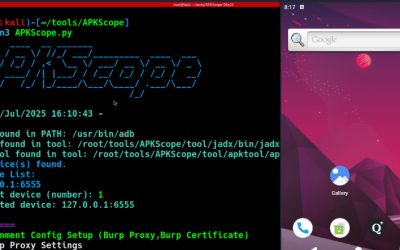
Offensive Security Tool: APKScope
APKScope is a tool designed to simplify the security analysis of Android applications. It integrates with popular tools such as ADB, Frida, Drozer, Jadx, and Apktool.
Offensive Security Tool: Cybersecurity AI (CAI)
Cybersecurity AI (CAI) is an open-source, agent-based, and modular AI framework purpose-built to automate and augment cybersecurity testing workflows using Large Language Models (LLMs) and pluggable tools. It supports both offensive and defensive operations. It’s designed for ethical hackers, red teamers, CTF players, and security researchers aiming to integrate AI into bug bounty, penetration testing, exploit development, and reporting workflows.
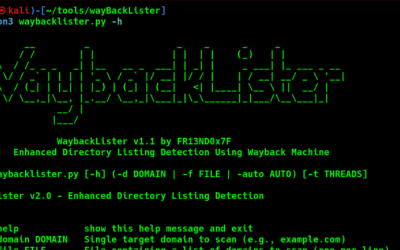
Recon Tool: WaybackLister
WaybackLister is a reconnaissance tool designed for web application penetration testers, red teamers, and bug bounty hunters. It automates the discovery of potentially exposed directory listings on web servers by leveraging historical data from the Wayback Machine (archive.org).
OSINT Tool: GoogleDorker
GoogleDorker is a tool designed for ethical hackers, bug bounty hunters, and penetration testers. It automates and enhances the process of Google Dorking—a technique that uses advanced Google search operators to find sensitive information exposed on the internet.
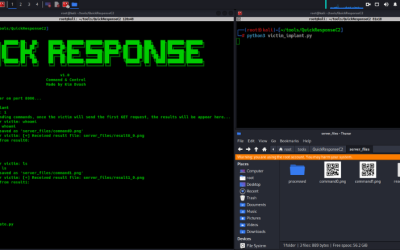
Offensive Security Tool: QuickResponseC2
QuickResponseC2 is a highly covert Command and Control (C2) framework and it operates by leveraging QR codes and HTTP(S) for indirect communication between an attacker and a compromised system.
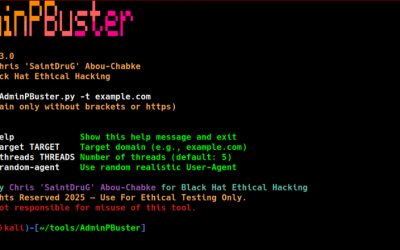
Recon Tool: AdminPBuster (Admin Panel Buster)
AdminPBuster identifies hidden admin panels for any domain using a built-in wordlist that includes both common and obscure paths, effectively bypassing WAFs.
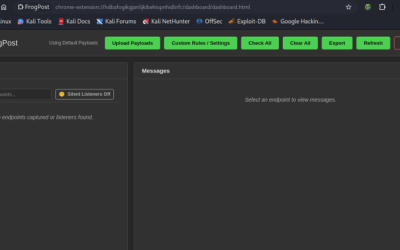
Browser Extension-Based Security Tool: FrogPost
FrogPost is a Chrome extension for testing and analyzing the security of postMessage communications between iframes. It helps developers and security professionals identify vulnerabilities in message-handling implementations.
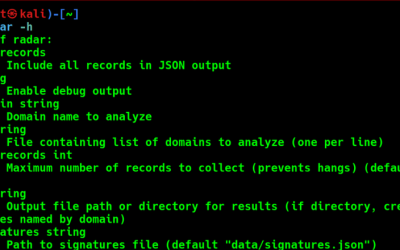
Recon Tool: RADAR
RADAR (Rapid Assessment of DNS And Reconnaissance) is an advanced DNS reconnaissance tool designed to identify technologies and services used by domains through their DNS footprints.
Recon Tool: spoof_checker
spoof_checker is a tool designed to identify misconfigurations in email authentication mechanisms and check for subdomain takeover vulnerabilities.