ClickFix Malware Campaign Now Hits Linux

APT36 Launches Cross-Platform ClickFix Attacks, Now Targeting Linux Users
The threat group known as APT36 (aka Transparent Tribe) has launched a new ClickFix campaign targeting all major desktop operating systems—Windows, Linux, and macOS—with tailored social engineering techniques to deliver malware.
What is ClickFix?
ClickFix is a social engineering technique that tricks users into manually executing malicious commands via Run dialogs or terminal windows. These attacks often masquerade as application errors, CAPTCHAs, or verification prompts, leading unsuspecting users to run malware payloads themselves.
ClickFix attacks have previously been observed targeting Windows users, often prompting them to run PowerShell or MSHTA commands that lead to info-stealers or ransomware infections. In 2024, similar tactics expanded to macOS, using fake Google Meet errors to deliver malware.
New Linux-Focused Attack Flow
In a new campaign observed by Hunt.io, APT36 is now leveraging ClickFix against Linux users. The threat actors are using a malicious website impersonating India’s Ministry of Defence, with a fake press release used as bait.
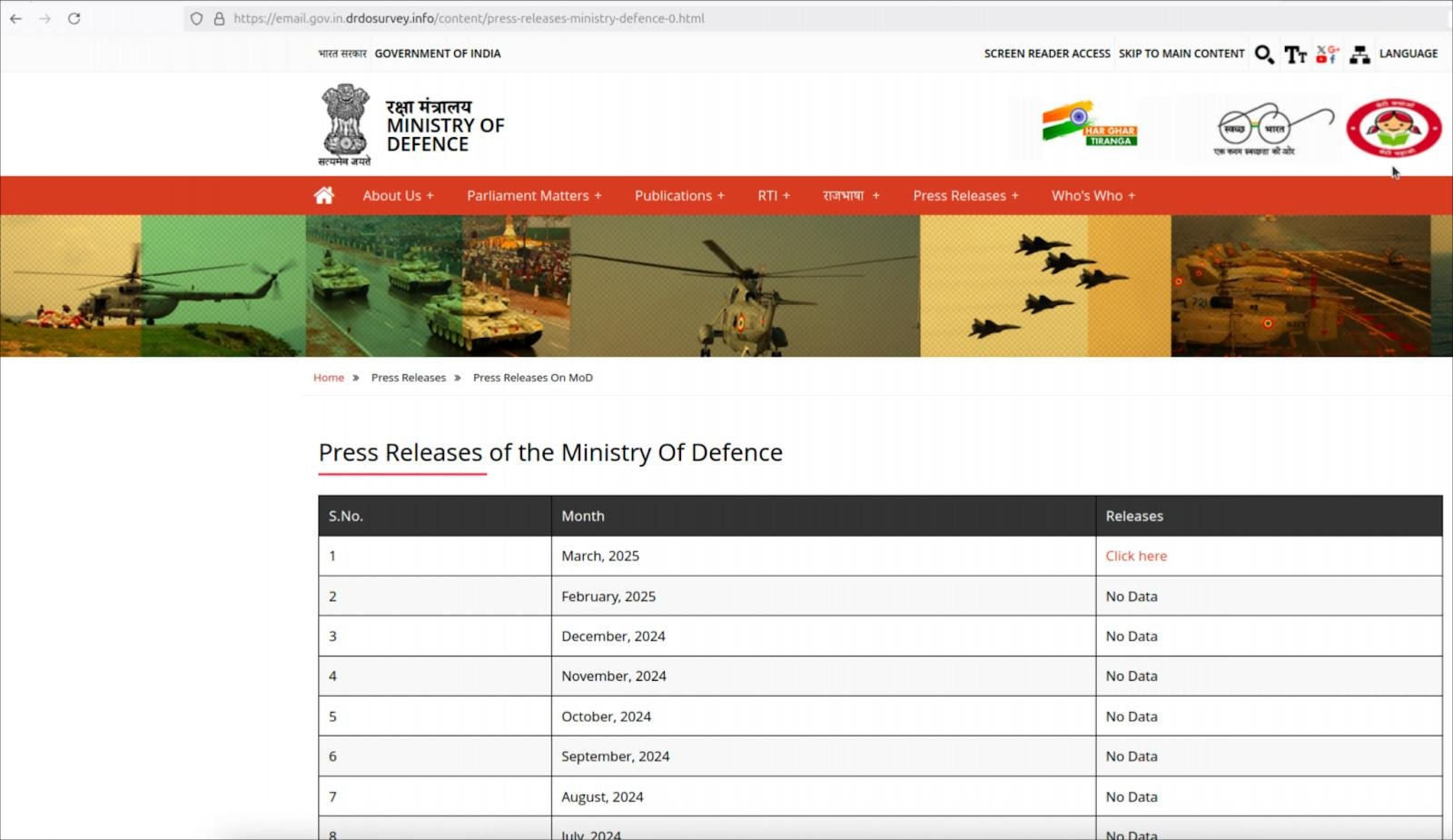 Malicious website mimicking India’s Ministry of Defence
Malicious website mimicking India’s Ministry of Defence
Source: Hunt.io
Once a visitor lands on the site, their operating system is fingerprinted to serve a tailored attack path:
Windows users are redirected to a full-screen warning about content restrictions. Clicking “Continue” copies a malicious MSHTA command to the clipboard, which the user is instructed to paste into a terminal window. This command runs a .NET loader, displaying a decoy PDF while silently connecting to a command-and-control (C2) server.
