New Secure Boot Flaw Lets Attackers Install Bootkit Malware
Critical Secure Boot Vulnerability (CVE-2025-3052) Exposes Millions of PCs to Bootkit Attacks
Security researchers have uncovered a severe flaw that compromises Secure Boot—an essential security feature used by nearly every modern PC and server. Tracked as CVE-2025-3052, the vulnerability allows attackers to disable Secure Boot protections and install stealthy bootkits that persist across reboots.
Discovered in a Microsoft-Signed Utility
The vulnerability was discovered by Alex Matrosov, a researcher at Binarly, after analyzing a BIOS-flashing utility originally developed for rugged tablets. Although intended for specific hardware, the utility was signed with Microsoft’s trusted UEFI CA 2011 certificate, enabling it to run on any Secure Boot-enabled system.
The core issue lies in how the utility handles a writable NVRAM variable without validation. An attacker with administrative access can exploit this to tamper with memory before the operating system loads.
Vulnerability Circulating Since 2022
Binarly found that the affected utility had been in circulation since late 2022 and was uploaded to VirusTotal in 2024, where it was first detected by the company. Binarly reported the issue to CERT/CC on February 26, 2025.
On June 10, 2025, Microsoft addressed the issue during Patch Tuesday, not only mitigating the original vulnerability but also adding 13 additional related modules to the Secure Boot dbx revocation list after discovering they were similarly affected.
“The issue did not affect just a single module… but actually 14 different modules,” said Binarly.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
How CVE-2025-3052 Bypasses Secure Boot
The flaw enables attackers to overwrite a global variable called gSecurity2, which plays a critical role in enforcing Secure Boot via the Security2 Architectural Protocol. By setting this variable to zero, Secure Boot can be disabled altogether.
“By setting it to zero, we effectively disable Secure Boot, allowing the execution of any unsigned UEFI modules,” Binarly explained.
Once Secure Boot is disabled, attackers can deploy bootkits—malicious tools that load before the OS and can remain undetected by antivirus software or security tools. This opens the door for persistent malware, spyware, or even ransomware embedded at the firmware level.
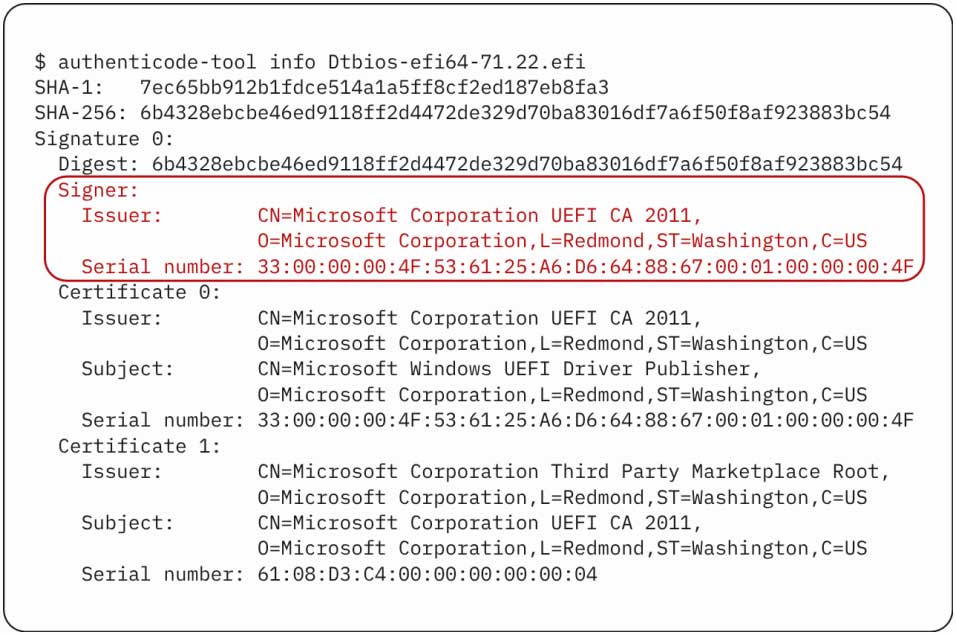 Vulnerable module signed with Microsoft UEFI CA 2011 certificate
Vulnerable module signed with Microsoft UEFI CA 2011 certificate
Source: Binarly
Microsoft Issues Fix — Urges Immediate Action
To mitigate the risk, Microsoft has released an updated Secure Boot dbx file that revokes the affected modules. Users are strongly advised to apply the latest updates immediately, especially those using Windows systems with Secure Boot enabled.
Binarly has released a demonstration video showing how their proof-of-concept exploit can disable Secure Boot and trigger a message before the OS loads, proving the seriousness of the flaw.
Trending: Recon Tool: WaybackLister
Second Secure Boot Vulnerability Also Revealed
Coinciding with the disclosure of CVE-2025-3052, another UEFI-related Secure Boot vulnerability, CVE-2025-4275, was also revealed. This flaw, discovered by Nikolaj Schlej and dubbed Hydroph0bia, affects Insyde H2O firmware and was patched following a standard 90-day disclosure timeline.
Both vulnerabilities underscore the growing threat posed by weaknesses in UEFI firmware and Secure Boot processes, and the increasing sophistication of attackers aiming to compromise systems at the deepest levels.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













