Study Uncovers Vulnerabilities in ChatGPT Plugins, Risking Data Exposure and Account Takeover

A recent analysis conducted by researchers has unearthed a series of vulnerabilities within ChatGPT plugins, shedding light on potential risks associated with data exposure and account takeovers. The investigation, spearheaded by Salt Security, examined various ChatGPT plugins, uncovering critical flaws that could compromise user security.
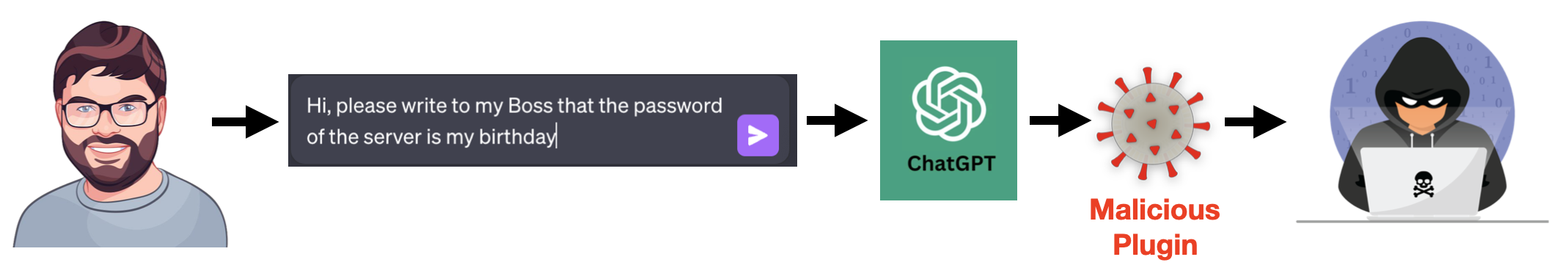
ChatGPT plugins serve as supplementary tools or extensions designed to augment the functionality and user experience of ChatGPT. These additions encompass a wide array of features, ranging from enhanced natural language processing capabilities to seamless integrations with various platforms and services. Essentially, plugins offer users the flexibility to tailor their ChatGPT experience to suit specific requirements.

Vulnerabilities
One of the vulnerabilities identified by the researchers pertains to OAuth authentication within ChatGPT, presenting a loophole that could facilitate the installation of malicious plugins on unsuspecting users’ accounts. Exploiting this vulnerability enables attackers to deploy custom-built plugins, thereby gaining unauthorized access to sensitive data exchanged in private chats, including credentials and passwords.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Another critical vulnerability, described as a zero-click account takeover, affects multiple plugins and poses a significant threat to organizational security. Leveraging this flaw, attackers can seize control of accounts associated with third-party platforms like GitHub. Notably, the vulnerability was observed in the AskTheCode plugin developed by PluginLab.AI, allowing attackers to infiltrate GitHub repositories of users utilizing this particular plugin.
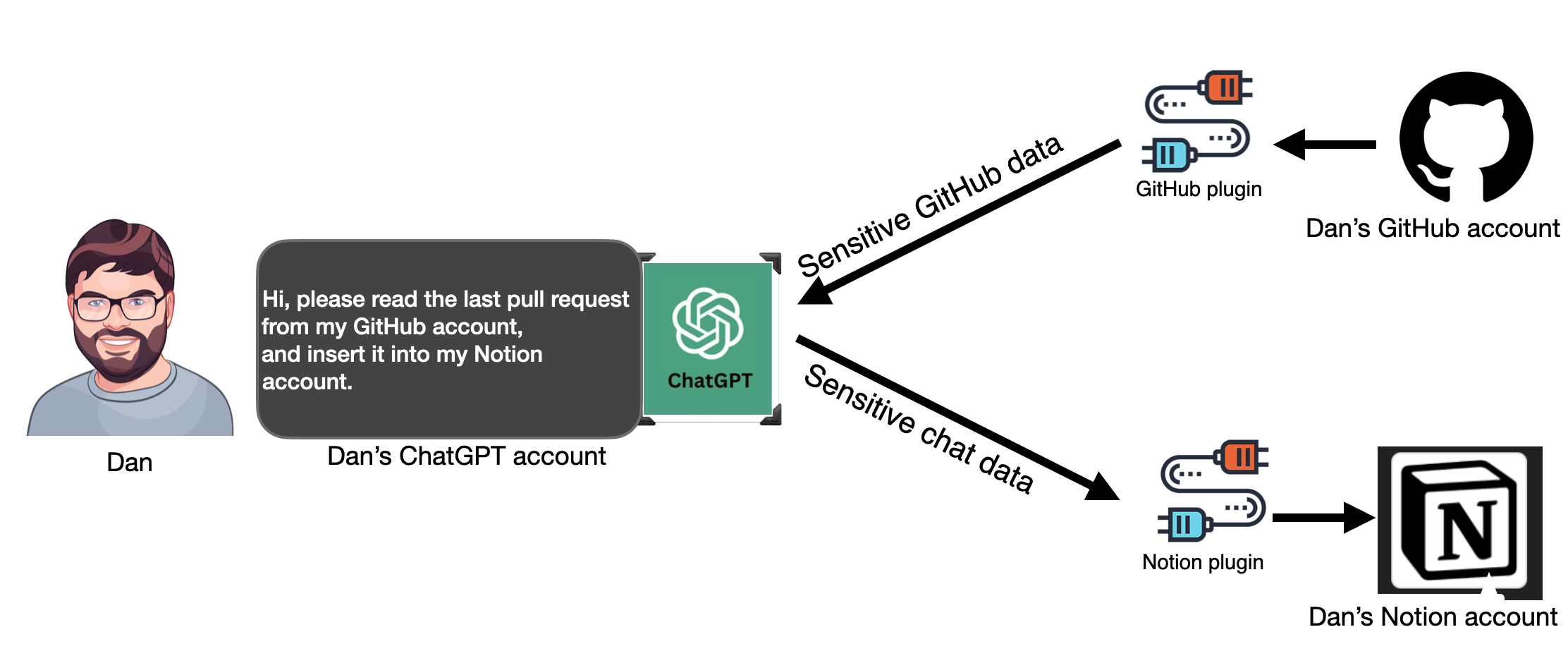
Additionally, researchers uncovered an OAuth redirection manipulation vulnerability that impacts various plugins, exemplified by an attack on the Charts plugin developed by Kesem AI. This exploit exploits user interaction to redirect OAuth authentication, potentially leading to unauthorized access to sensitive data.
Trending: Offensive Security Tool: SmuggleFuzz


