XZ-Utils Backdoor Still Found in 35+ Docker Hub Linux Images

The XZ-Utils backdoor, first discovered in March 2024, is still present in at least 35 Linux container images on Docker Hub, leaving users and organizations exposed to potential compromise.
Docker Hub is the main public registry for container images, widely used in CI/CD pipelines, developer environments, and production deployments. If a base image on Docker Hub contains malicious code, any container built on top of it inherits the same vulnerability.
Discovery of Infected Images
Security researchers at Binarly identified dozens of Docker images still affected by the CVE-2024-3094 XZ-Utils backdoor.
The malware was originally inserted into xz-utils versions 5.6.0 and 5.6.1, specifically targeting the liblzma.so library.
“Some of these compromised images are still publicly available on Docker Hub,” Binarly reported. “Even more troubling, other images have been built on top of these infected base images, making them transitively infected.”
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
How the Backdoor Works
The XZ-Utils backdoor hijacks the RSA_public_decrypt function in OpenSSH via glibc’s IFUNC mechanism.
If an attacker with a special private key connects over SSH to an affected system, they can bypass authentication and execute commands as root.
The malicious code was introduced by a long-time project contributor, “Jia Tan”, and shipped in official packages for Debian, Fedora, OpenSUSE, and Red Hat. This incident is considered one of the most severe open-source supply chain compromises of 2024.
Debian’s Controversial Response
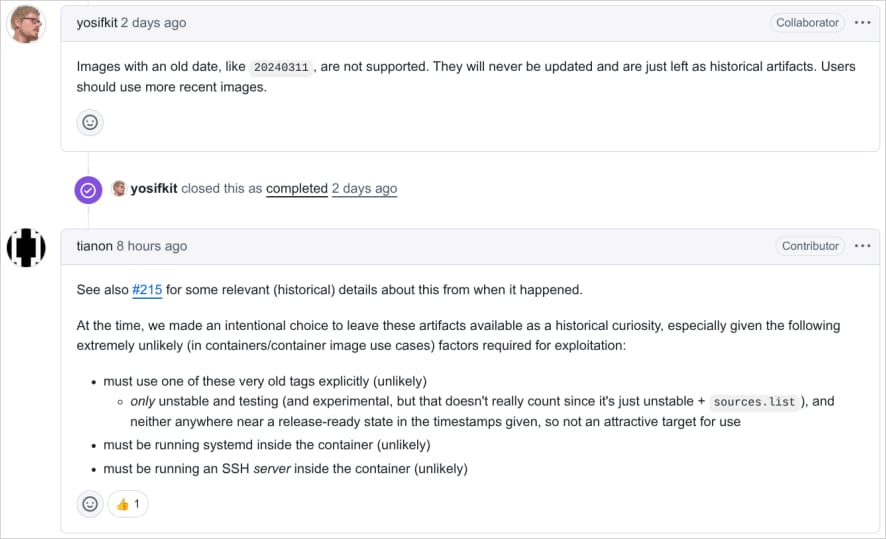
Despite the discovery, Debian maintainers chose not to remove the affected Docker images. They argue that:
- Exploitation would require sshd to be installed and running in the container.
- The attacker must have network access to the container’s SSH service.
- The attacker must possess the specific private key triggering the backdoor.
Debian maintains these images for archival purposes and advises users to only pull up-to-date images.
 Debian maintainer’s response
Debian maintainer’s response
Source: Binarly
Trending: Offensive Security Tool: APKScope
Binarly’s Warning
Binarly disagrees with Debian’s decision, stressing that publicly accessible infected images could still be accidentally pulled into production environments or automated build pipelines.
Their partial scan found over 35 infected images, but they warn the actual number is likely far higher since only a small fraction of Docker Hub was analyzed.
Mitigation
Users should verify their containers do not contain the affected versions of XZ-Utils:
- Safe versions: 5.6.2 or later (latest stable: 5.8.1)
- Detection: Use scanning tools from Binarly or Kaspersky.
- Best practice: Avoid using outdated images, especially from unverified sources.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













