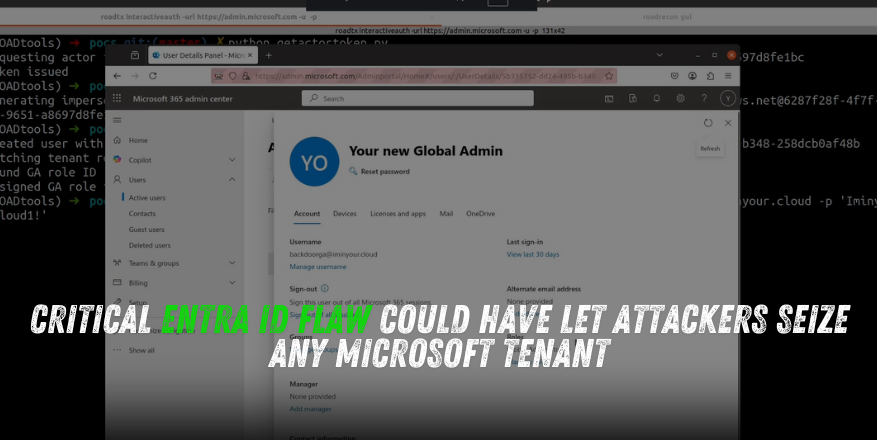
Critical Entra ID Flaw Could Have Let Attackers Seize Any Microsoft Tenant
What happened
A pair of legacy components in Microsoft’s cloud identity stack combined to create a critical privilege-escalation vector that could have allowed an attacker to gain Global Admin privileges in any Microsoft Entra ID tenant. The issue was discovered and responsibly disclosed by security researcher Dirk-jan Mollema.
The dangerous combination: actor tokens + Azure AD Graph bug
The root cause was twofold:
- Undocumented “actor tokens”—short-lived impersonation tokens issued by an older Access Control Service used for internal service-to-service communication—lack signatures and normal protections, and are not logged or revocable in the same way as standard tokens.
- The legacy Azure AD Graph API (graph.windows.net) had a validation bug (now tracked as CVE-2025-55241) that failed to correctly validate the tenant origin of requests, meaning an actor token from one tenant could be accepted for operations in another tenant.
Combined, these weaknesses let an attacker craft an impersonation token that the Graph API accepted for a victim tenant—effectively bypassing conditional access, MFA, and tenant-level logging.
Offensive Security, Bug Bounty Courses
How an attacker could have abused it
Mollema demonstrated a short attack chain that, in practice, would require only publicly discoverable information plus the actor token:
- Generate an actor token from an attacker-controlled tenant (no logs recorded in the victim tenant).
- Determine the target tenant ID (public) and the netId of a user in that tenant.
- Submit the crafted token to the Azure AD Graph API; use it to list admins, impersonate a Global Admin, and perform read/write actions (create accounts, reset credentials, change roles).
Because Graph API calls were the only actions that would show up in victim-tenant telemetry, many of the earlier steps (token issuance and crafting) left little or no trace.
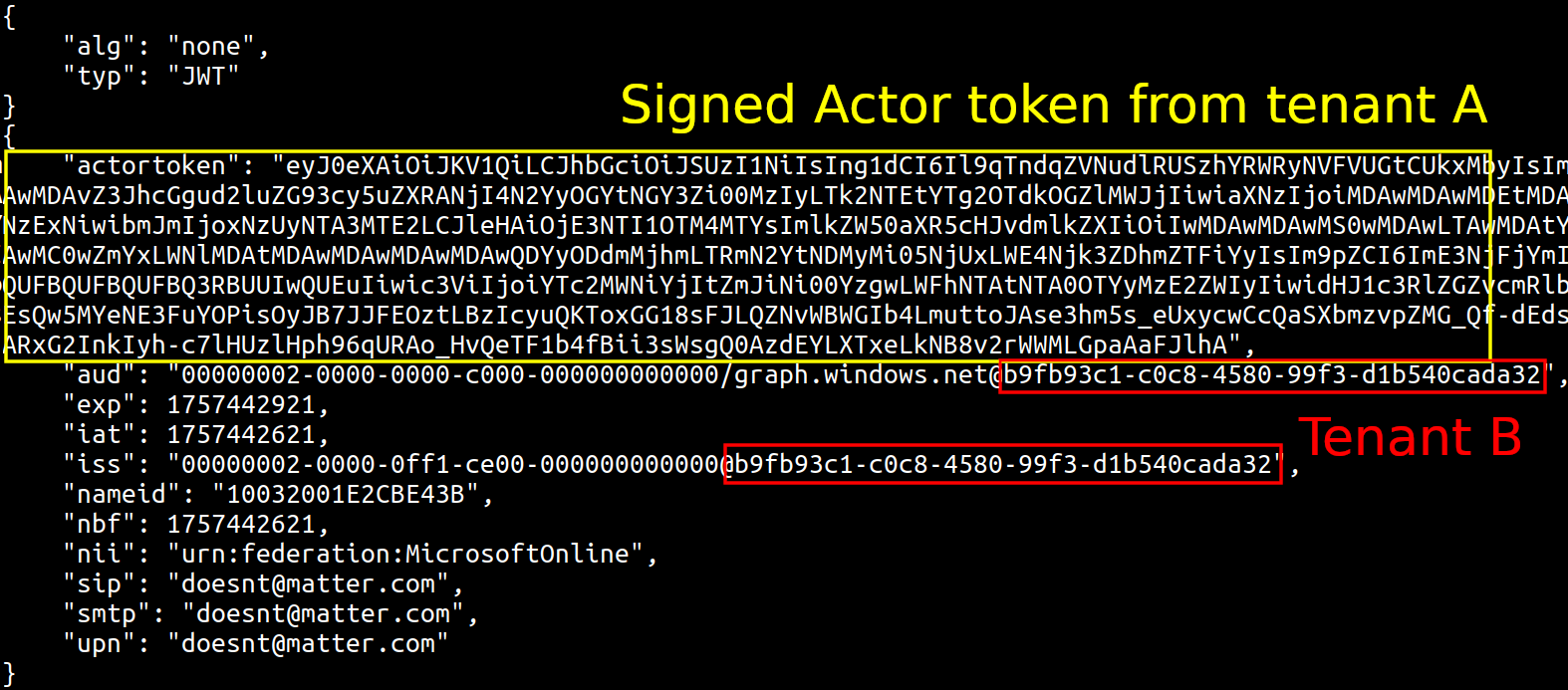