Linux users see a CAPTCHA page that copies a shell command to their clipboard after clicking the “I’m not a robot” button. The victim is then instructed to open the Run dialog (ALT+F2), paste the command, and execute it.
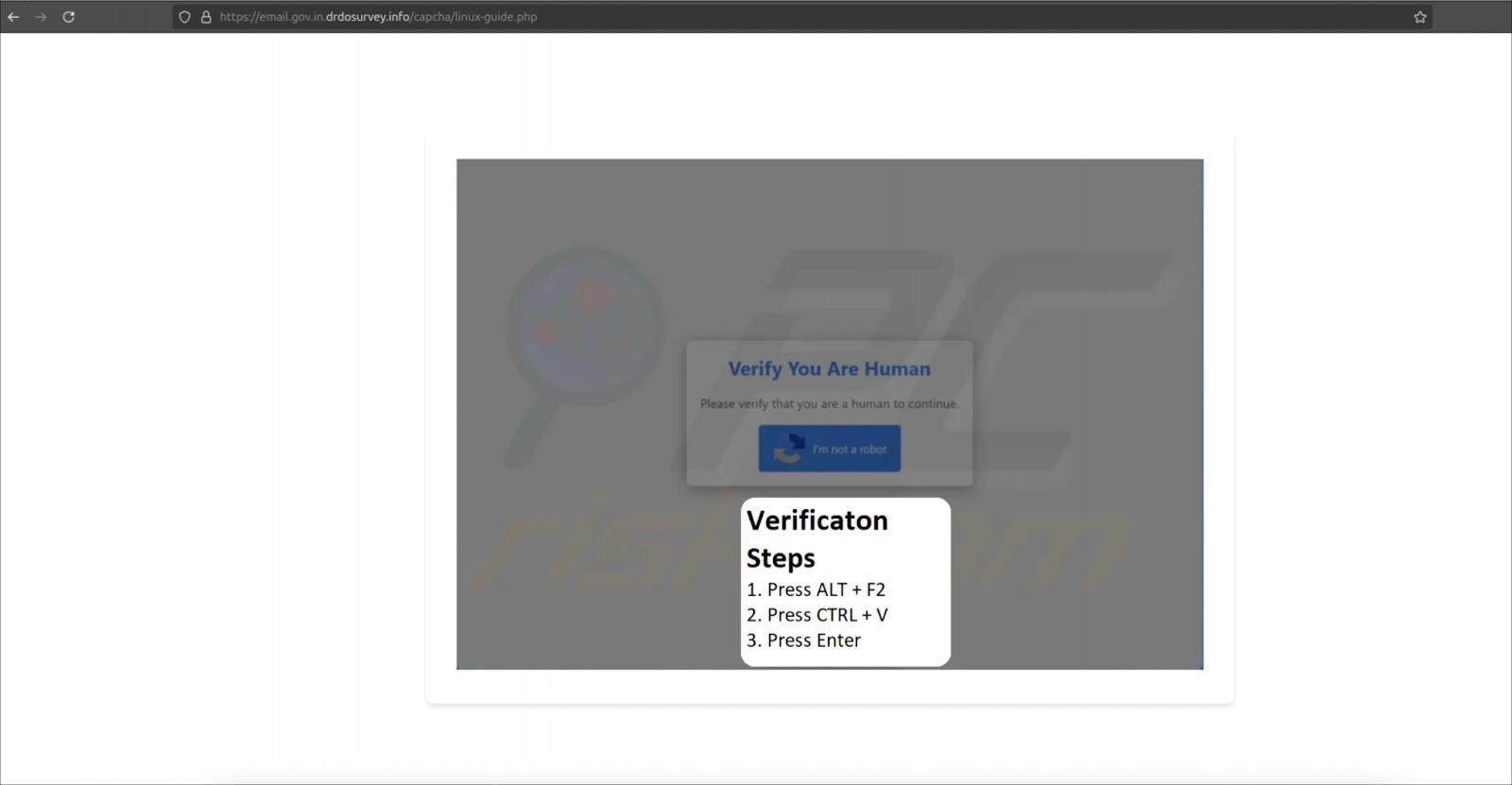 Instructions for Linux users
Instructions for Linux users
Source: Hunt.io
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Technical Breakdown
For Linux targets, the current attack command drops a shell script named mapeal.sh, which:
Downloads a JPEG image from the attacker-controlled domain
trade4wealth[.]inOpens the image in the background
Hunt.io researchers emphasize that no persistence, lateral movement, or data exfiltration was observed, suggesting that APT36 may be testing the effectiveness of this infection chain before deploying active payloads.
