New ClickFix Campaign “EVALUSION” Deploys Amatera Stealer and NetSupport RAT
Overview of the EVALUSION Campaign
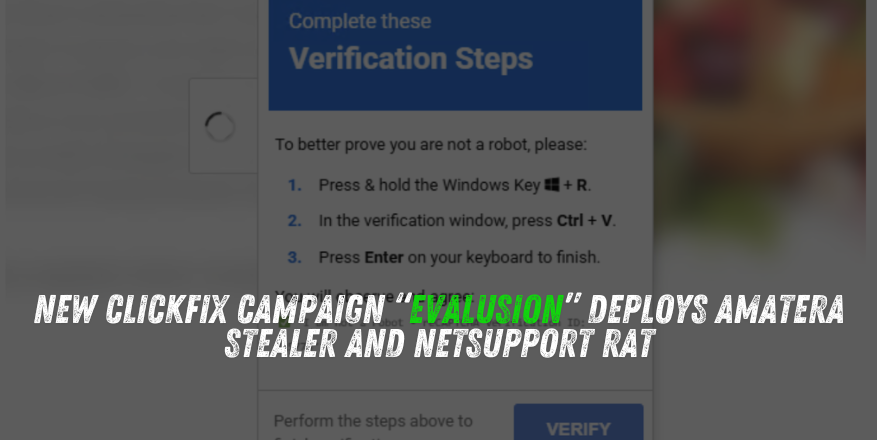
Cybersecurity researchers have uncovered a new wave of ClickFix-style malware attacks delivering both Amatera Stealer and NetSupport RAT, tracked by eSentire as EVALUSION.
ClickFix, a fast-growing social engineering tactic, lures victims into manually running malicious commands through the Windows Run dialog under the guise of bypassing a “reCAPTCHA verification.” This approach bypasses many automated security safeguards and has become a preferred tactic for numerous malware operators.
The latest activity has been observed throughout October 2025, marking a significant expansion in the distribution of Amatera Stealer — a successor to AcridRain (ACR) Stealer — and accompanying remote access tools.
Amatera Stealer: An Evolved MaaS Platform
First discovered in June 2025, Amatera Stealer is marketed via subscription plans ranging from $199/month up to $1,499/year, aligning with the rise of malware-as-a-service offerings.
Key features include:
- Extensive data theft capabilities targeting
- Crypto wallets
- Web browsers
- Messaging apps
- Email clients
- FTP clients
- Advanced evasion methods such as
- WoW64 SysCalls to bypass user-mode hooks used by AV, EDR, and sandboxes
- DLL payloads packed with PureCrypter, a crypter/loader also sold as a MaaS product
Once executed, the stealer DLL is injected into the legitimate MSBuild.exe process to steal credentials and sensitive information. It then issues PowerShell commands to download NetSupport RAT — but only if the victim appears valuable.
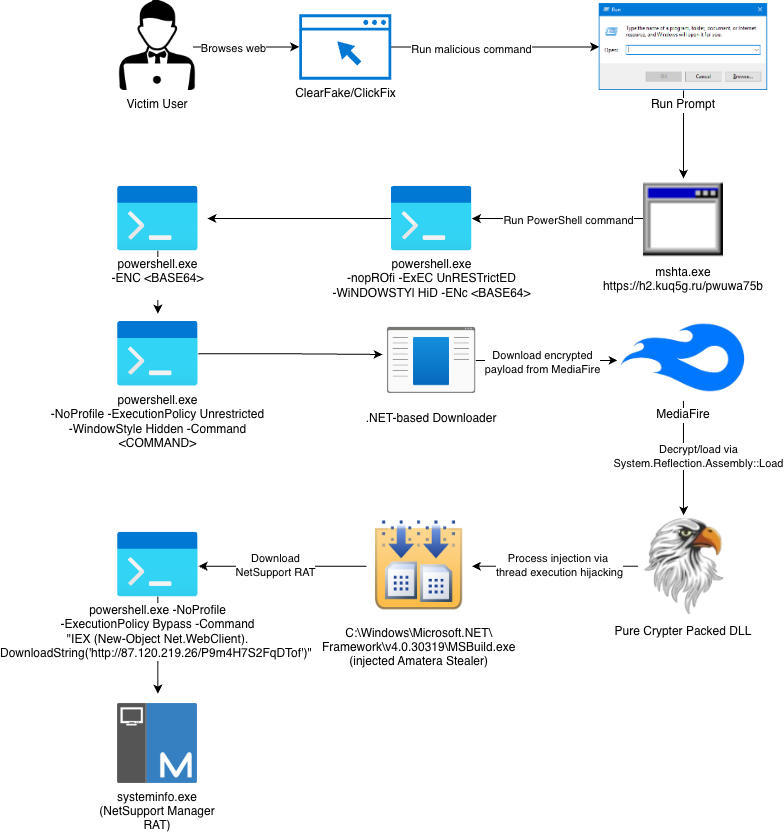 Figure 3 – Attack chain leading to Amatera and NetSupport RAT
Figure 3 – Attack chain leading to Amatera and NetSupport RAT
Offensive Security, Bug Bounty Courses
Targeting Logic: Only High-Value Victims Get NetSupport RAT
eSentire’s analysis highlights a clever filtering mechanism:
If the infected endpoint is not domain-joined and does not contain files of financial or operational value, Amatera does not download NetSupport RAT.
This avoids wasting resources and reduces noise that could alert defenders, focusing efforts on victims most likely to yield profit.
How the ClickFix Attack Works
The attack chain mirrors other ClickFix-driven campaigns:
- User is shown a fake CAPTCHA or Cloudflare Turnstile-style page.
- The page instructs them to open the Windows Run dialog and paste a command.
- Executing the command triggers mshta.exe, which runs a PowerShell loader.
- The loader fetches a .NET payload (typically from MediaFire).
- Amatera Stealer is installed, followed by NetSupport RAT (if the system is valuable).
This multi-stage flow allows EDR evasion while leveraging trusted Windows binaries (“living-off-the-land”).
Related Malware Campaigns Using ClickFix
eSentire and other vendors report a surge in ClickFix-enabled campaigns dropping a variety of malware:
1. XWorm via VBS Invoice Lures
- Malicious VBS attachments disguise themselves as invoices.
- A batch file invokes PowerShell to fetch and run XWorm.
2. SmartApeSG / HANEYMANEY / ZPHP
- Compromised websites inject malicious JavaScript.
- Victims are redirected to fake Cloudflare Turnstile checks that deliver NetSupport RAT.
3. Fake Booking.com CAPTCHA
- Hospitality sector targeted.
- Fake CAPTCHA pages instruct users to run PowerShell commands dropping credential stealers.
4. Email Delivery Notification Spoofs
- Fraudulent “blocked messages” prompts.
- Leads victims to credential-harvesting sites designed to siphon corporate logins.
Trending: Recon Tool: ZoomeyeSearch
Cephas & Tycoon 2FA: Evolving Credential Phishing Kits
A growing number of phishing kits also support ClickFix-style flows, including:
Cephas
- Emerged in August 2024
- Uses an unusual obfuscation technique that inserts random invisible Unicode characters
- Helps evade anti-phishing scanners and disrupts YARA detection
Tycoon 2FA
- Intercepts authentication flows to steal credentials and 2FA tokens
- Used in attacks against cloud services and corporate email accounts
Barracuda reports these kits are becoming increasingly stealthy and professionalized, lowering barriers for inexperienced attackers.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com, esentire.com/blog













