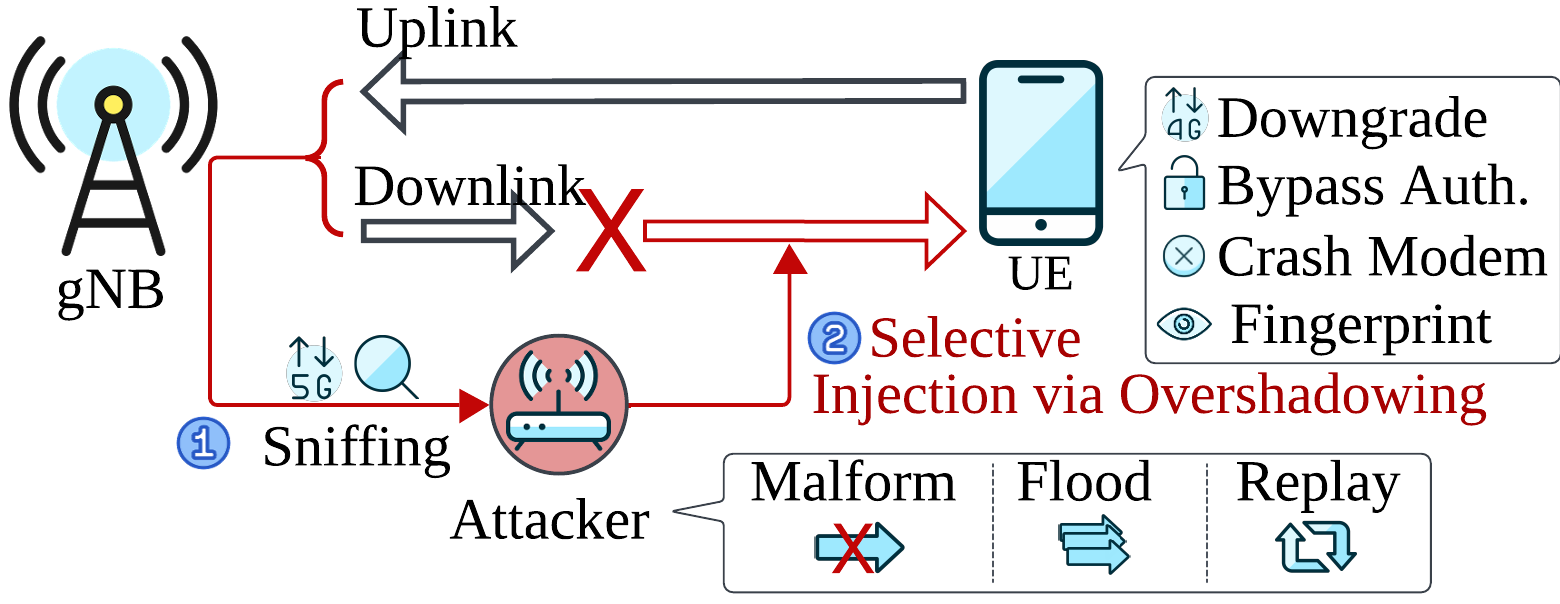
Their tool, called Sni5Gect (short for Sniffing 5G Inject), is an open-source software toolkit capable of sniffing unencrypted messages exchanged between a 5G base station (gNB) and a mobile device (UE). It can then inject malicious messages over-the-air to manipulate the communication.
Capabilities of Sni5Gect
The framework enables several types of attacks, including:
- Downgrading devices to earlier generations (e.g., 4G)
- Crashing the modem of the victim device
- Fingerprinting and authentication bypass
Unlike traditional 5G attack models that depend on rogue base stations, Sni5Gect works as a third-party sniffer. It silently monitors traffic, tracks protocol states during the UE attach process, and injects targeted payloads during the unencrypted pre-authentication phase.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Building on Prior 5G Research
The findings build upon ASSET’s 2023 research, which uncovered 14 flaws in 5G modem firmware from MediaTek and Qualcomm, collectively named 5Ghoul. Those flaws allowed attackers to drop connections, freeze modems, and force downgrades from 5G to 4G.
Sni5Gect extends this research by showing that attackers don’t even need compromised base stations to succeed—they can exploit the brief communication window before encryption kicks in.
Downgrade and Exploitation Potential
During this early phase of 5G communication, attackers can:
- Crash the modem on a victim’s phone
- Fingerprint the device for tracking
- Downgrade connections to 4G, a protocol with well-documented vulnerabilities that can be abused for location tracking and further exploitation
In practical tests, the attack achieved:
- 80% accuracy in sniffing uplink/downlink traffic
- 70–90% injection success rate
- From a distance of up to 20 meters (65 feet)
Tested devices included the OnePlus Nord CE 2, Samsung Galaxy S22, Google Pixel 7, and Huawei P40 Pro.
Trending: Recon Tool: WaybackLister
Industry Response and Security Implications
The GSMA (Global System for Mobile Communications Association) has acknowledged the threat, assigning it CVD-2024-0096.
The researchers stress that Sni5Gect is not only a tool for demonstrating vulnerabilities but also a framework for future 5G security research, intrusion detection, and mitigation strategies.
They conclude that this work highlights the need for stronger packet-level security mechanisms in 5G and future wireless standards.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com