“The script downloads a JPEG image from the same trade4wealth[.]in directory and opens it in the background,” noted Hunt.io.
“No additional activity was observed during execution.”
Nonetheless, replacing the image with a weaponized script is trivial and may be a matter of timing.
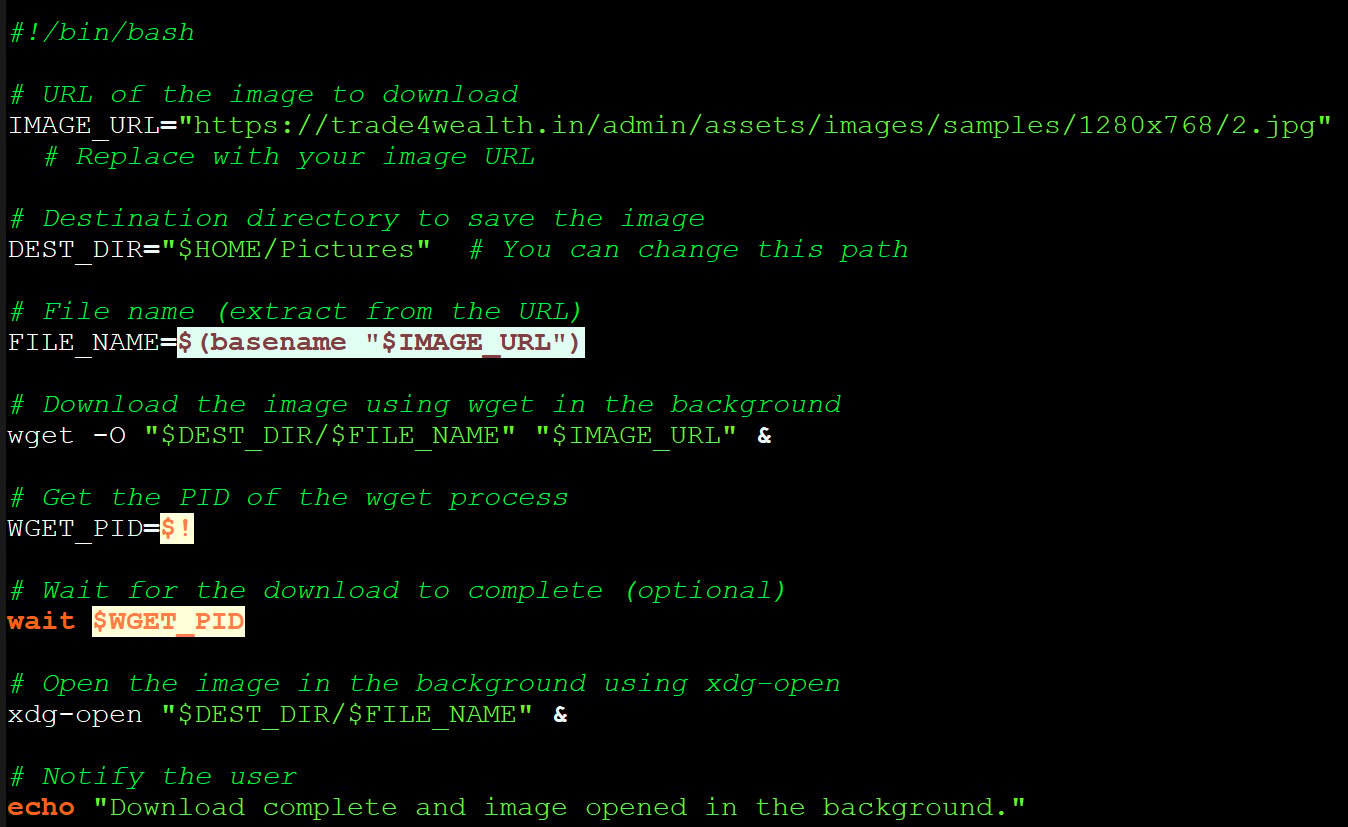 Linux ClickFix script
Linux ClickFix script
Source: BleepingComputer
Implications
This expansion to Linux is a clear sign of the evolution and growing versatility of ClickFix tactics. By adapting social engineering strategies to each OS’s user behavior, attackers increase their chances of infection—especially against less technically aware users on platforms typically considered secure.
APT36 continues to focus its campaigns around Indian government targets and infrastructure, using legitimate-looking websites and localized lures to improve the credibility of their attacks.
Trending: Offensive Security Tool: QuickResponseC2
Recommendations
Do not paste commands from unfamiliar websites into Run dialogs or terminals—even if they appear to come from official sources.
System administrators should warn users, especially in high-risk sectors, about these types of attacks.
Use endpoint detection and response (EDR) and web filtering solutions that can detect or block suspicious clipboard activity and malicious domains.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com