Google Recovery Bug Allowed Brute-Force of User Phone Numbers

Critical Google Phone Number Disclosure Flaw Exposed Millions to SIM Swap and Phishing Risks
Key Takeaways
- A now-deprecated Google account recovery endpoint leaked full recovery phone numbers.
- The attack required only a user’s Google profile name and a partial phone number—easily obtained through recovery hints or third-party services.
- The vulnerability posed a significant risk for phishing, vishing, and SIM-swapping attacks.
- Discovered by BruteCat, the researcher behind the February 2025 YouTube email address leak.
- Google patched the issue on June 6, 2025, after classifying it as a medium-severity vulnerability.
Overview of the Exploit
Security researcher BruteCat uncovered a legacy JavaScript-disabled version of Google’s username recovery form that lacked adequate rate-limiting and CAPTCHA protection.
This exposed endpoint allowed attackers to brute-force Google recovery phone numbers tied to any Google account—essentially enabling anyone to uncover users’ personal numbers using automated tooling.
Technical Breakdown
Legacy Endpoint Exploited
An old version of Google’s recovery form (JS-disabled) was still accessible. It permitted recovery queries using a display name and partial phone number.Bypassing Rate Limiting
BruteCat used IPv6 address rotation (/64 subnet trick) to send trillions of unique requests, circumventing basic anti-abuse protections.Bypassing CAPTCHA (BotGuard)
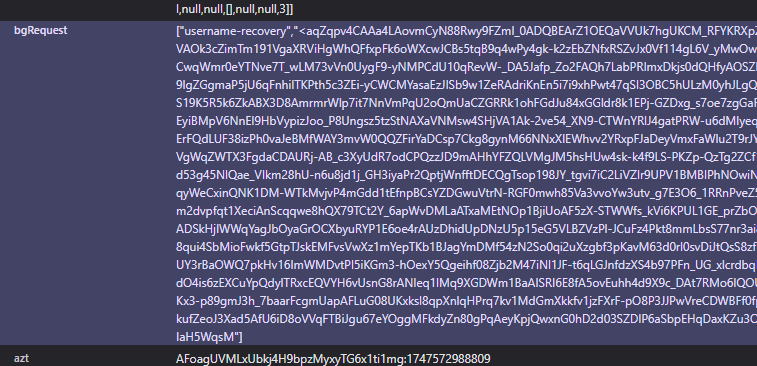
CAPTCHA was bypassed using a valid BotGuard token harvested from the modern, JS-enabled version of the form. Tokens were generated with headless Chrome and reused in brute-force requests.
Captured BotGuard token from a Google JS-enabled username recovery form
Source: BruteCatPhone Number Enumeration
Used Google’s libphonenumber to format numbers by region.Created a “country mask” database to streamline attack.Brute-force speeds:
- US: ~20 minutes
- UK: ~4 minutes
- Netherlands: ~15 seconds
.jpg) Time to brute-force phone numbers
Time to brute-force phone numbers
Source: BruteCat
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Target Identification Process
To tie a number to a specific account:
- Looker Studio Trick
Transferred ownership of a document to the victim’s Gmail address. Once accepted, the profile name was revealed. - Recovery Hint Abuse
Used partial numbers shown in Google’s own recovery flow (e.g., +1•••••1779), and supplemented with other services like PayPal that show more digits.
Combined, this allowed a near-complete number reconstruction for targeting.
Real-World Implications
This vulnerability could have enabled:
- SIM swap attacks to intercept 2FA codes
- Phishing and vishing campaigns targeting known users
- Identity theft through account takeovers
BruteCat emphasized the severity: attackers could extract full phone numbers from just a name and two digits.
Remediation Timeline
| Date | Action |
|---|---|
| April 14, 2025 | BruteCat reports the vulnerability to Google |
| May 22, 2025 | Google upgrades severity to medium and begins mitigations |
| June 6, 2025 | Google fully deprecates the vulnerable JS-disabled endpoint |
- Google awarded $5,000 via its Vulnerability Reward Program (VRP).
- The issue is no longer exploitable.
- It’s unclear if the vulnerability was abused before being reported.
Trending: Recon Tool: WaybackLister
Recommendations for Users
Although the issue is patched, users should:
- Review recovery methods and remove old phone numbers or email addresses
- Use authenticator apps instead of SMS for 2FA
- Avoid using the same display name across services
- Be cautious with recovery hints from third-party platforms
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com