source: https://dirkjanm.io/obtaining-global-admin-in-every-entra-id-tenant-with-actor-tokens/
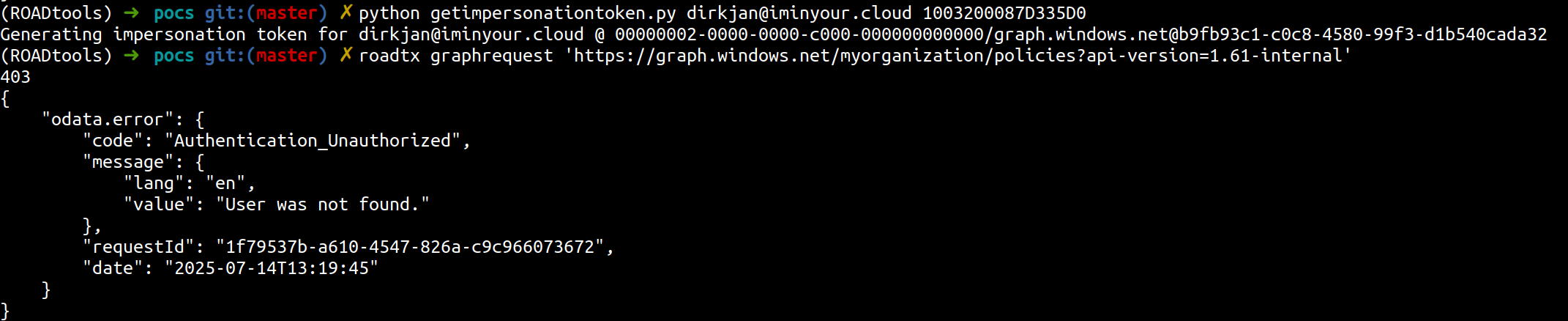
source: https://dirkjanm.io/obtaining-global-admin-in-every-entra-id-tenant-with-actor-tokens/
Impact and scope
If exploited in the wild, the vulnerability could have allowed full tenant compromise—exfiltrating user and admin lists, modifying roles and policies, and gaining access to any downstream services relying on Entra ID (Exchange Online, SharePoint, Microsoft 365, third-party SaaS integrated via Entra, etc.). Multiple outlets characterized the flaw as exceptionally severe and likened its potential impact to major past cloud identity incidents.
Trending: Offensive Security Tool: RingReaper
Microsoft’s response and timeline
Mollema reported the issue in mid-July 2025; Microsoft investigated and implemented fixes rapidly, applying mitigations across the cloud and restricting the problematic actor token usage. Microsoft confirmed remediation and later assigned CVE-2025-55241 and published follow-up guidance. Public reporting indicates Microsoft applied fixes in July with CVE assignment and public disclosure following in September.
Microsoft says it found no evidence the flaw was abused in the wild during its investigation
Defenses and recommendations
Organizations should assume patching and vendor mitigations are necessary but not always sufficient—recommended actions include:
- Verify your Microsoft tenancy is running the latest Entra ID protections and confirm Microsoft’s mitigations have been applied.
- Audit privileged roles and remove unnecessary Global Admins; enable Just-In-Time / Just-Enough Admin controls where possible.
- Enhance telemetry: push for API-level logging, centralized SIEM collection, and cross-tenant alerting to detect anomalous Graph API activity.
- Enforce strong conditional access and external review of legacy integrations that may rely on old tokens or deprecated APIs (noting Microsoft’s deprecation of Azure AD Graph in favor of Microsoft Graph).
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com, dirkjanm.io













