Offensive Security Tool: smugglo
Reading Time: 3 Minutes
smugglo
smugglo, developed by b3rito, is an HTML smuggling tool that creates self-contained malicious HTML payloads designed to bypass content filters and EDR/AVs by embedding binary files into an HTML page that auto-drops the payload when opened in a browser. It leverages trusted browser environments to exfiltrate or deploy binaries, evading network inspection tools.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Features
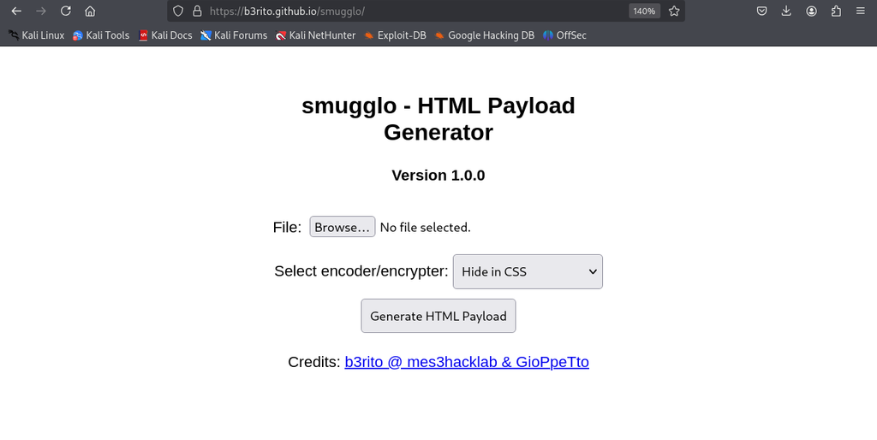
- One-file payload: Wrap any file into a single self-contained HTML file
- Automatic extraction: The generated HTML auto-extracts and downloads the file when opened (no clicks needed)
- Data hiding options: Supports XOR obfuscation, AES-GCM encryption, Base64 or hex encoding to conceal content
- Stealth injection: Option to stash file data in CSS variables for extra sneakiness
- Bypass filters: Slip past content filters and sandboxes by masquerading as a harmless HTML page (classic HTML smuggling trick)
See Also: Offensive Security Tool: HExHTTP
How it Works
- Select a file: Use the file input to choose any file from your system.
- Choose a method: Pick one of the embedding methods:
- CSS Encoding
- XOR Encryption
- AES Encryption
- Base64 Encoding
- Hex Encoding
- Generate HTML: Click the button and smugglo wraps your file into a self-contained HTML file.
- Automatic Extraction: When the HTML payload is opened in a browser, it automatically decodes/decrypts the embedded file and triggers its download.
Live Demo
Try smugglo directly in your browser:
Clone the repo from here: GitHub Link