Bluetooth Bugs in Sony, Bose, JBL Devices Could Let Hackers Spy or Place Calls

Researchers have disclosed three Bluetooth vulnerabilities in Airoha chipsets, widely used in wireless audio products from ten major vendors, enabling potential eavesdropping, data theft, and command injection attacks.
Uncovered by cybersecurity firm ERNW and presented at the TROOPERS conference in Germany, the flaws impact 29 devices—including headphones, earbuds, wireless mics, and speakers—from brands like Bose, Sony, Beyerdynamic, JBL, Jabra, Marshall, JLab, Teufel, EarisMax, and MoerLabs.
The Vulnerabilities
The three flaws reside in Airoha’s Bluetooth system-on-chip (SoC) firmware, specifically targeting True Wireless Stereo (TWS) functionality:
- CVE-2025-20700 (CVSS 6.7 – Medium): Missing authentication in GATT services
- CVE-2025-20701 (CVSS 6.7 – Medium): Missing authentication in Bluetooth BR/EDR
- CVE-2025-20702 (CVSS 7.5 – High): Flaws in a custom protocol that enables dangerous capabilities
Using a proof-of-concept exploit, researchers demonstrated they could:
- Read currently playing media
- Hijack Bluetooth connections
- Issue HFP (Hands-Free Profile) commands, such as initiating or answering calls
- Extract Bluetooth link keys, allowing access to call history and contacts
- Eavesdrop on phone conversations
- Potentially rewrite device firmware for remote code execution and worm-like propagation
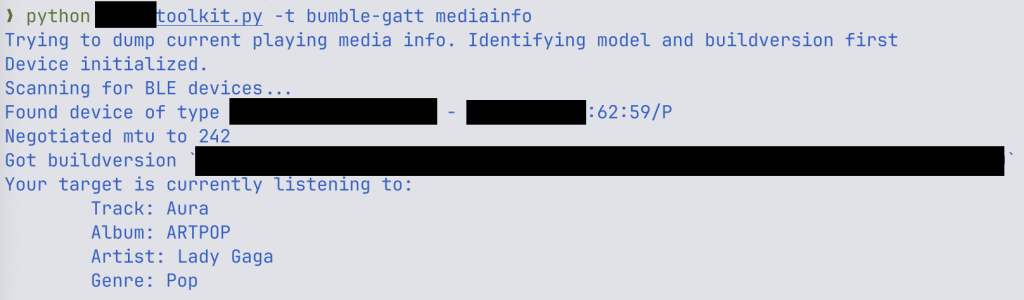 Reading currently played song from a vulnerable Airoha device
Reading currently played song from a vulnerable Airoha device
source: ERWN
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Attack Feasibility
While the implications are severe, real-world exploitation is difficult:
- Requires close physical proximity (Bluetooth range)
- Demands advanced technical skill
- Limited primarily to high-value targets (e.g., diplomats, journalists, executives)
“Yes — technically, it is serious. But real attacks are complex to perform,” said ERNW researchers.
Response & Mitigation
- Airoha has released an updated SDK with patches addressing all three vulnerabilities.
- However, many vendors had not yet incorporated these fixes as of May 27, 2025, according to German publication Heise.
- Firmware updates must be issued by each affected vendor before end users are protected.
Trending: Using Favicon for OSINT
Recommendations
- Users: Check for firmware updates from device manufacturers and apply them immediately.
- Enterprises & high-risk individuals: Consider avoiding affected models or disabling Bluetooth when not in use.
- Vendors: Urgently push patched firmware based on the updated Airoha SDK.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













