Browser Extension-Based Security Tool: FrogPost

Reading Time: 3 Minutes
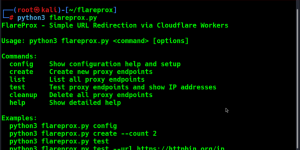
FrogPost: postMessage Security Testing Tool
FrogPost, developed by thisis0xczar, is a Chrome extension for testing and analyzing the security of postMessage communications between iframes. It helps developers and security professionals identify vulnerabilities in message-handling implementations.
Key Features
- Live monitor of cross-origin postMessage traffic
- Automatic detection and analysis of message handlers
- Static and runtime analysis for DOM-based vulnerabilities
- Identification of missing origin checks and unsafe sinks
- Targeted fuzzing of insecure handlers
- Detailed security reports with payload suggestions
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Usage Highlights
- Observe: Load any site with iframes. FrogPost captures postMessage exchanges.
- Analyze: Click ▶ to begin handler analysis. Static fallback analysis is applied if runtime fails.
- Trace: Use ✨ to trace data flows, detect DOM sinks, and generate security payloads.
- Fuzz: Launch 🚀 to test vulnerable endpoints using crafted fuzzing payloads.
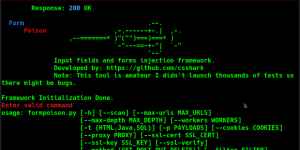
Dashboard at a Glance
Per-Iframe Controls
- Play – Start handler detection and capture
- Trace – Static sink and flow analysis
- Report – Show results & recommendations
- Launch – Begin fuzzing vulnerable handlers
General Controls
- Check All – Analyze all endpoints
- Clear Messages – Reset state and logs
- Export – Download captured messages
- Refresh – Manually update messages
- Debug Toggle – Verbose logging in console
Message Controls
- → Send to Origin – Replay to sender
- → Send to Destination – Replay to receiver
Panels
- Hosts Panel – Shows the main page and iframe connections
- Messages Panel – Intercepted postMessage traffic
- Security Report – DOM XSS and origin check findings
See Also: Offensive Security Tool: HExHTTP
Installation Guide for macOS
Option 1 (Recommended): Install the Chrome Extension via setup.sh
Clone the repository:
git clone https://github.com/thisis0xczar/FrogPost.git
Load the extension in Chrome.
cd to the repo folder:
cd FrogPost
Make setup.sh executable and run it:
chmod +x setup.sh; ./setup.sh
Option 2: Install the Chrome Extension manually
Clone the repository:
git clone https://github.com/thisis0xczar/FrogPost.git
Go to chrome://extensions/ in Chrome
Enable Developer mode
Click Load unpacked and select the FrogPost directory
Extension should appear in Chrome
Step 2: Set Up the Native Messaging Host
Create required directories:
mkdir -p ~/Library/Application\ Support/NodeServerStarter
mkdir -p ~/Library/Application\ Support/Google/Chrome/NativeMessagingHosts
Copy your Chrome Extension ID and update com.nodeserver.starter.json:
sed -i '' 's/\abcdefghijklmnopabcdefghijklmnop//g' com.nodeserver.starter.json
Verify allowed_origins includes:
"chrome-extension://(your-extension-id)/"
In server.js, set:
const rootDir = '/Path/To/extension/folder';
In start_server.sh, set:
SERVER_JS="/Users/[USER_NAME]/Library/Application Support/NodeServerStarter/server.js" LOG_FILE="/Users/[USER_NAME]/Library/Application Support/NodeServerStarter/node-finder.log
Copy files to system paths:
cp /path/to/FrogPost/server.js ~/Library/Application\ Support/NodeServerStarter/
cp /path/to/FrogPost/start_server.sh ~/Library/Application\ Support/NodeServerStarter/
cp /path/to/FrogPost/com.nodeserver.starter.json ~/Library/Application\ Support/Google/Chrome/NativeMessagingHosts/
Confirm the JSON file is configured correctly:
cat ~/Library/Application\ Support/Google/Chrome/NativeMessagingHosts/com.nodeserver.starter.json
Install Node dependencies:
cd ~/Library/Application\ Support/NodeServerStarter/
npm install express cors body-parser
Troubleshooting
- Could not connect to fuzzer server: Recheck file paths
- Permission issues: Run chmod 755 on all scripts
- Node not found: Ensure it’s installed and available in your $PATH
- Extension not loading: Use Chrome dev tools or reload
Disclaimer
Use FrogPost ethically and legally — only test applications you own or have permission to assess. Unauthorized testing may violate laws.
Clone the repo from here: GitHub Link